AKASEC2024 - Sharing is not Caring
My friends and I use the same computer on campus and have a shared folder to exchange files. After submitting the flag for the challenge, it was leaked, and someone obtained it without my knowledge. I’m unsure how they got it.
Author : d33znu75
Attachments : disk.ad1 & network.pcapng
Disk
After downloading the files, I mounted the .ad1 disk file with FTK Imager.
After scrolling thgought all the users, I remembered that the Public folder is shared among all the users. This may be the exchange folder that is mentionned on the challenge. Let’s see :

It really looks like a common marketplace where everyone upload his files. Okokokok so, let’s check what can be good for our investigation :
A pretty cat named WhatsApp 2 i love him really much
A strange broccoli guy
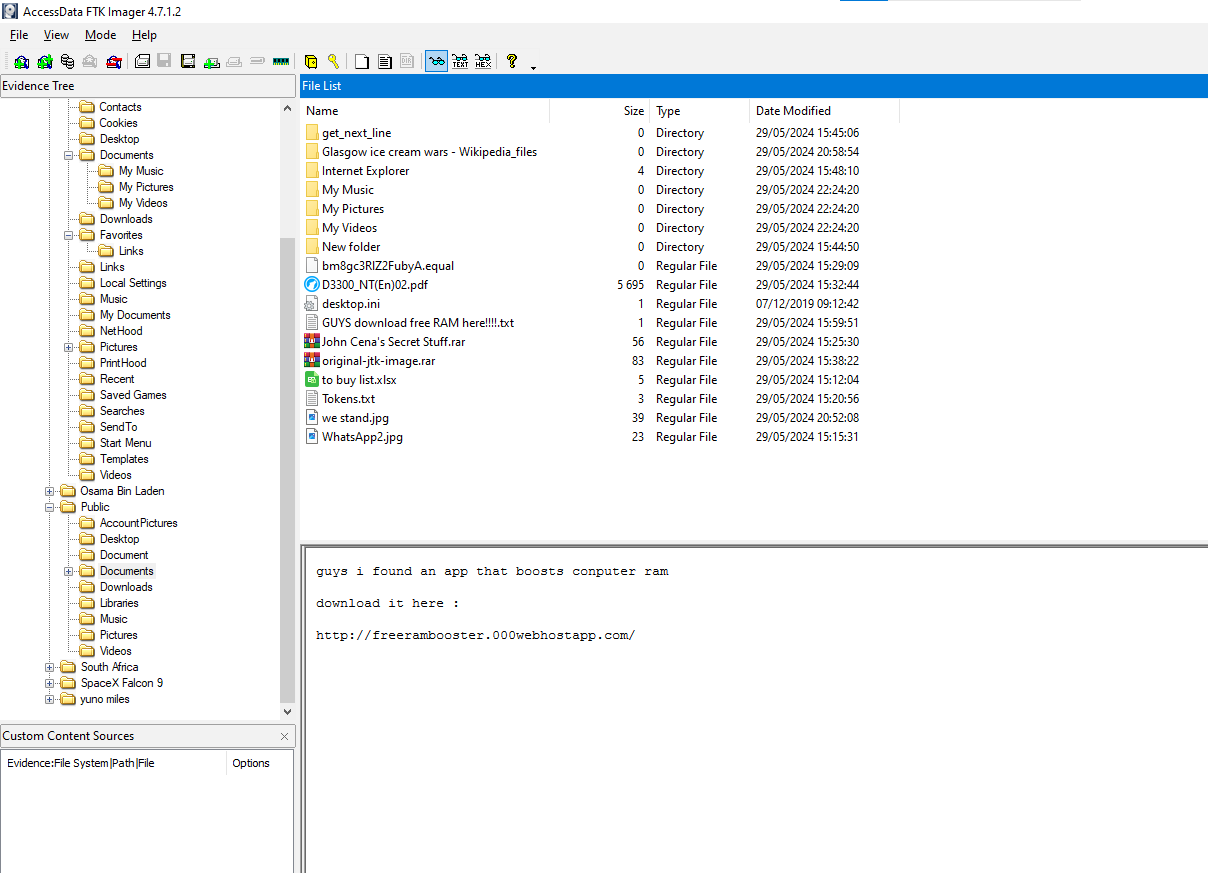
Among all this garbage, we can see two rar files that are locked by a password. I tried to run john on the background to see if I can get something, but let’s go ahead
The rar of John Cena :

I also found a strange .txt file that talks about free RAM boost, that’s seems cool, FREE RAM??
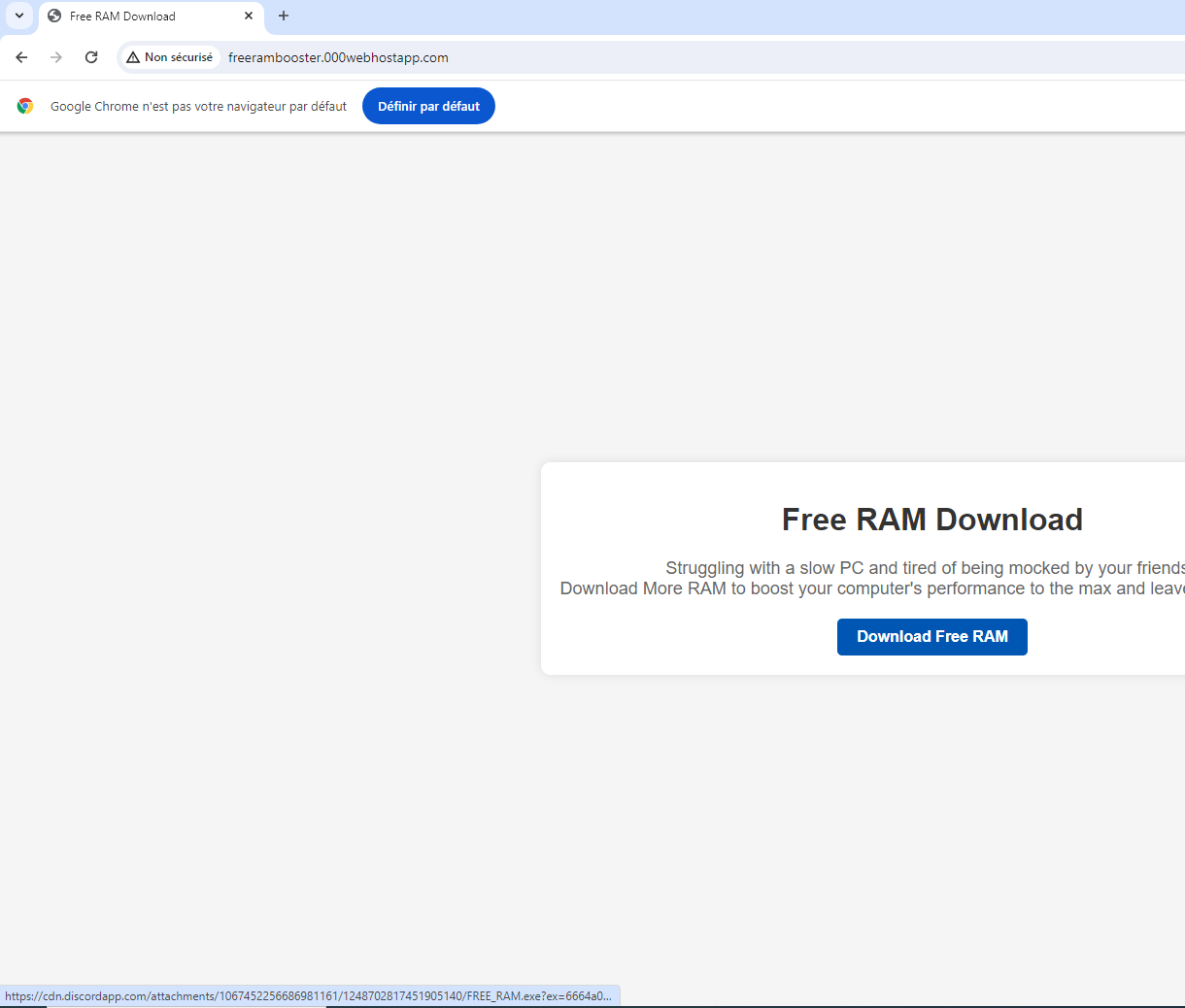
I went to the url, notice that http is important because https sends us to the wrong place.
pretty cool website
When we go to the http website, we can now download free ram, that’s incredible, but wait a minute. Have you seen the link in the bottom of the page? A discord attachement looks WEIRD. Let’s download it in a VM :D
here’s the link : BE CAREFUL THAT A SH1TTY EXE : https://cdn.discordapp.com/attachments/1067452256686981161/1248702817451905140/FREE_RAM.exe?ex=6664a09f&is=66634f1f&hm=bc1e51999ffe4b6246999111c477f170eac8c4b3a95935e7ff8335919421b53a&
FREE_RAM.exe
Now downloaded, let’s run it (for the lore)


ohyéééé, the exe tells us that he’s looking for a file at C:\Users\Public\Documents\Internet Explorer\SIGNUP\sslkey.log
We lucky, there’s some file in the .ad1 file that FTK mounted !!
sslkey.log
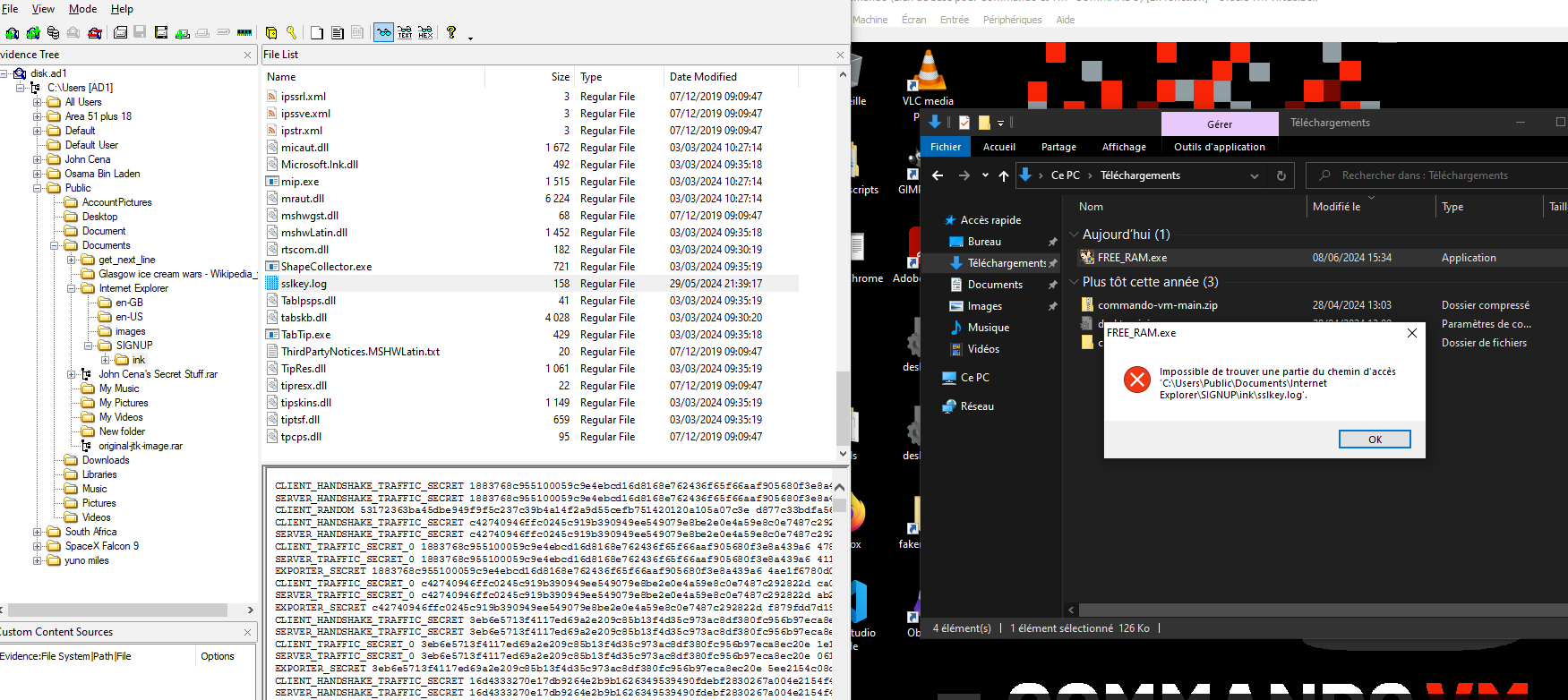
Bottom right, the sslkey.log file, let’s save it and check afterwards the pcapng file
Network Traffic
First, let’s check for protocol hierarchy and statistics


Some pure HTTP, let’s check
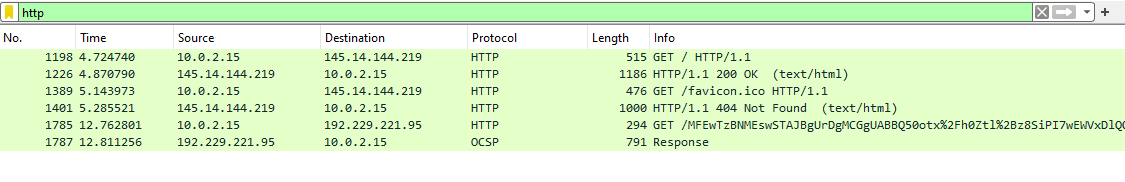
nothing that crazy
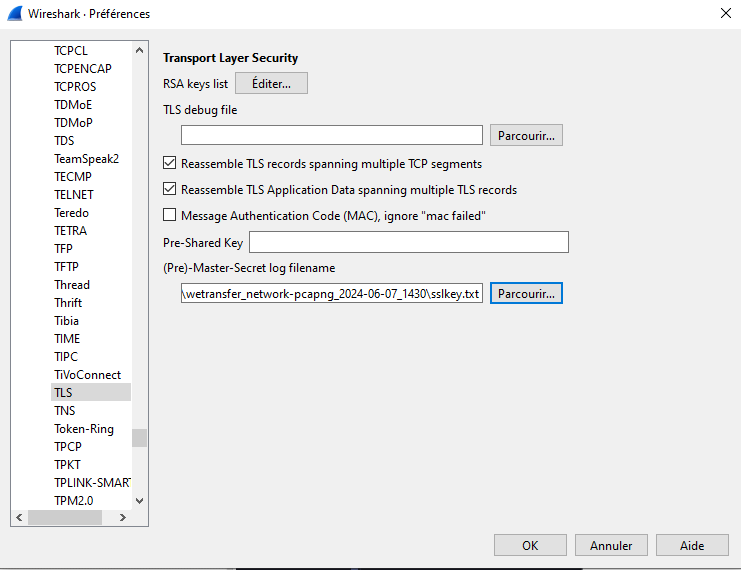
Ok but, there’s full of encrypted streams, but we have the SSL keys !!
Let’s add them : Edit/Preferences/Protocols/TLS and add the key files to pre-Master Secret
We have now so much more data. Let’s check HTTP2
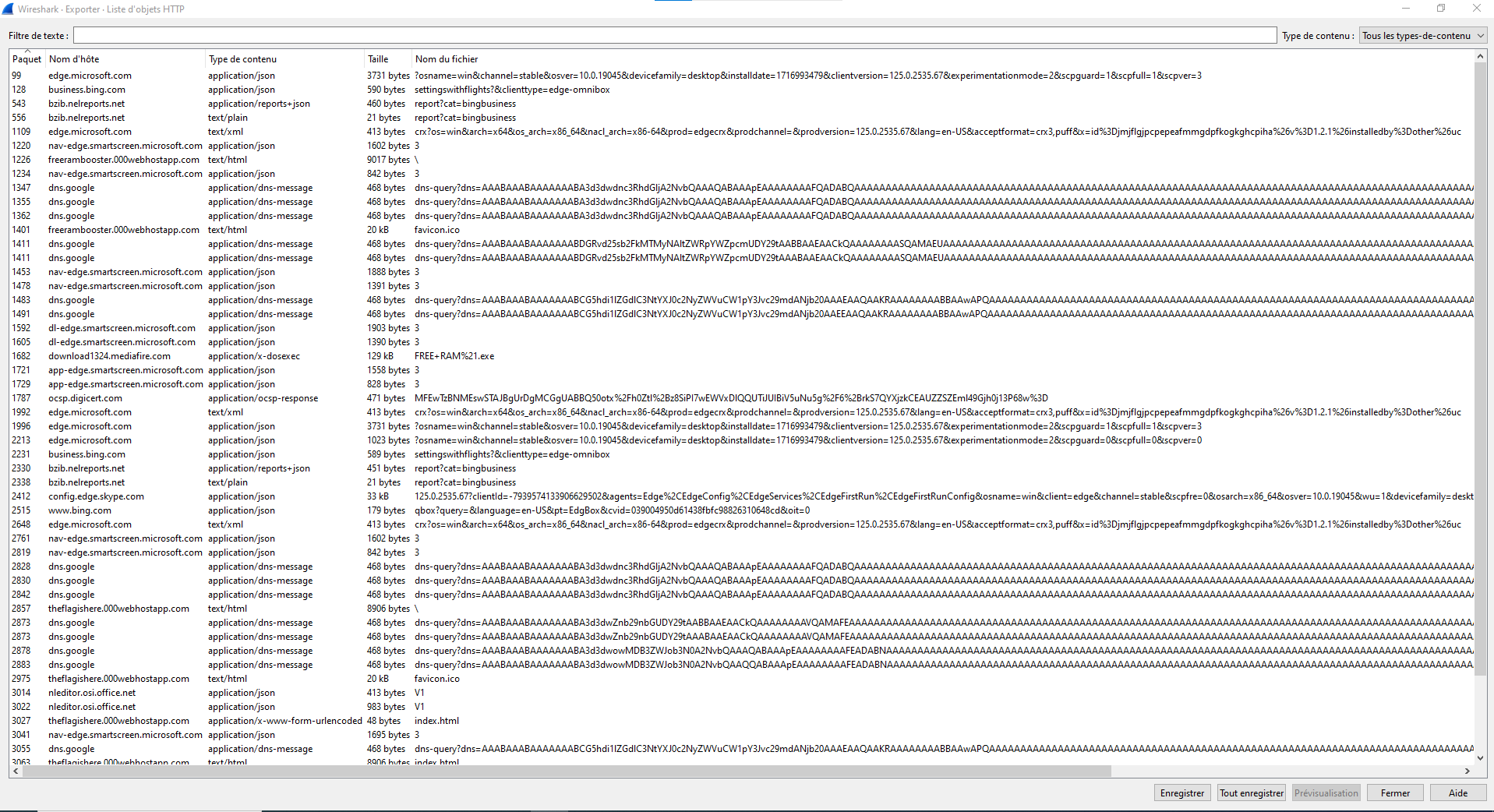
We have some traffics but I ain’t gonna check every packets
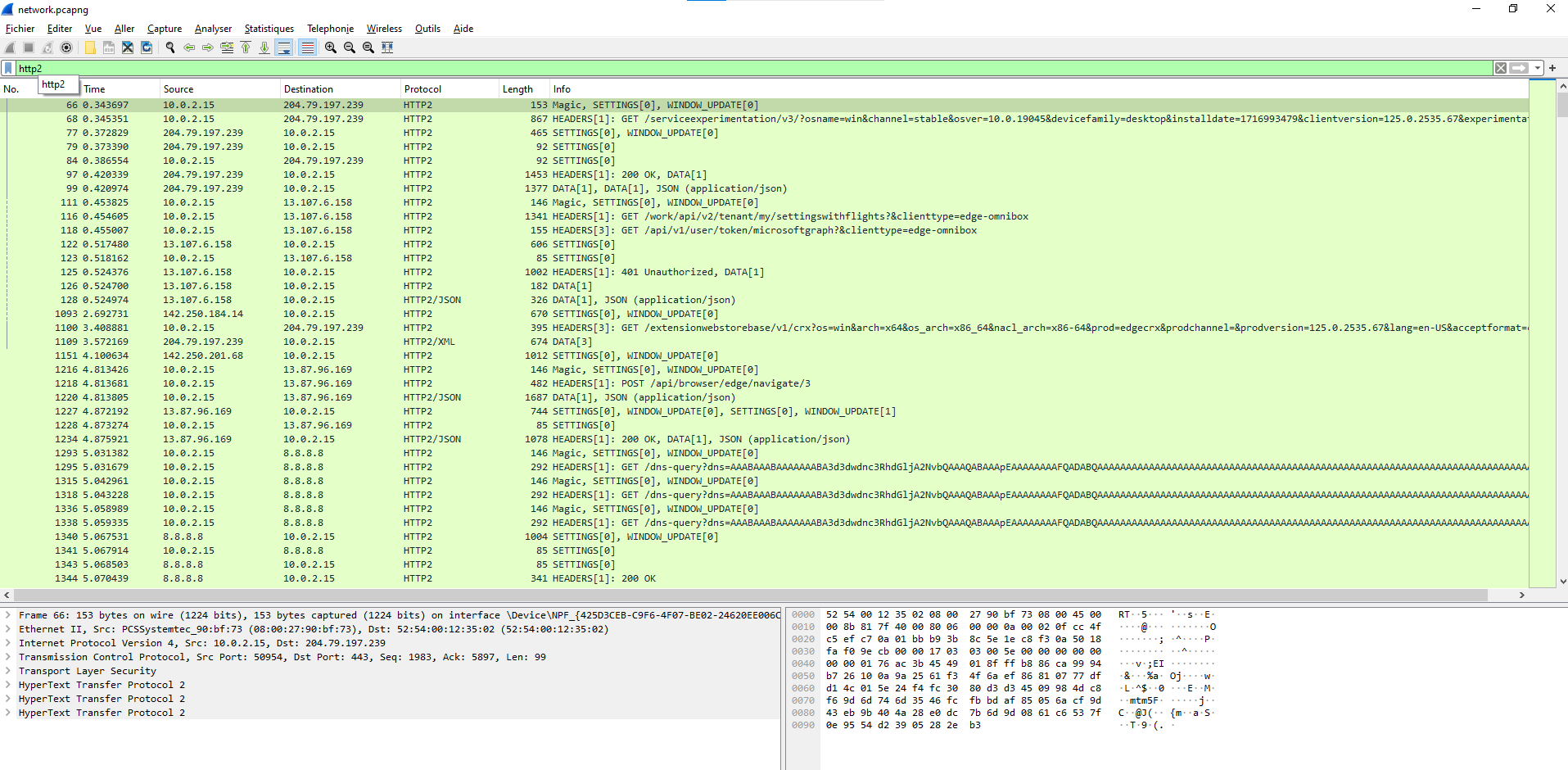
I exported the traffic as raw data
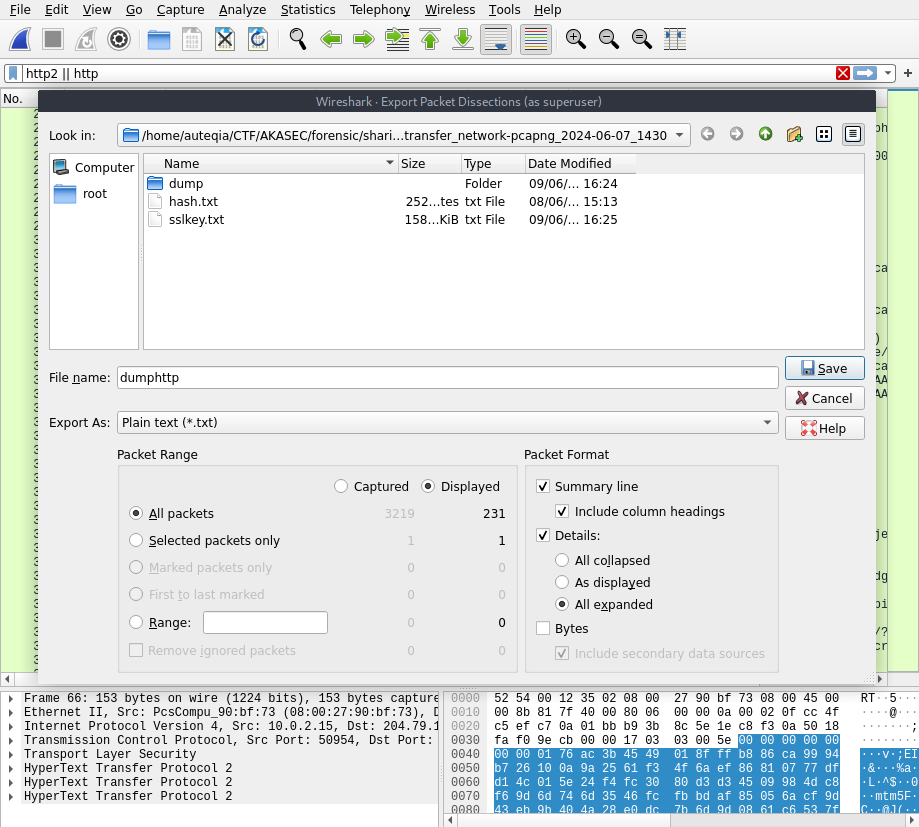
strings dumphttp.txt | grep -i AKASECand the flag appears !!
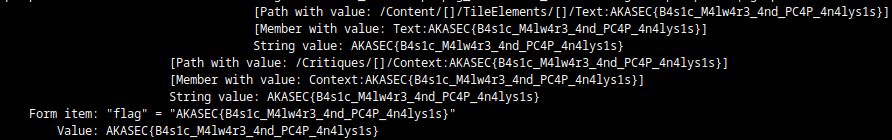
AKASEC{B4s1c_M4lw4r3_4nd_PC4P_4n4lys1s}
Thanks to my mate Slotekh who found the flag first ;)