DFIR & Malware Analysis homelab
I recently bought two physical servers and decided them to build a homelab for DFIR operations and Malware Analysis. I installed Proxmox on both and configured them into a single cluster.
Specs
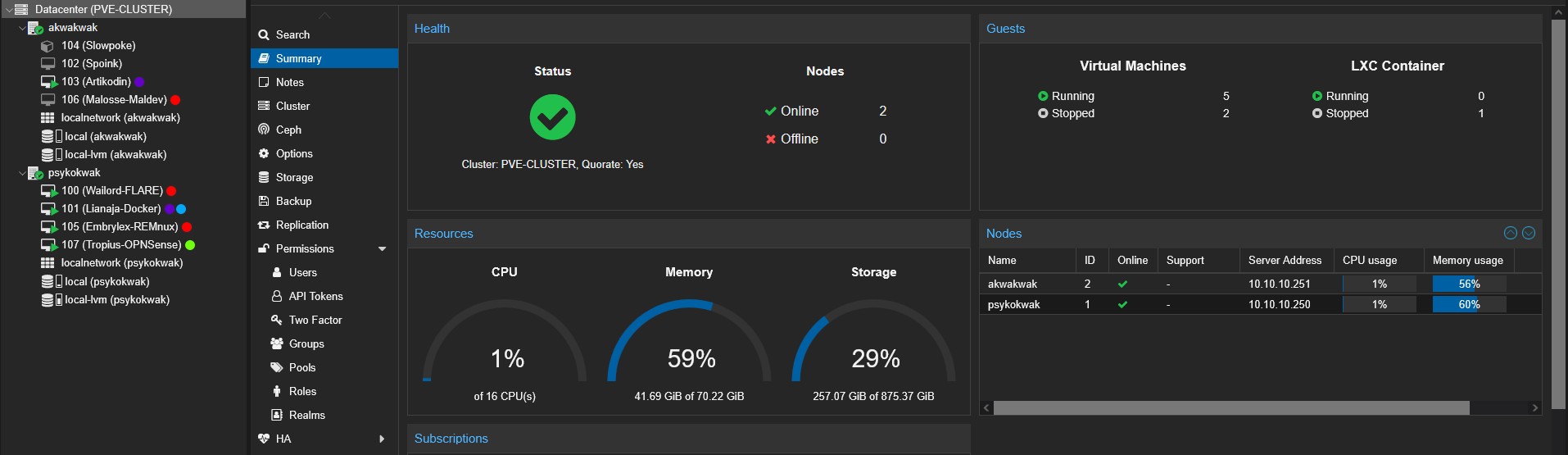
In the akwakwak node, I have 8G of memory and an 4 x Intel(R) Core(TM) i5-6500 CPU @ 3.20GHz. In the other hand, psykokwak node has 12 x Intel(R) Core(TM) i5-10505 CPU @ 3.20GHz with 64G of RAM.
Network configuration
I use three VLANs to separate traffic:
- VLAN 10: Home network (WAN)
- VLAN 20: LANDFIR (for forensics)
- VLAN 30: Malware analysis
I created a Linux bridge vmbr0 attached to the physical interface enp2s0
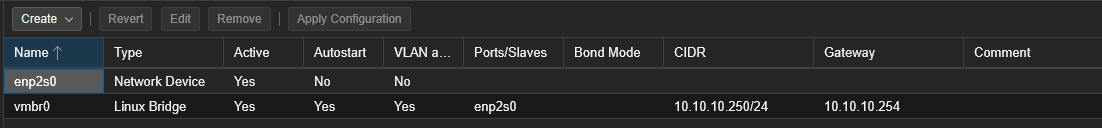
Enabled VLAN awareness on the bridge
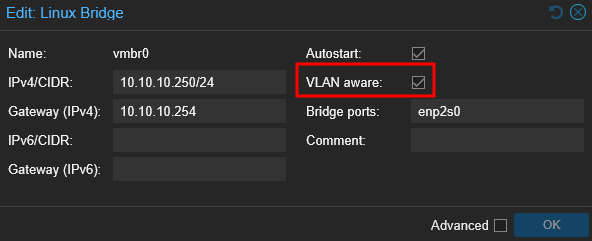
You can only attach one bridge per physical interface. That means:
1 vmbr = 1 physical NIC.
Then I tagged the network interface of my Malware Analysis VM for the VLAN 30 (MALWARE)
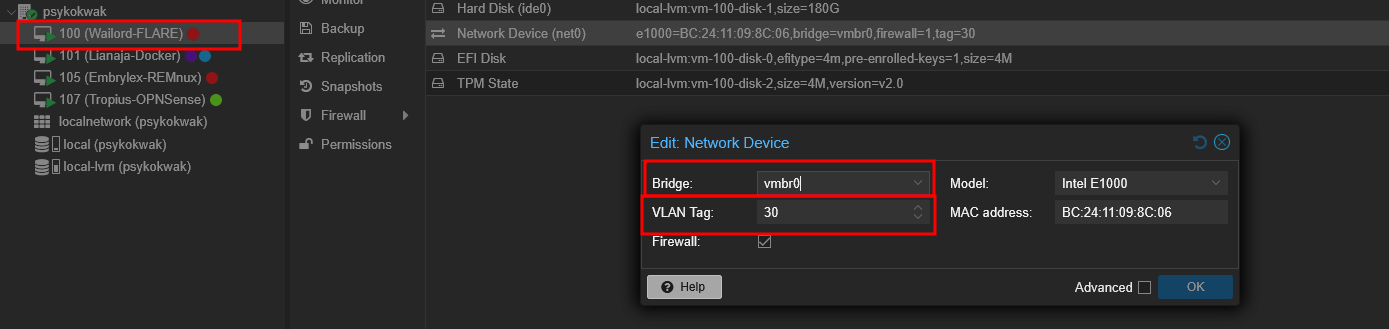
For each VM (FLAREVM, REMnux, etc.), I added the correct VLAN tag (e.g., VLAN 30 for malware analysis). I also connected OPNsense to all three VLANs by creating 3 virtual NICs, one for each VLAN.
For the initial install of OPNSense, I recommend connecting only the WAN interface (VLAN 10) to avoid confusion.
OPNSense
In order to separate the networks, I installed an OPNSense iso here
Interfaces
Once the install is done, you can access the webGUI and then assign interfaces
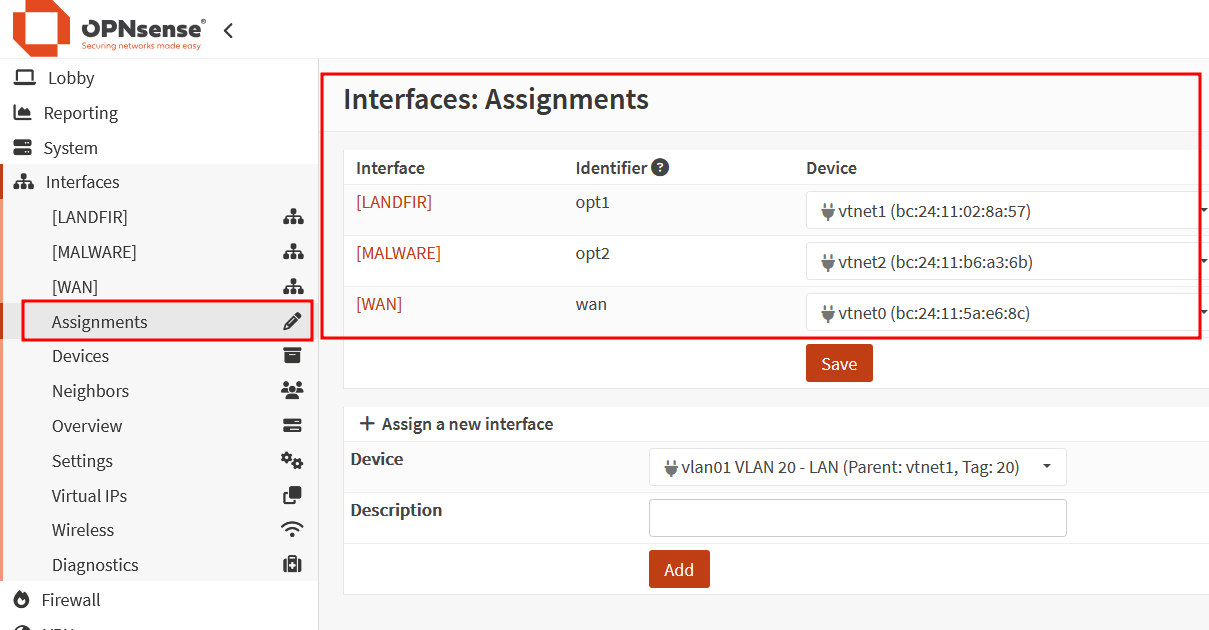
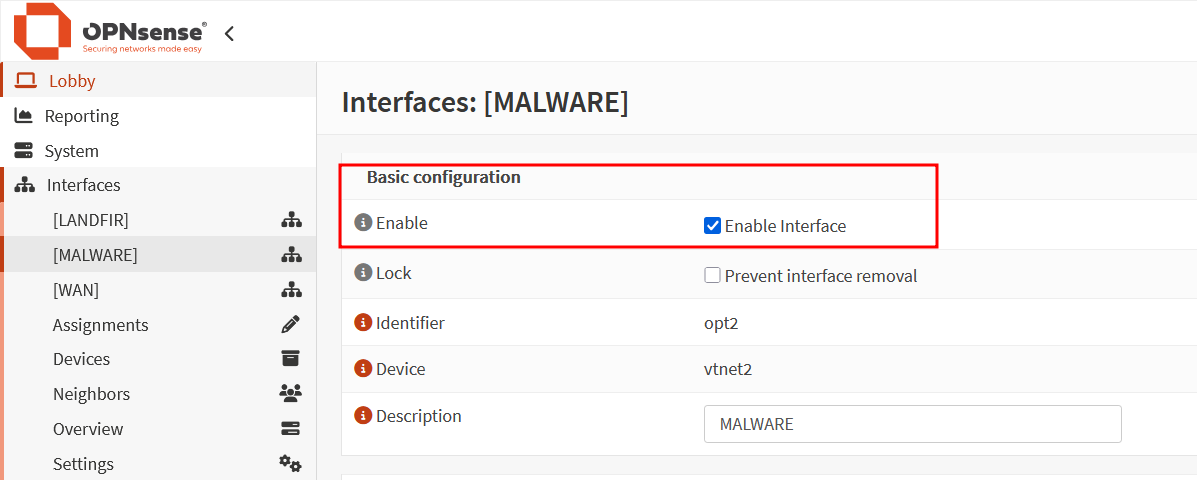
Don’t forget to enable the interfaces
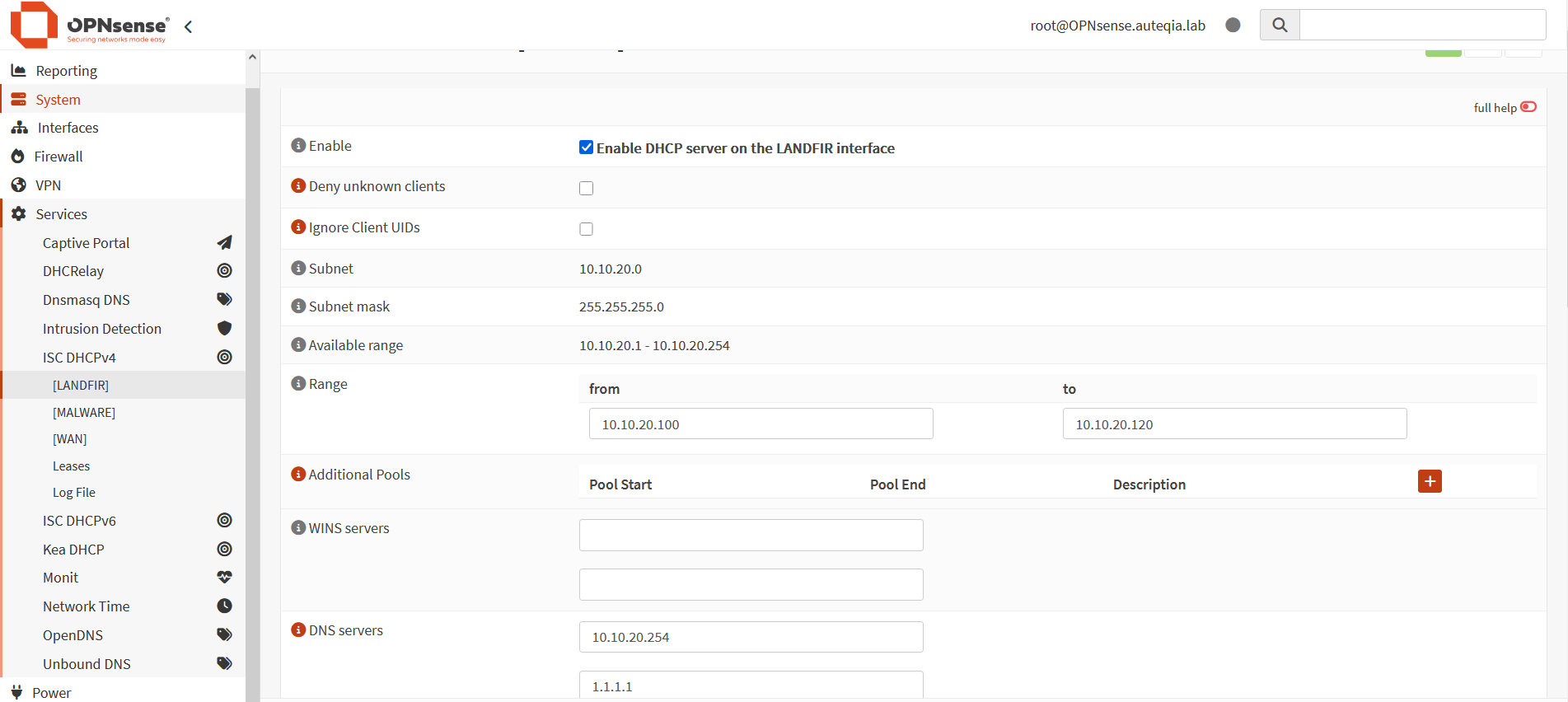
DHCP
You can enable DHCP
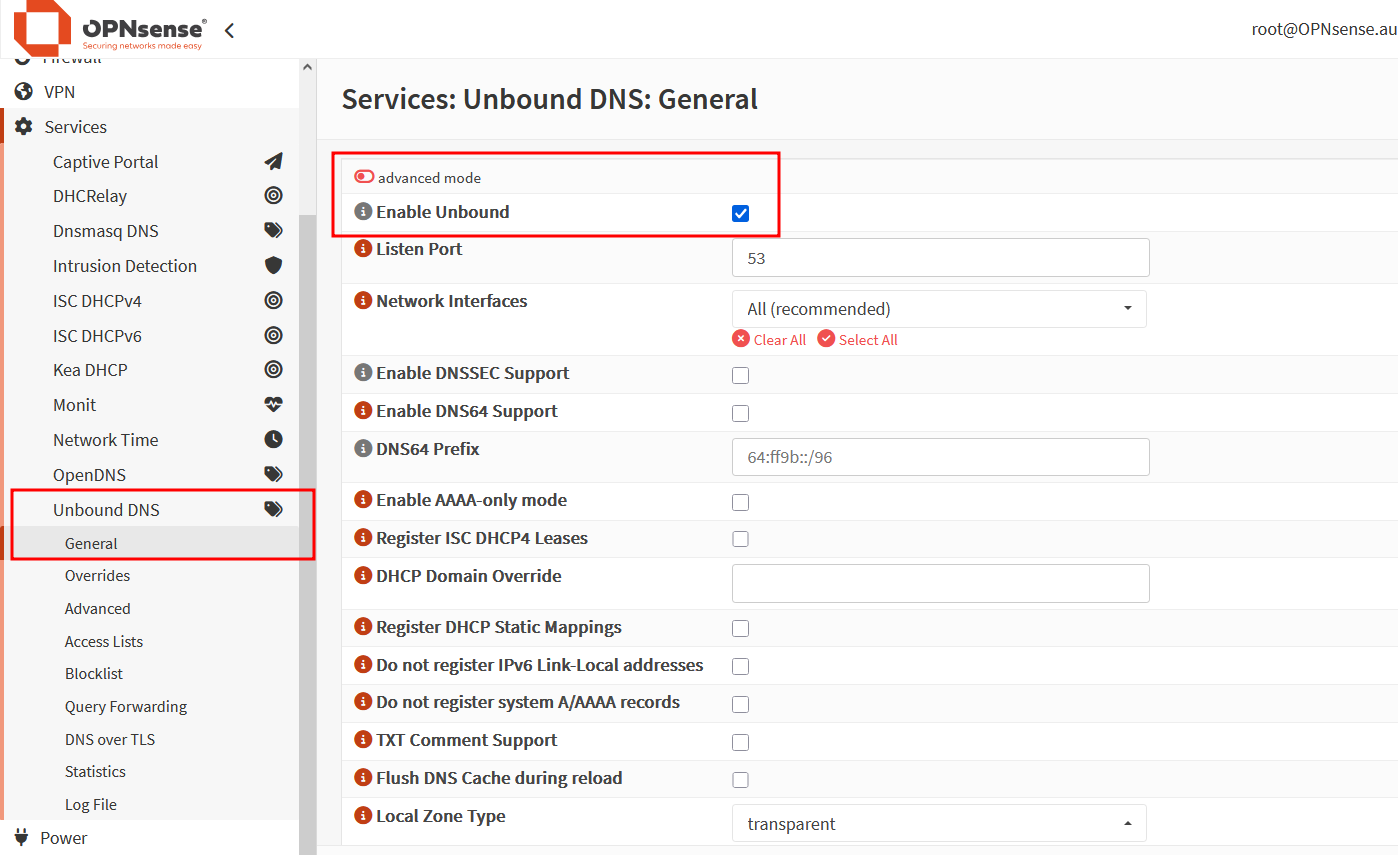
DNS
Enable DNS unbound
Set up the DNS that you want to use (you are only a DNS Forwarder, not a resolver)
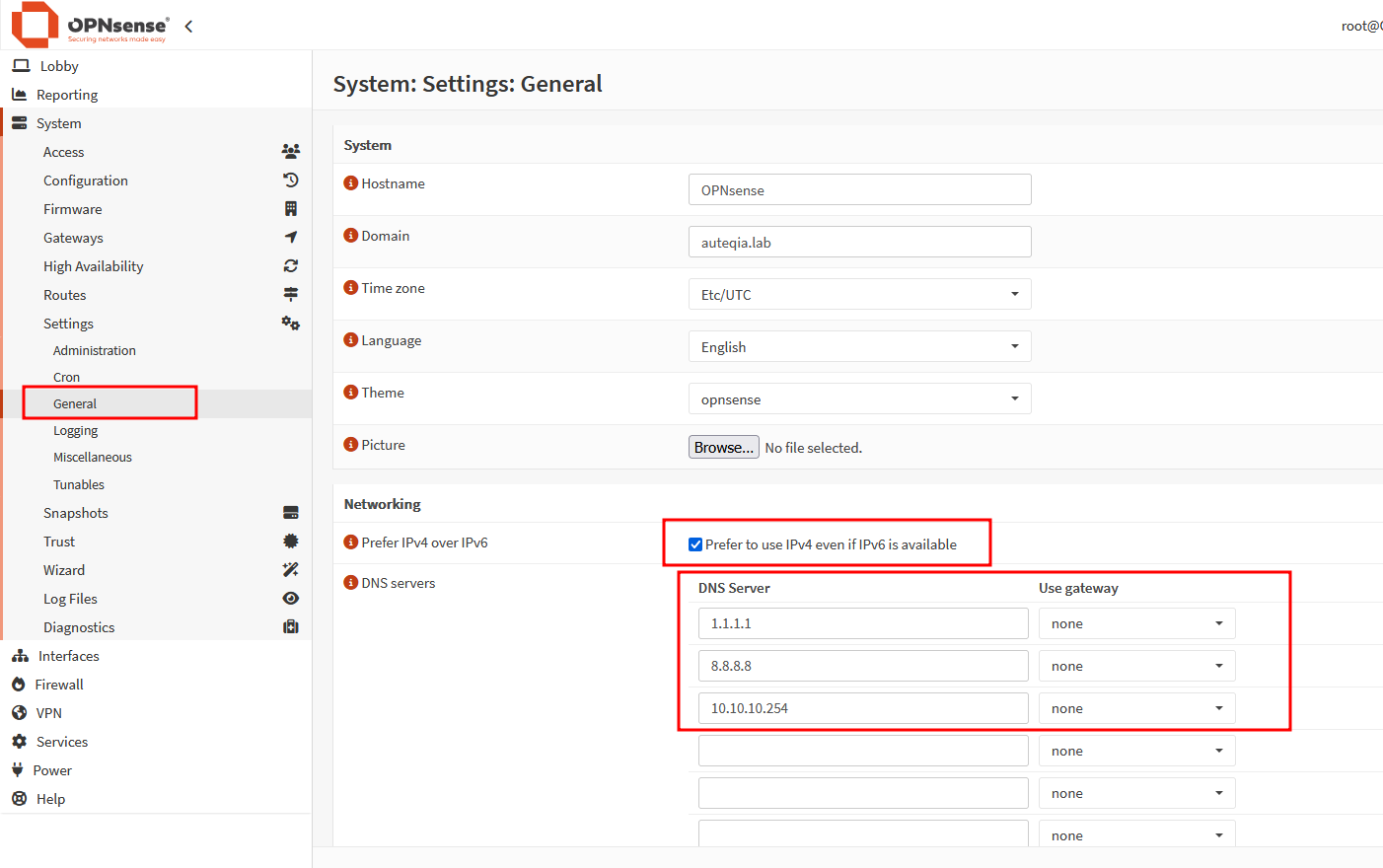
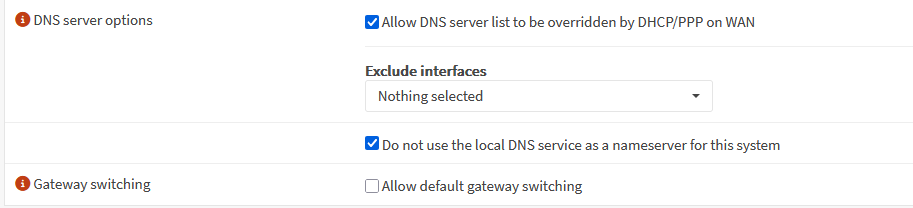
Check the Use System Nameservers
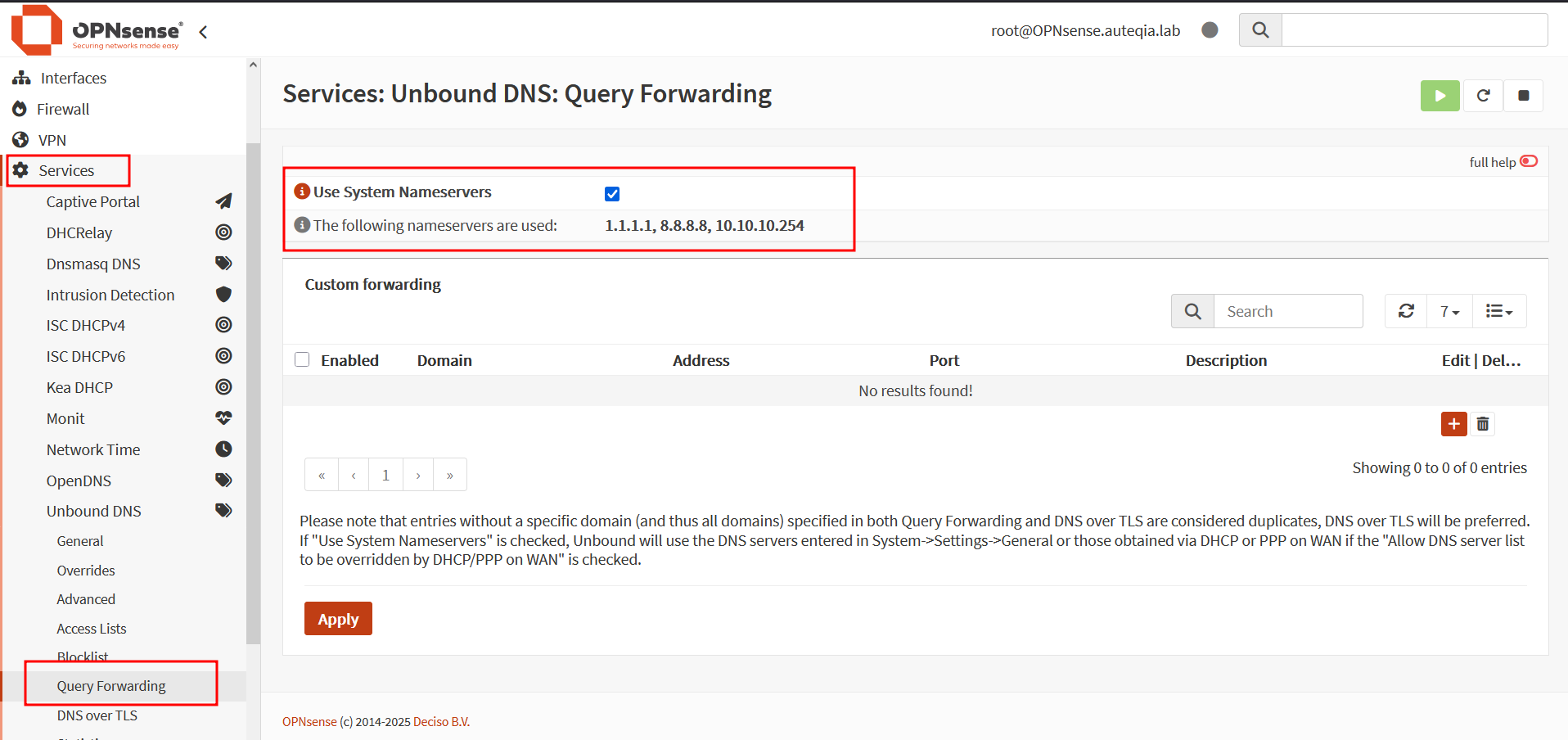
It behaves like a forwarder now thanks to the System Nameservers
NAT
Go under Firewall/NAT/Outbound
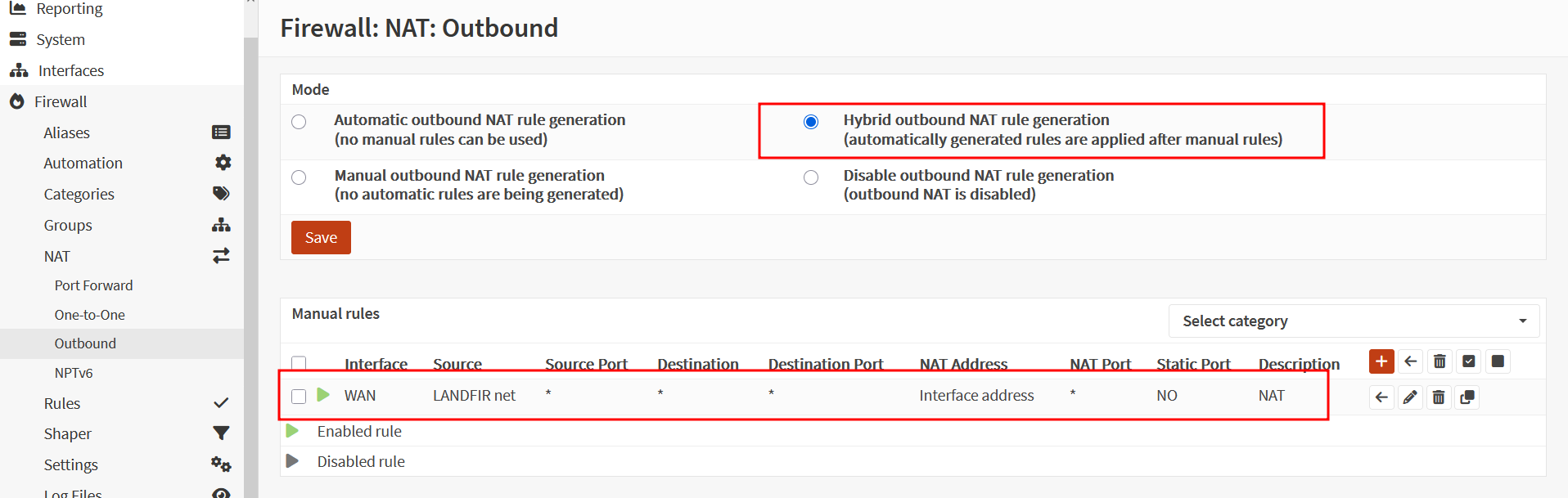
The rule should look like this.
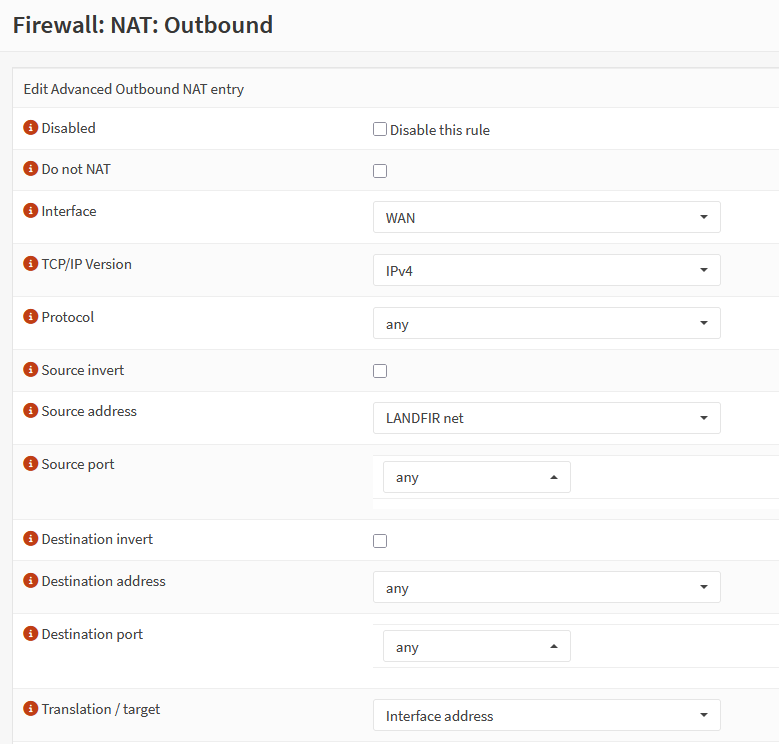
Rules
I configured strict rules for the Malware VLAN, blocking almost all outgoing connections to ensure samples can’t reach the internet unless explicitly allowed.
Routing
Because my main router (ISP box) doesn’t know how to reach 10.10.20.x or 10.10.30.x, I had to add static routes on the machines connected to the WAN.
For windows :
route -p add 10.10.20.0 mask 255.255.255.0 10.10.10.253
route -p add 10.10.30.0 mask 255.255.255.0 10.10.10.253Linux :
sudo ip route add 10.10.20.0/24 via 10.10.10.253
sudo ip route add 10.10.30.0/24 via 10.10.10.253macOS (not persistent tho):
sudo route -n add -net 10.10.20.0/24 10.10.10.253
sudo route -n add -net 10.10.30.0/24 10.10.10.253Now, I have access to my VMs!

Note that I did this because my servers aren’t up all the time. So I want to be able to go on the Internet without them up and running.
Troubleshooting
Beware, sometimes, OPNSense give you two gateways, keep the WAN Gateway only
VM’s
I use this lab for Malware Analysis with the PMAT course, for the MalDev academy and also for forensics CTF
Malware Analysis
FlareVM
I’m using FLAREVM for dynamic analysis of malware samples and PE executables.
REMNux
REMnux is used as an isolated malware lab network emulator, running tools like INetSim to fake internet services.
DFIR
For the DFIR part, i’m using a ParrotOS VM, FlareVM (not the one for Malware Analysis) and a Debian with Portainer on it, with many containers :
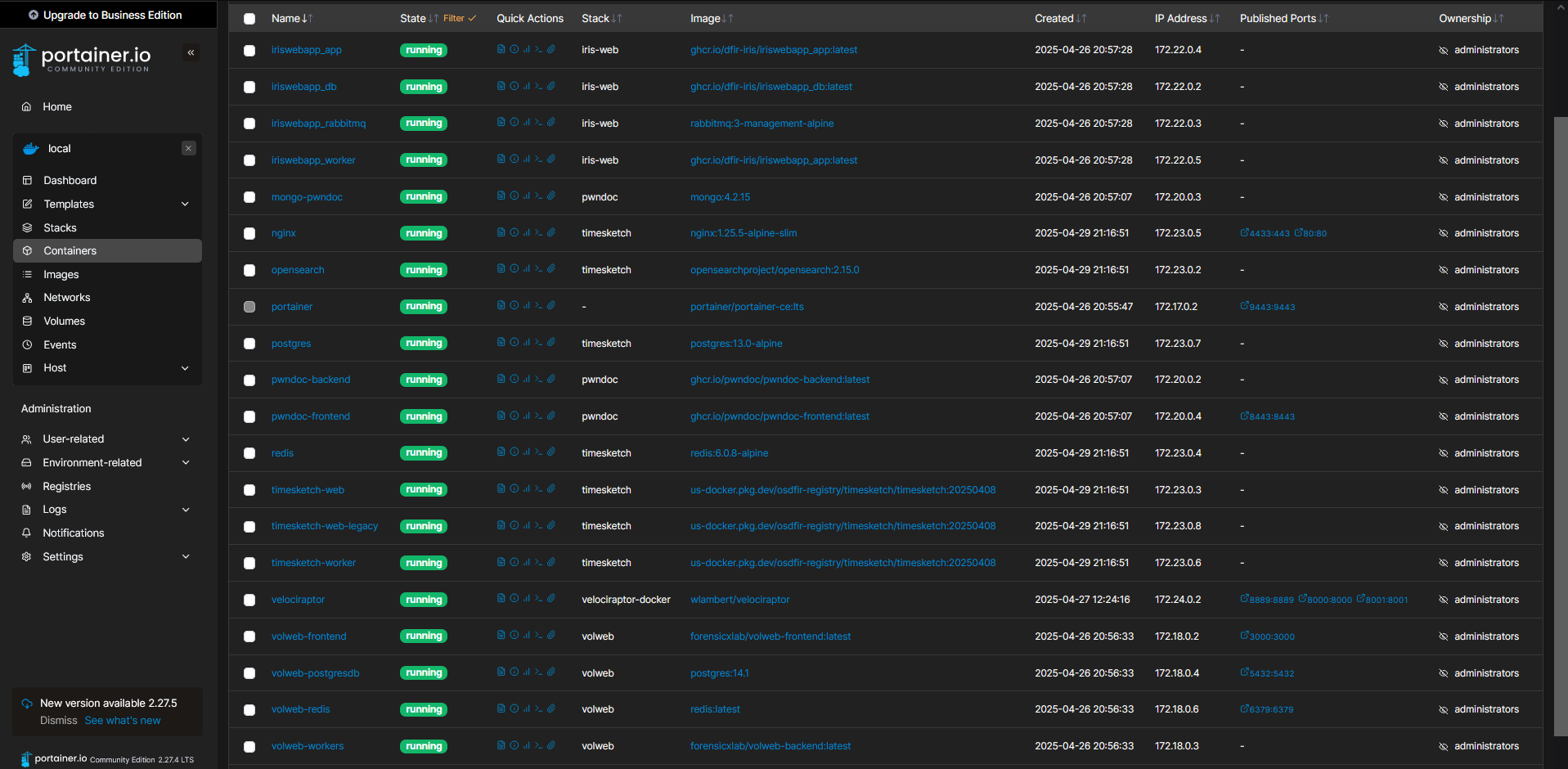
I have :
- DFIR-Iris, for DFIR reporting
- PWNDOC, for pentest reporting
- Timesketch, for collaborative timeline analysis
- Velociraptor, for the collect en masse
- Volweb, for collaborative memory analysis
On another infra, I have :
- Cyberchef, self-hosted version
- Libretranslate
- Overleaf, LaTeX editor
I want to deploy FAME & AssemblyLine as a Malware Analysis plateform :) This is in my todo list