AKASEC2024 - Snooz
don’t wake me up, I want a snooze u will find everything on my laptop!!
Author: samaqlo
Let’s start by Wireshark, in HTTP streams we can observe that a strange thing is downloaded, let’s pick it
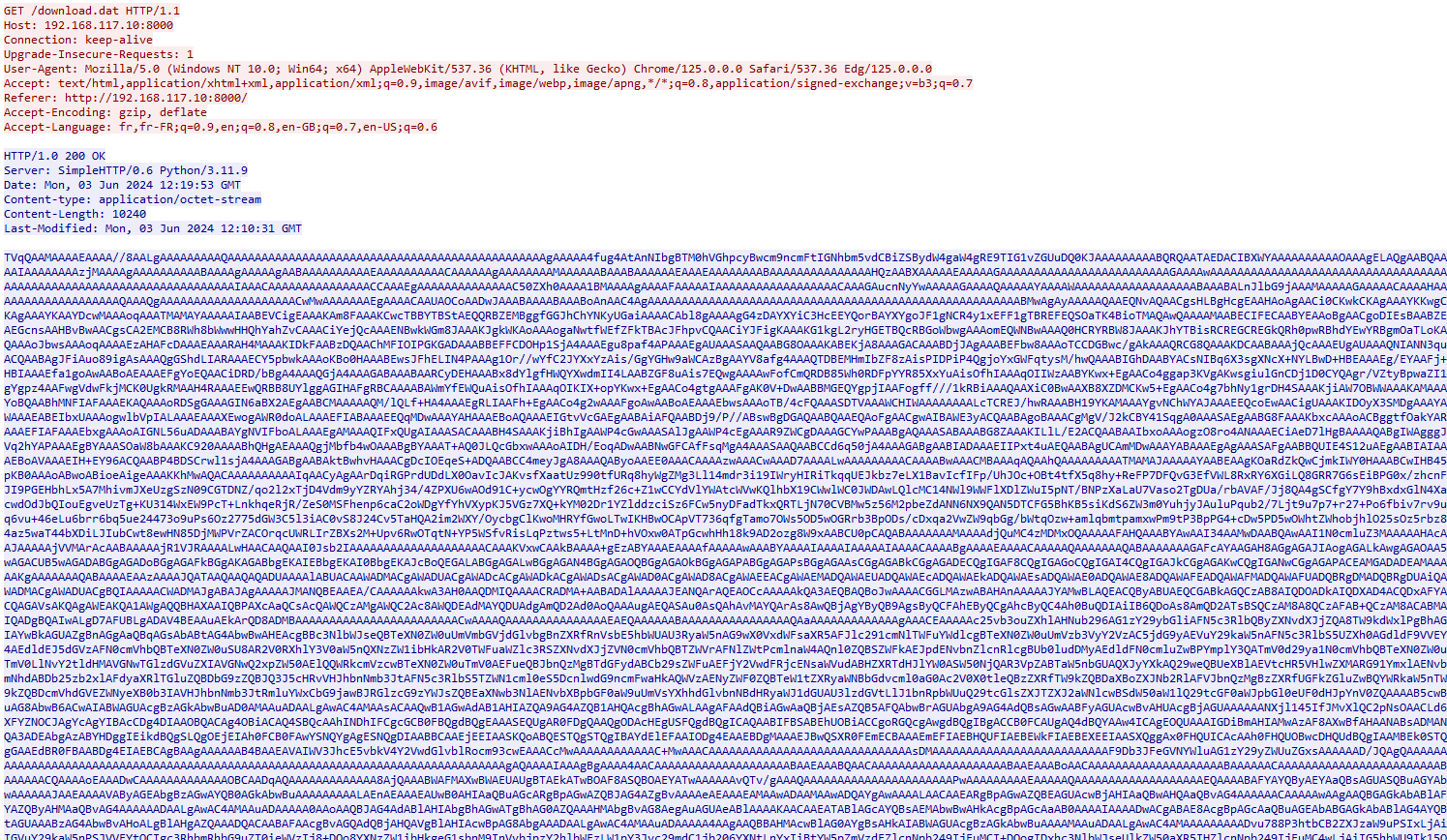
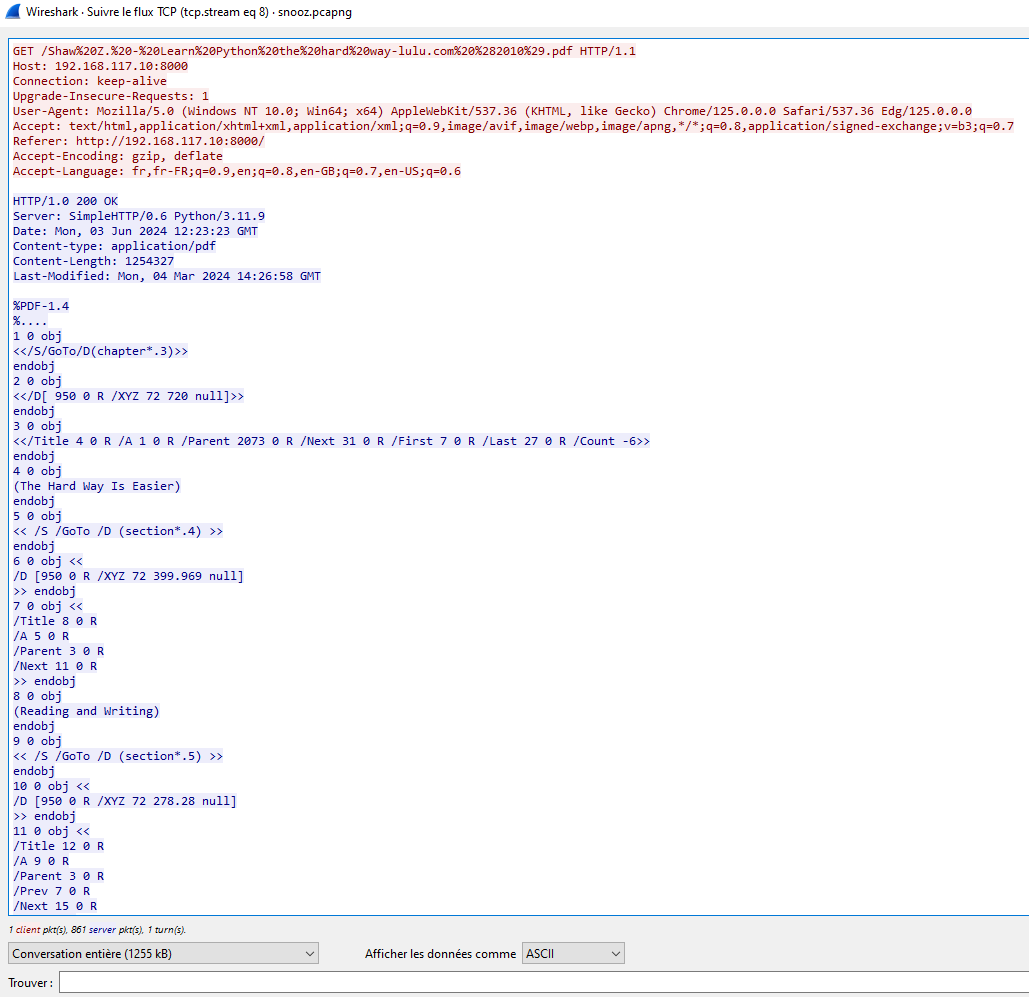
We can also see the PDF downloaded. It appears on HTTP object too
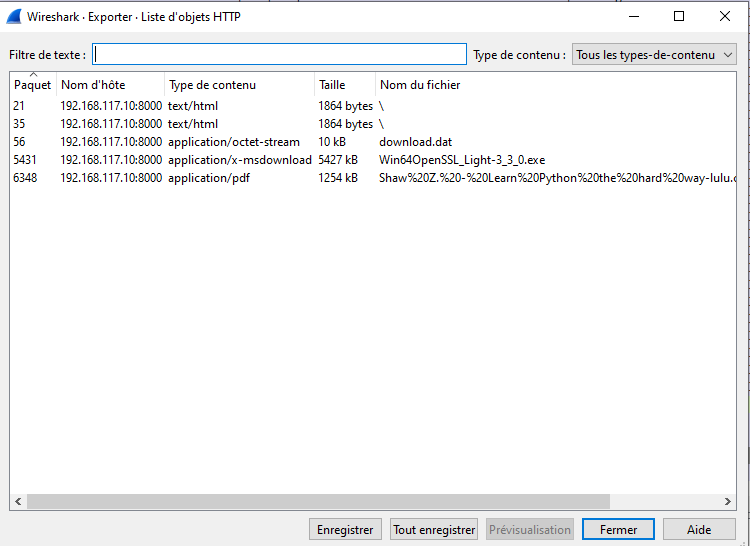
download.dat is the strange file in base64
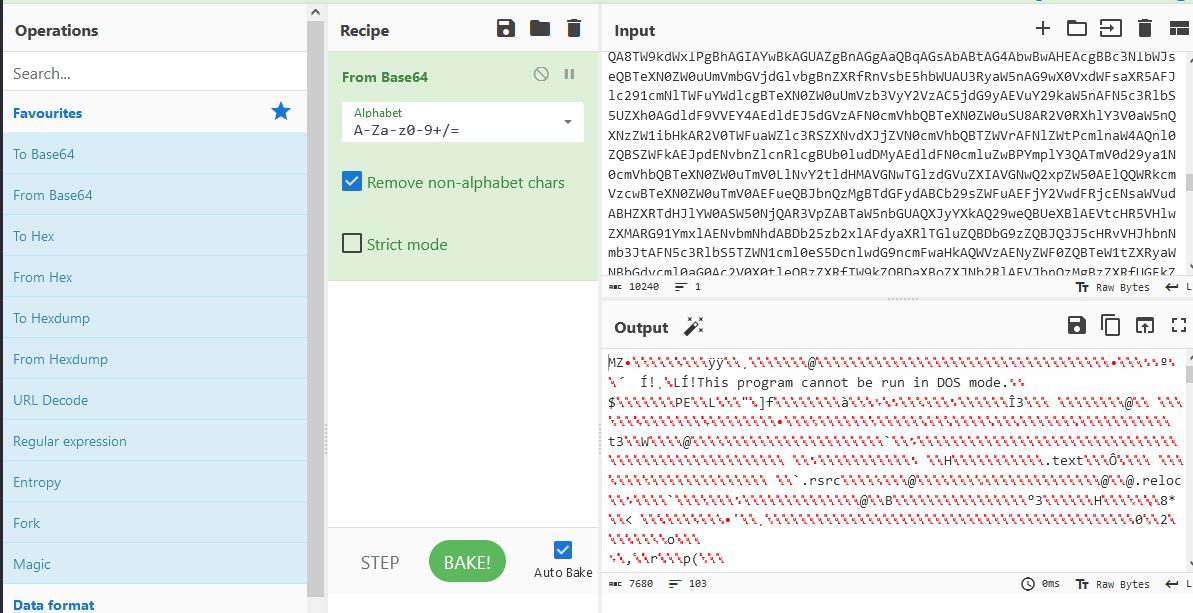
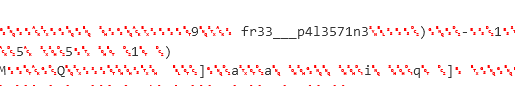
Once extracted :
file download.exe
download.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sectionsIn a Windows VM with dnSpy, let’s start the debugger :
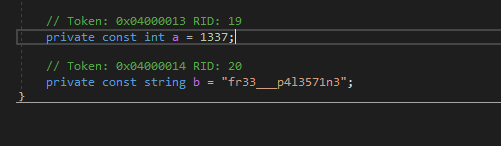
nice ! a pretty string
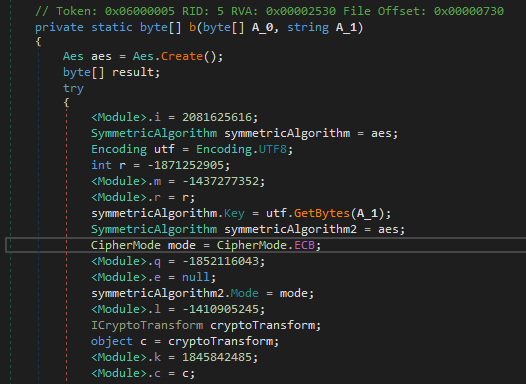
In the code, we can see that it waits for incoming connexion on the TCP port 1337
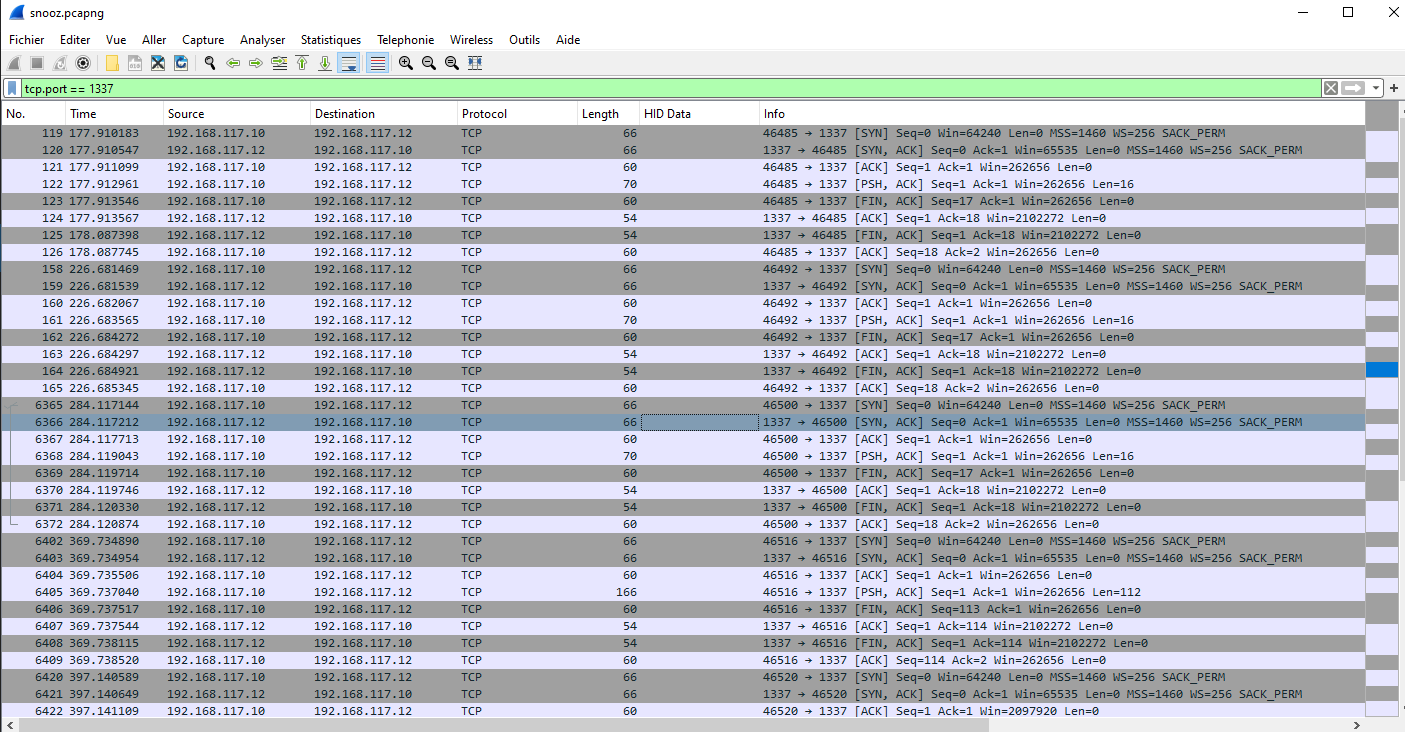
with tshark
tshark -r snooz.pcapng -Tfields -Y "tcp.port == 1337" -e 'data.data' > tcp1337.txt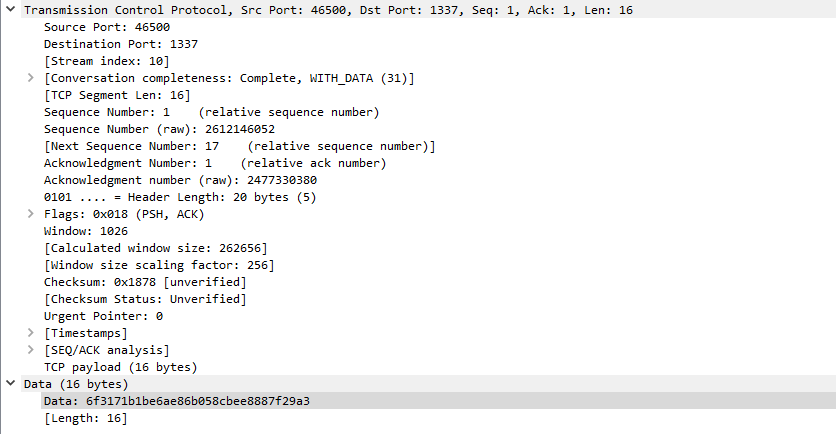
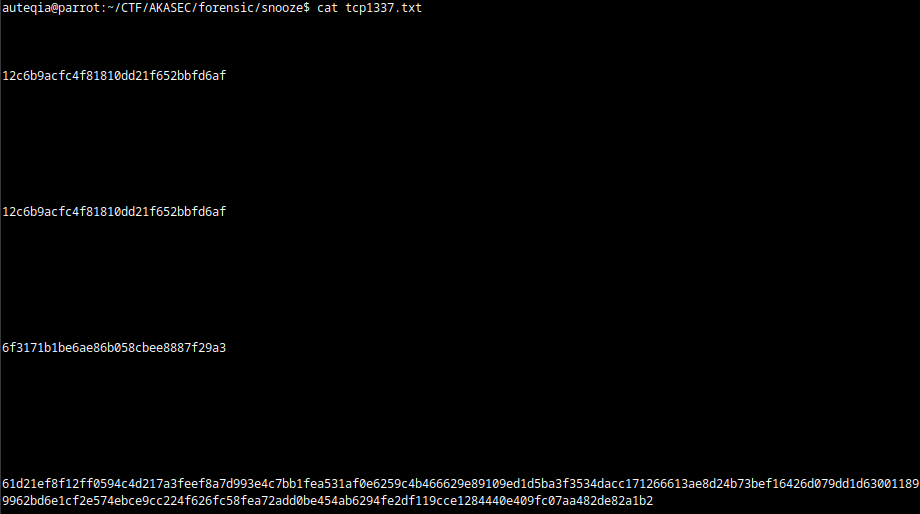
It gives us this :
12c6b9acfc4f81810dd21f652bbfd6af12c6b9acfc4f81810dd21f652bbfd6af6f3171b1be6ae86b058cbee8887f29a361d21ef8f12ff0594c4d217a3feef8a7d993e4c7bb1fea531af0e6259c4b466629e89109ed1d5ba3f3534dacc171266613ae8d24b73bef16426d079dd1d630011899962bd6e1cf2e574ebce9cc224f626fc58fea72add0be454ab6294fe2df119cce1284440e409fc07aa482de82a1b20e449b0133eed2e00a240569c4650ffaCyberchef
AES ECB don’t use IV, and, in the code we didn’t see any explicit usage of IV’s
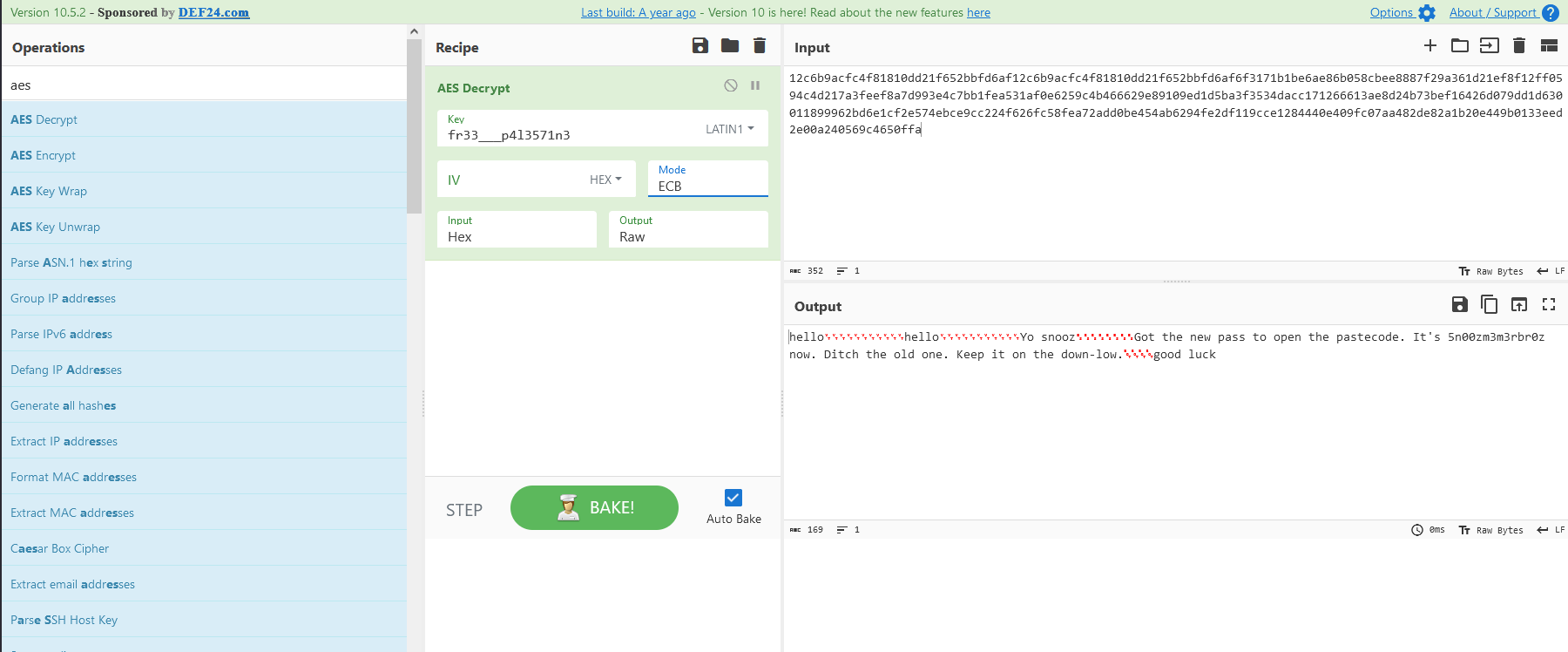
From now we have found something !!
hello hello Yo snooz Got the new pass to open the pastecode. It's 5n00zm3m3rbr0z now. Ditch the old one. Keep it on the down-low. good luckWe have a password, let’s check the memory dump
Time to check Memory dump
Recon
windows.info
/opt/volatility3/vol.py -f memdump.mem windows.infoThat’s a Windows
windows.pslist
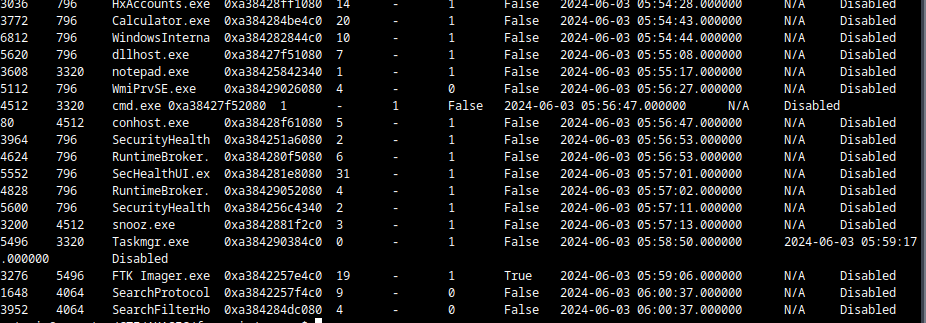
Weirds process :
- notepad.exe pid 3608
- msedge pid 5844 76 3040 5924 2872
- cmd exe 4512
- snooz.exe 3200
windows.netscan
/opt/volatility3/vol.py -f memdump.mem windows.netscan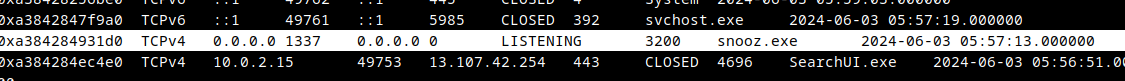
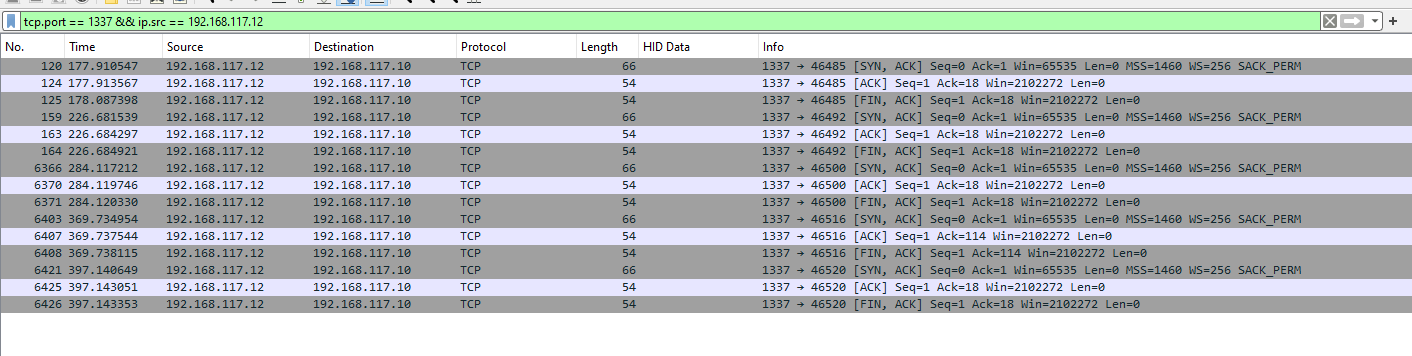
tcp.port == 1337 && ip.src == 192.168.117.12The traffic that matches
windows.procdump
Proc dump of snooz.exe
That dumps all dll and the .exe. It’s the same exe than the one we found (download.dat) so that’s useless but i did it
/opt/volatility3/vol.py -f memdump.mem -o output-proc/snooz windows.dumpfiles ‑‑pid 3200windows.memdump
memory dump of snooz.exe in case of
/opt/volatility3/vol.py -f memdump.mem -o output-proc/snooz windows.memmap ‑‑dump ‑‑pid 3200memdump of notepad.exe
/opt/volatility3/vol.py -f memdump.mem -o notepad/ windows.memmap ‑‑dump ‑‑pid 3608strings
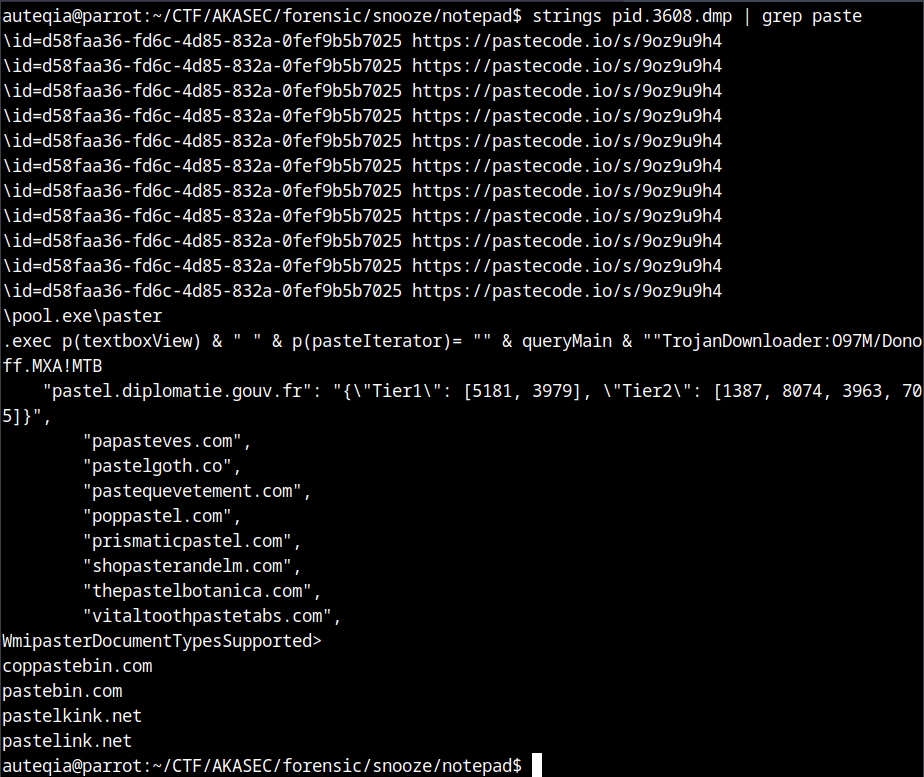
strings the whole memdump instead of the notepad
pastecode.io
Now we have the website and the password, let’s gooo :
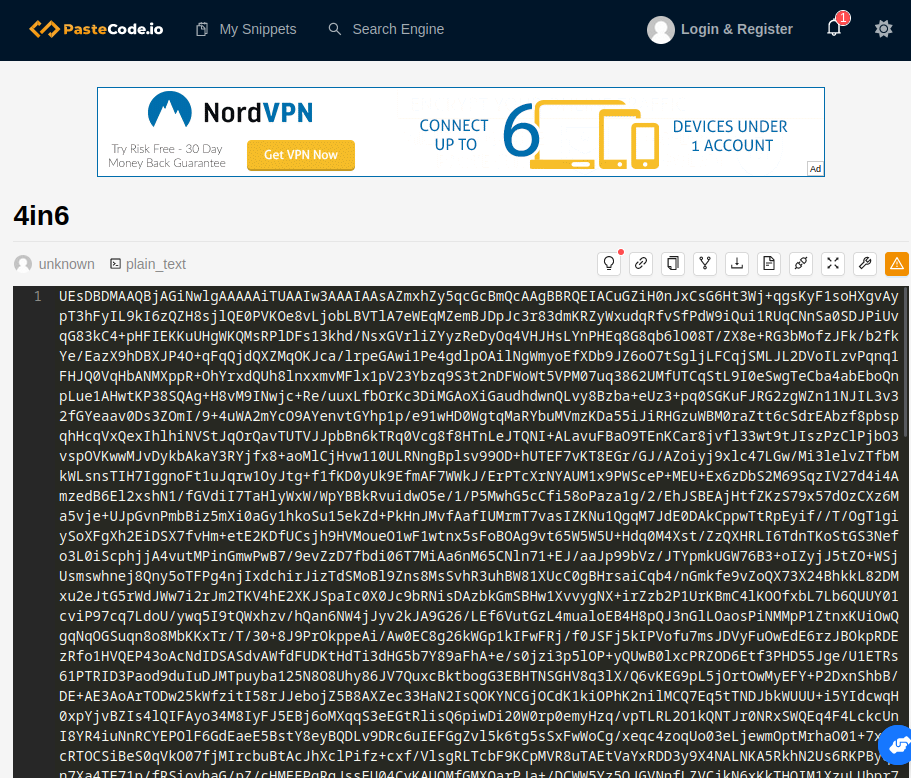
I downloaded it and bring it to binary
base64 -d 4in6-pastecode_io.txt > bigboy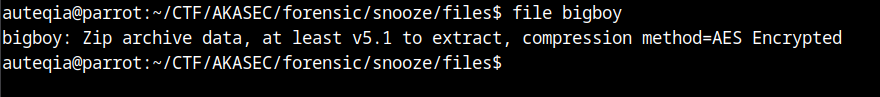
it’s encrypted :((
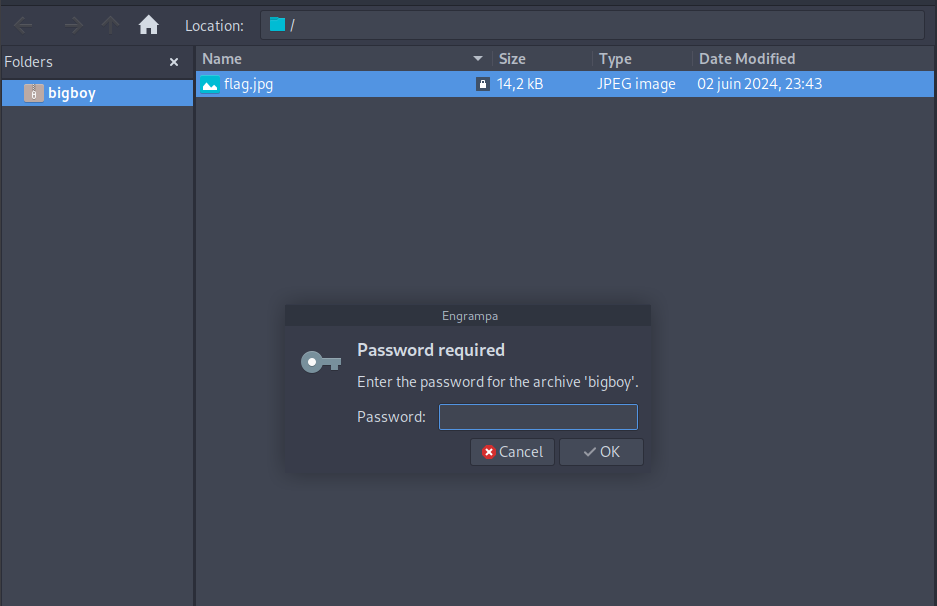
I started john in background just in case

So where I should have look to get the password of the zip file.
Starting over
We have weirds process :
- notepad.exe pid 3608
- msedge pid 5844 76 3040 5924 2872
- cmd exe 4512
- snooz.exe 3200
snooz.exe is the malicious file cmd.exe execute the snooze.exe edge ? notepad already gave us the pastecode.io link
And i remembered that one of the root-me challenges was about memdump a process in order to see what was displayed on the screen. I tried it with snooz.exe because when I was trying the exe (before i decrypted tcp stream, just for fun) the exe printed the result on the terminal. So maybe I can catch some information displayed at the moment on the screen
snooz.exe sandboxinnnn
with dnspy, that the same as download.dat ^^
let’s try it in a vm
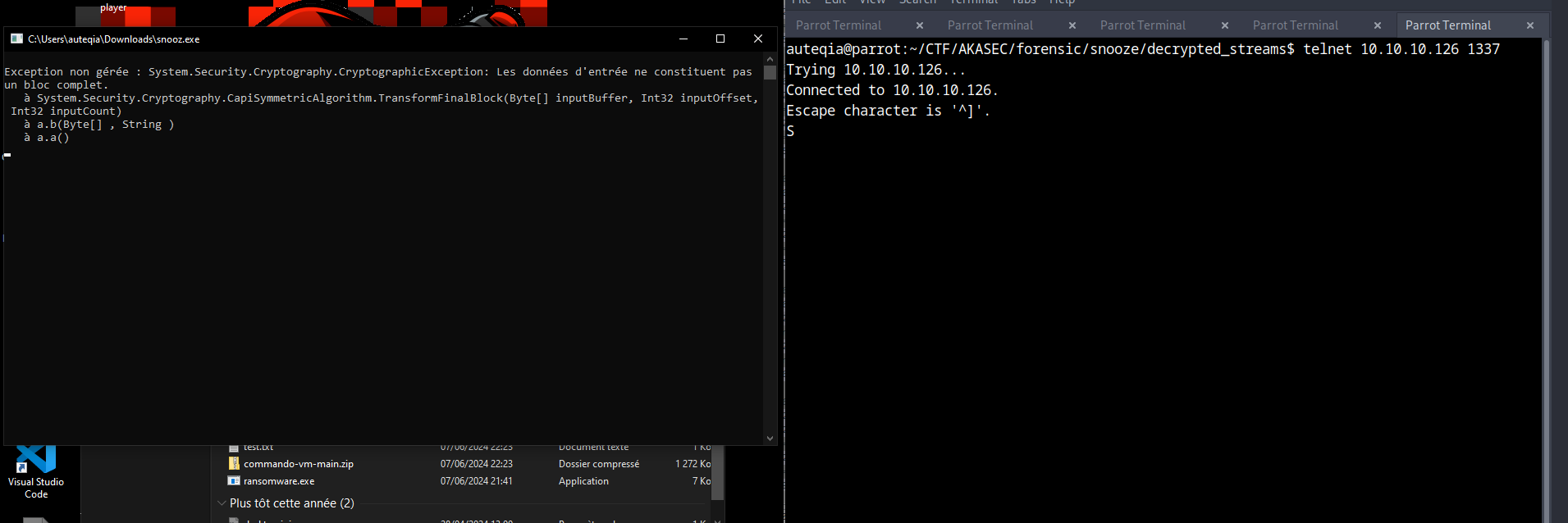
yess!! it works !! but the cmd close himself after the first char
memory dump of snooz.exe
To be viewed by GIMP, you need to rename your file with the extension .data
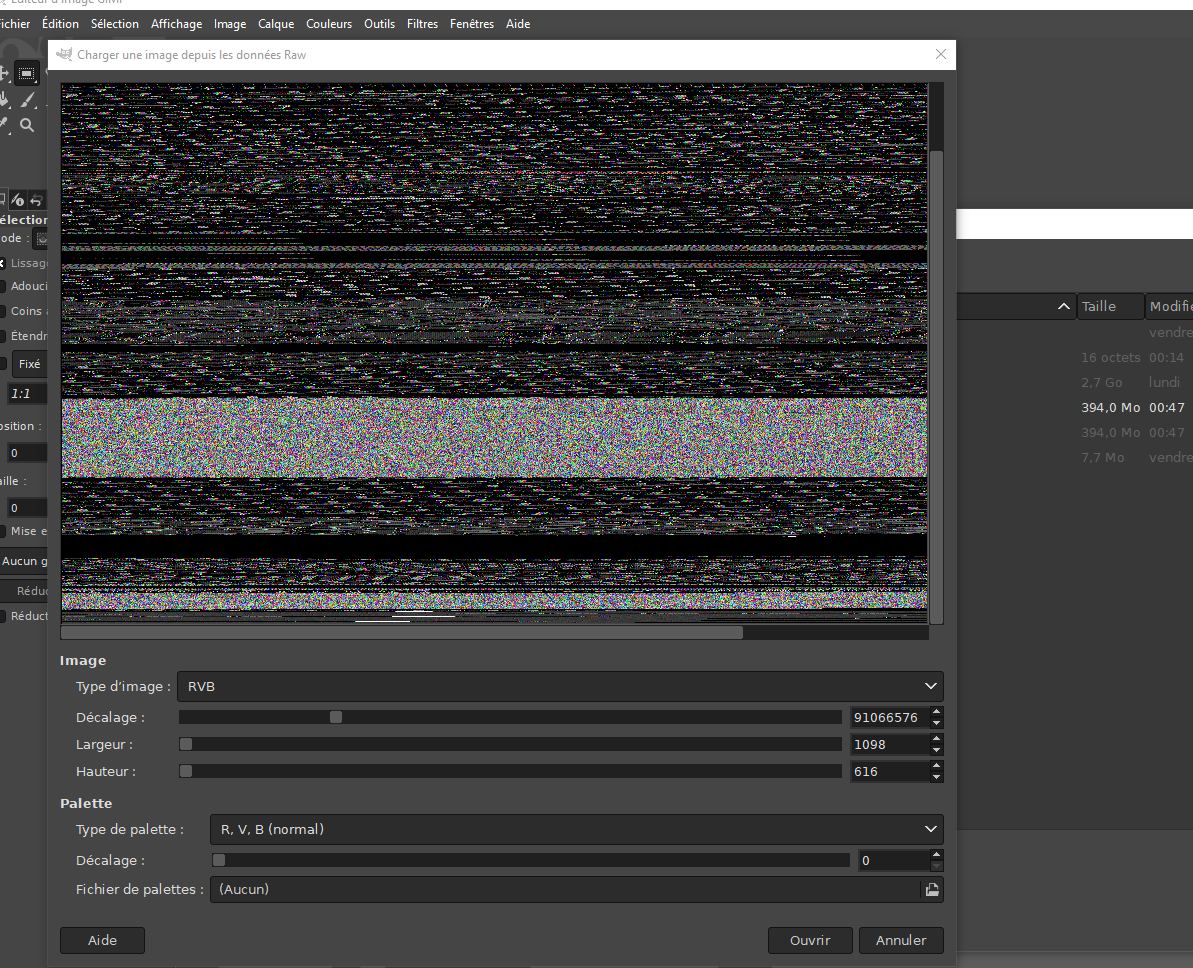
pure suffering
memory dump of notepad.exe
cp pid.3608.dmp notepad.data
AFTER A WHILE
I juste started to see AT OFFSET 0 the notepad.exe view. So i continued with pain
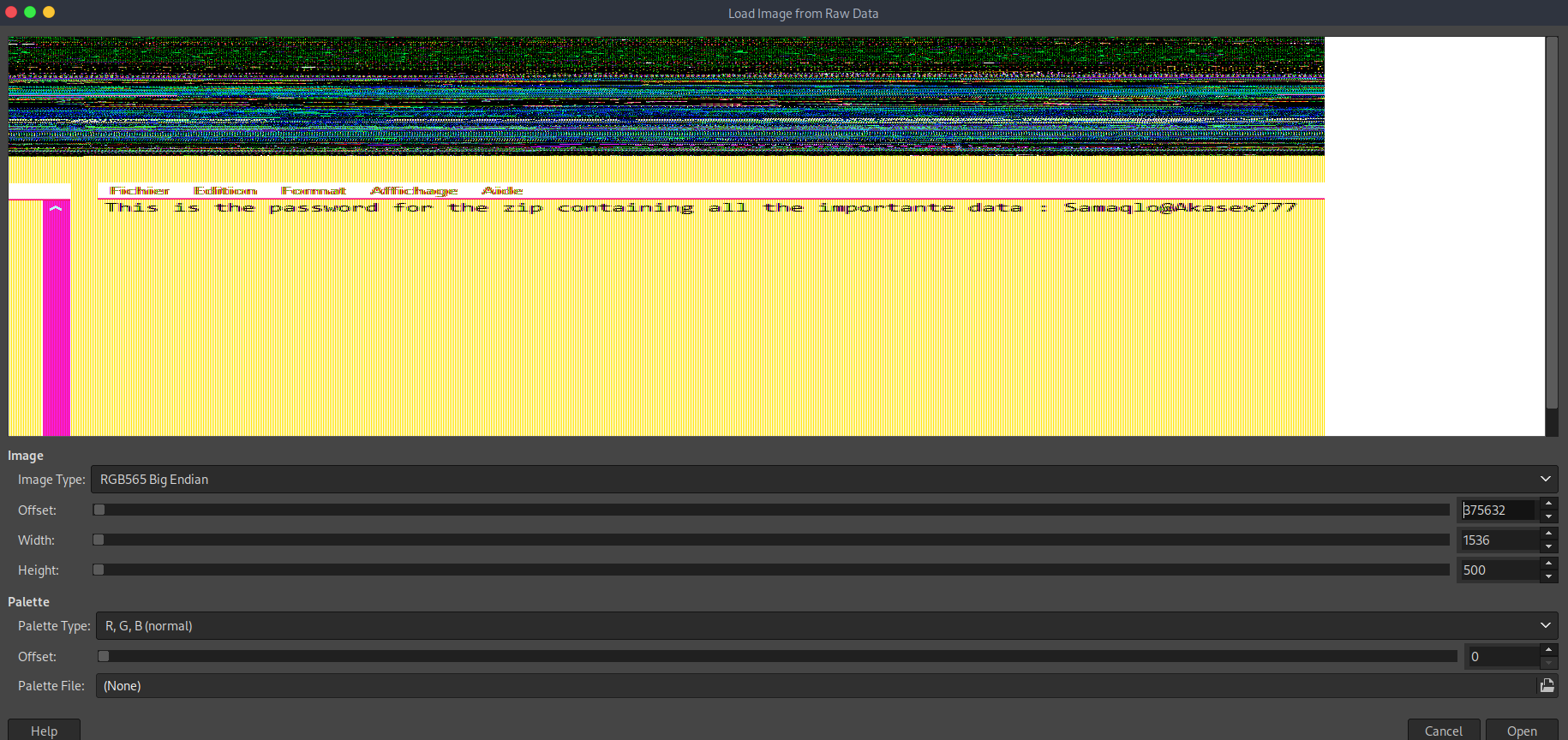
After a really really long and painfull ajustments, we can see clearly This is the password for the zip containing all the importante data : Samaqlo@Akasex777
another solution way more easy: I tried several strings command
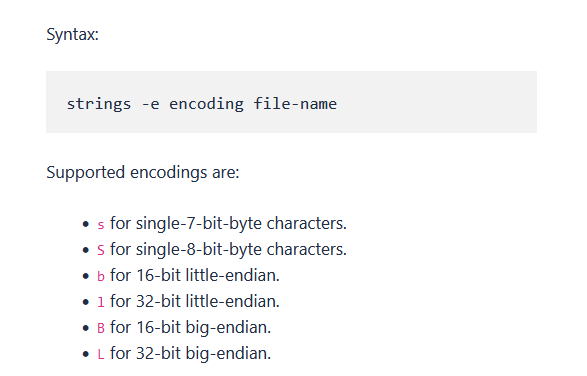
strings -e l pid.3608.dmp - -e : Select the endianness, in this case 16 bits
- it also works with
b,
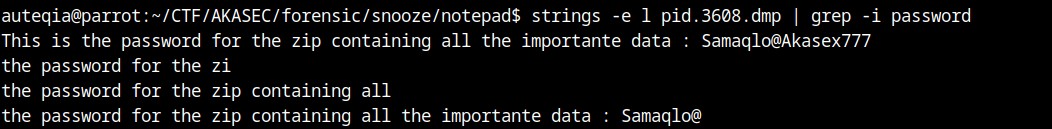
for some reason, it works with a certain encoding, maybe notepad.exe stores non-saved char in another endianness. Good2know for next CTF or challenges that I would like to make
So, we have a password, let’s open up the zip file !
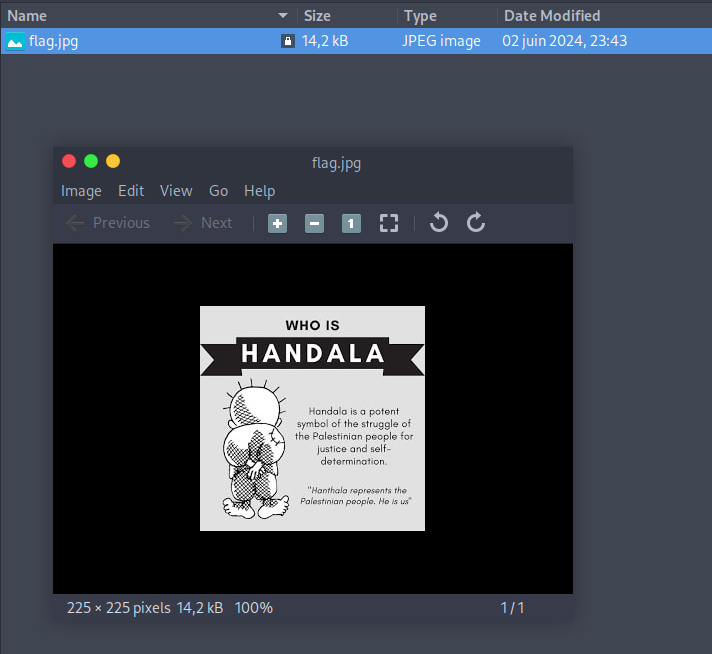
ok that’s not what I expected, but free 🇵🇸
JPEG file
strings
nothing :(
binwalk
aperisolve
Nothing :(
stegoveritas
sudo docker run -it --rm -v $(pwd):/mnt bannsec/stegoveritas
nothing good….
I was blocking here. So i didn’t validate the challenge (because of stegano???) In term of stegano, when I have tried Stegoveritas and Aperisolve, I can’t really do more on JPEG file….
So i waited the write up in order to see what’s going on behind this image. I discovered the tool stegseek ! A steghide cracker, really usefull.
So let’s run it
stegseek
wget https://github.com/RickdeJager/stegseek/releases/download/v0.6/stegseek_0.6-1.deb
sudo apt install ./stegseek_0.6-1.deb
stegseek flag.jpg 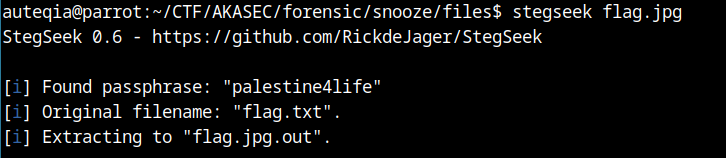
So a flag.txt file was hidding in the flag.jpg behind the password palestine4life.
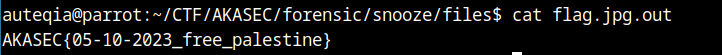
Finally the flag. It was a hard challenge but really fun.
AKASEC{05-10-2023_free_palestine} 🇵🇸
GG to World Wide Flags that first blooded us and I took their solution for the steganography part