AKASEC2024 - Portugal
I accidentally left my computer unlocked at the coffee shop while I stepped away. I’m sure that someone took advantage of the opportunity and was searching for something.
Author : d33znu75
Attachment : memdump1.mem
Introduction
First, we have the information that someone stepped away from his computer and somebody took advantage of it. We also have a memory dump and the interesting word “searching” for something, and not looking for something. That will matter later, you’ll see :)
strings for recon
strings memdump1.mem | grep -i powershellthat’s definitively noisy af
That’s really noisy and I don’t want to lose time on it, let’s continue
volatility3
Let’s start with basic recon :
/opt/volatility3/vol.py -f memdump1.mem windows.infoWe can see it’s a Windows, but we already knew with strings
/opt/volatility3/vol.py -f memdump1.mem windows.pslistEverything looks pretty normal except chrome.exe
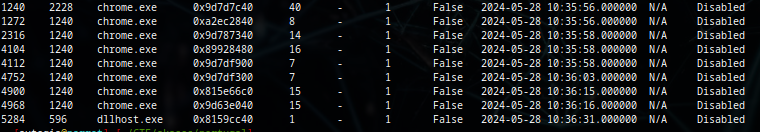
And now, i’m starting thinking about the “search for something”. chrome.exe seems suspect and unusual. There’s the master chrome.exe (PID 1240) process and the tabs that depends on the master process.
For later, let’s continue the recon
filescan
Let’s see what’s inside the memory with a filescan :
/opt/volatility3/vol.py -f memdump1.mem windows.filescan > filescan.txtlooking for something unusual
With the filescan.txt I tried to grep on extension that can be interesting, such as .evtx .ps1 or .bat but nothing appeared
strings for chrome
Now we can move forward and try some strings on the dump file and grep more precisely
strings for Google queries :
strings memdump1.mem | grep "https://www.google.com/search?q="We have plenty of queries, let’s look at them
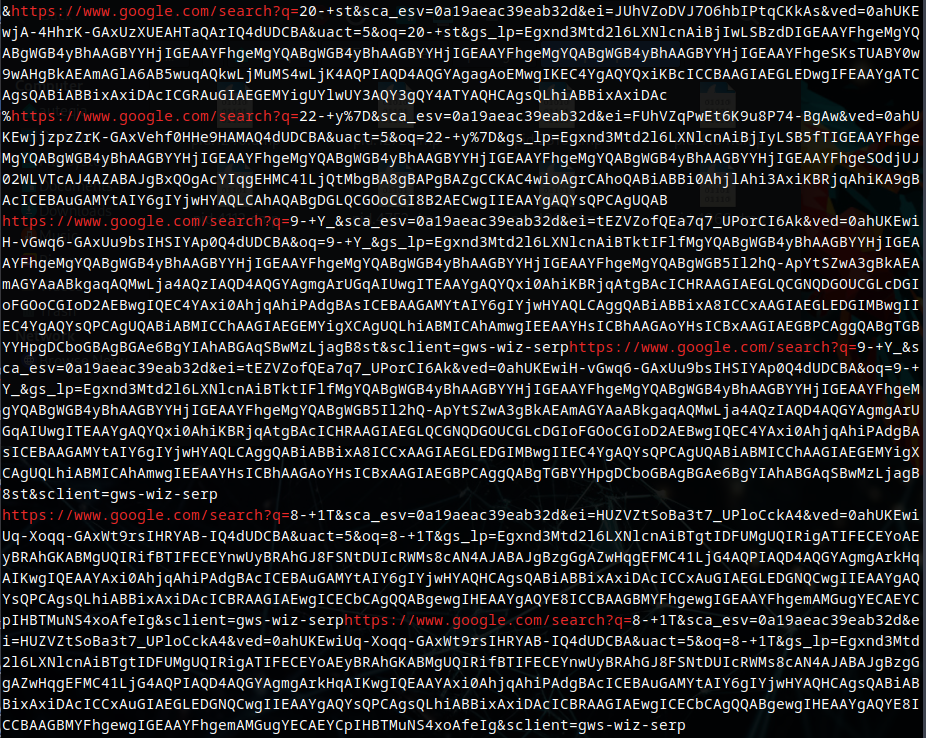
8 - 1T
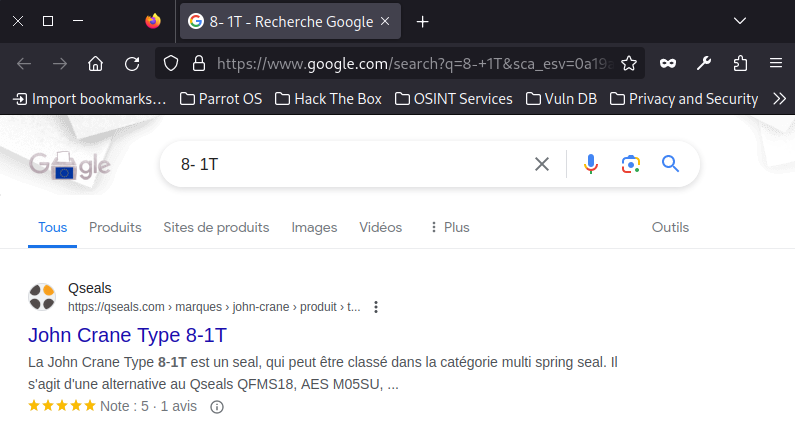
20 - st
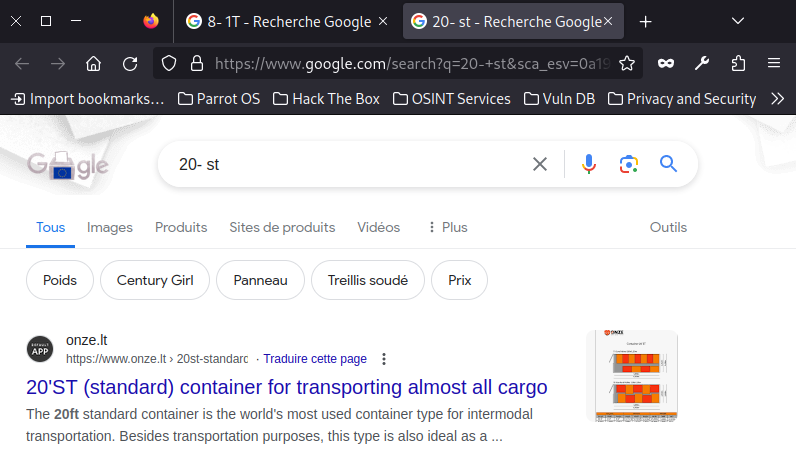
5 - 0L
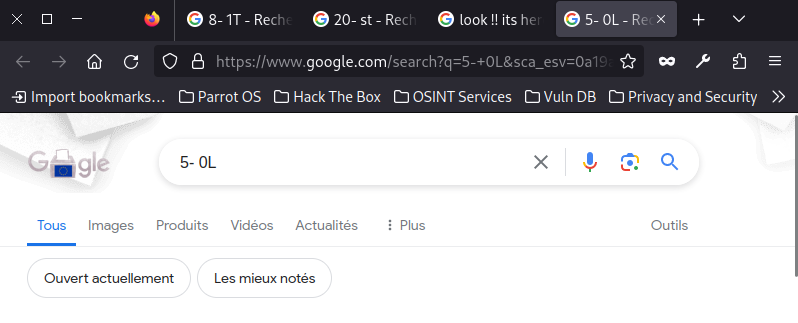
oh !
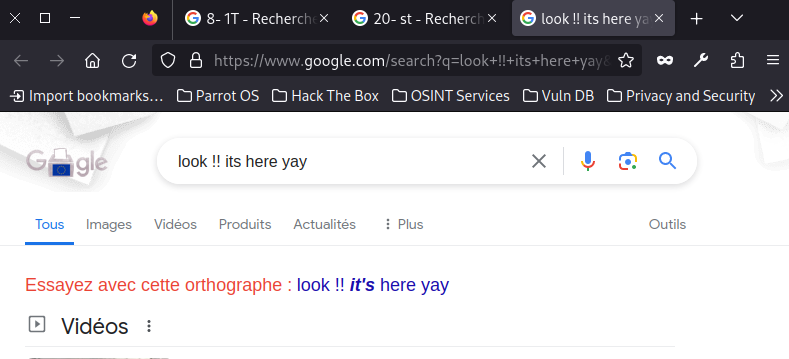
But even if I didn’t see the last one, I would have checked deeper in the Chrome history. Now we know that something is going on with Chrome searches. Let’s dump all the memory of chrome processes.
memdump
First, I dumped all the process and tabs
/opt/volatility3/vol.py -f memdump1.mem windows.memmap ‑‑dump ‑‑pid 1240
/opt/volatility3/vol.py -f memdump1.mem windows.memmap ‑‑dump ‑‑pid 4900
/opt/volatility3/vol.py -f memdump1.mem windows.memmap ‑‑dump ‑‑pid 4104
/opt/volatility3/vol.py -f memdump1.mem windows.memmap ‑‑dump ‑‑pid 5200
/opt/volatility3/vol.py -f memdump1.mem windows.memmap ‑‑dump ‑‑pid 4968
/opt/volatility3/vol.py -f memdump1.mem windows.memmap ‑‑dump ‑‑pid 2316
/opt/volatility3/vol.py -f memdump1.mem windows.memmap ‑‑dump ‑‑pid 4752
/opt/volatility3/vol.py -f memdump1.mem windows.memmap ‑‑dump ‑‑pid 4112
/opt/volatility3/vol.py -f memdump1.mem windows.memmap ‑‑dump ‑‑pid 1272If we strings and|or grep on all the dumped process we can see some kind of history, but it clearly need to be reconstructed.
grep -Ria https://google.comSo, in order to get something clearer, I dumped the file that contains Chrome history!
dump Chrome History
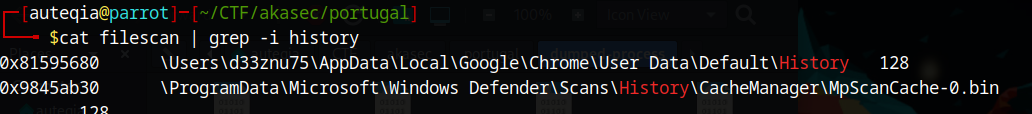
I’m looking for some history files
cat filescan | grep -i historyYes found it !
Let’s dump it
/opt/volatility3/vol.py -f memdump1.mem -o filedump/ windows.dumpfiles --virtaddr=0x81595680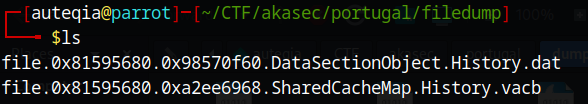
for the convenience :
mv file.0x81595680.0x98570f60.DataSectionObject.History.dat historySo let’s string it :
strings history 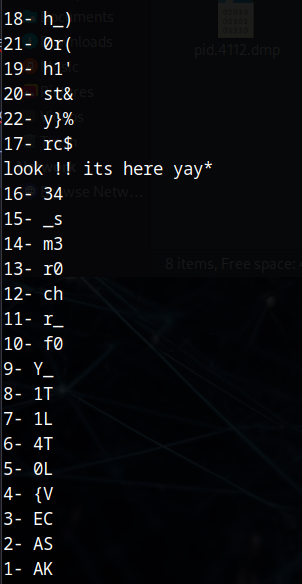
That’s definitively this. Let’s extract them in order to rearrange thing. It starts from 1 and ends to 22.
Once it rearrange with the right number for the string, we obtain the flag :
AKASEC{V0L4T1L1TY_f0r_chr0m3_s34rch_h1st0ry}That was a nice challenge :)