AKASEC2024 - Sussy
Something Fishy’s Going on in Our Network
Author : d33znu75
Attachment : packet.pcapng insérer le pcap du challenge
PCAP
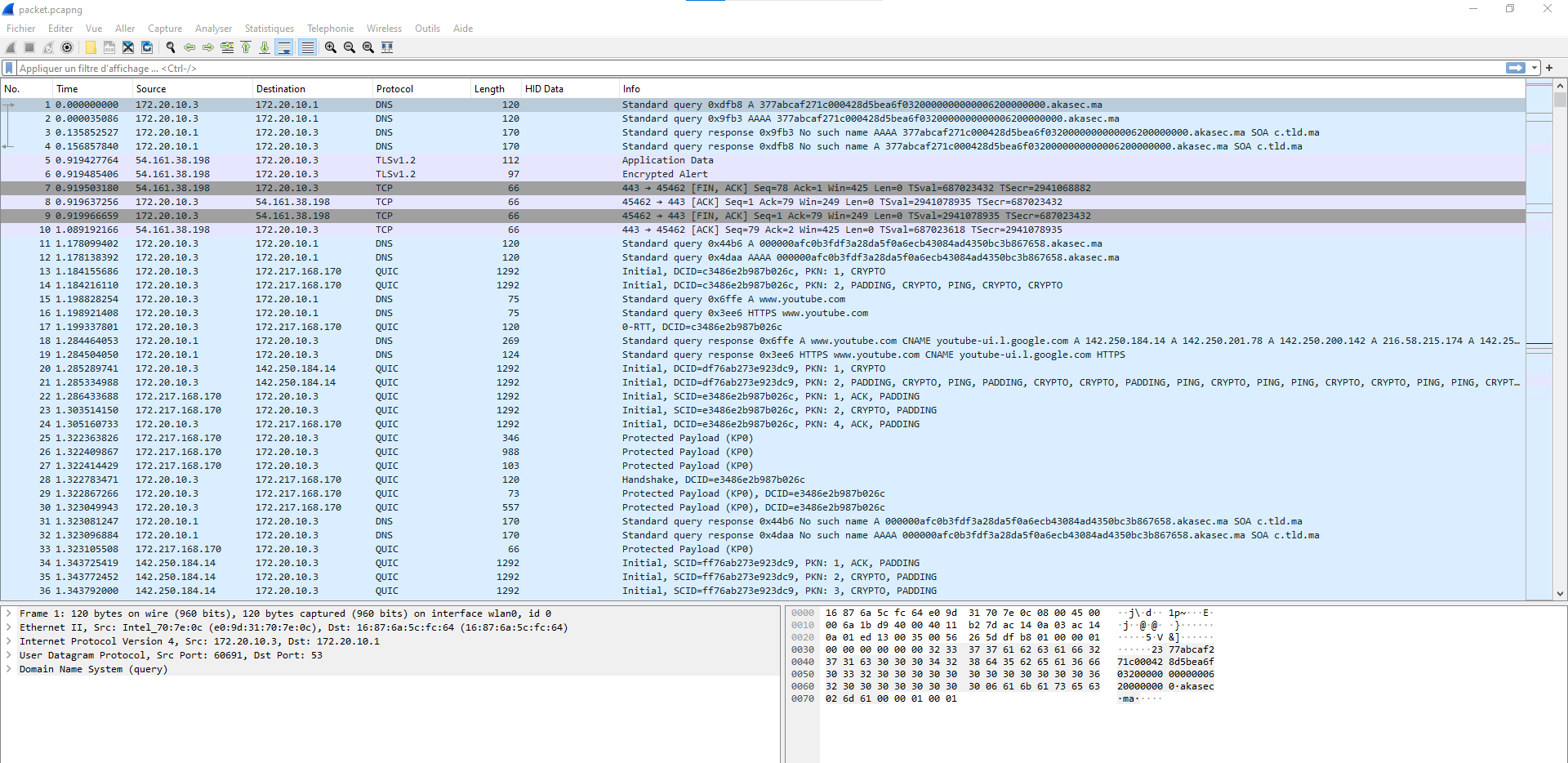
Right after opening the pcap file, there’s something strange in the dns queries.
2000000afc0b3fdf3a28da5f0a6ecb43084ad4350bc3b867658.akasec.ma looks pretty sussy, let’s apply a filter :
frame.len == 120 && ip.src == 172.20.10.3 && dns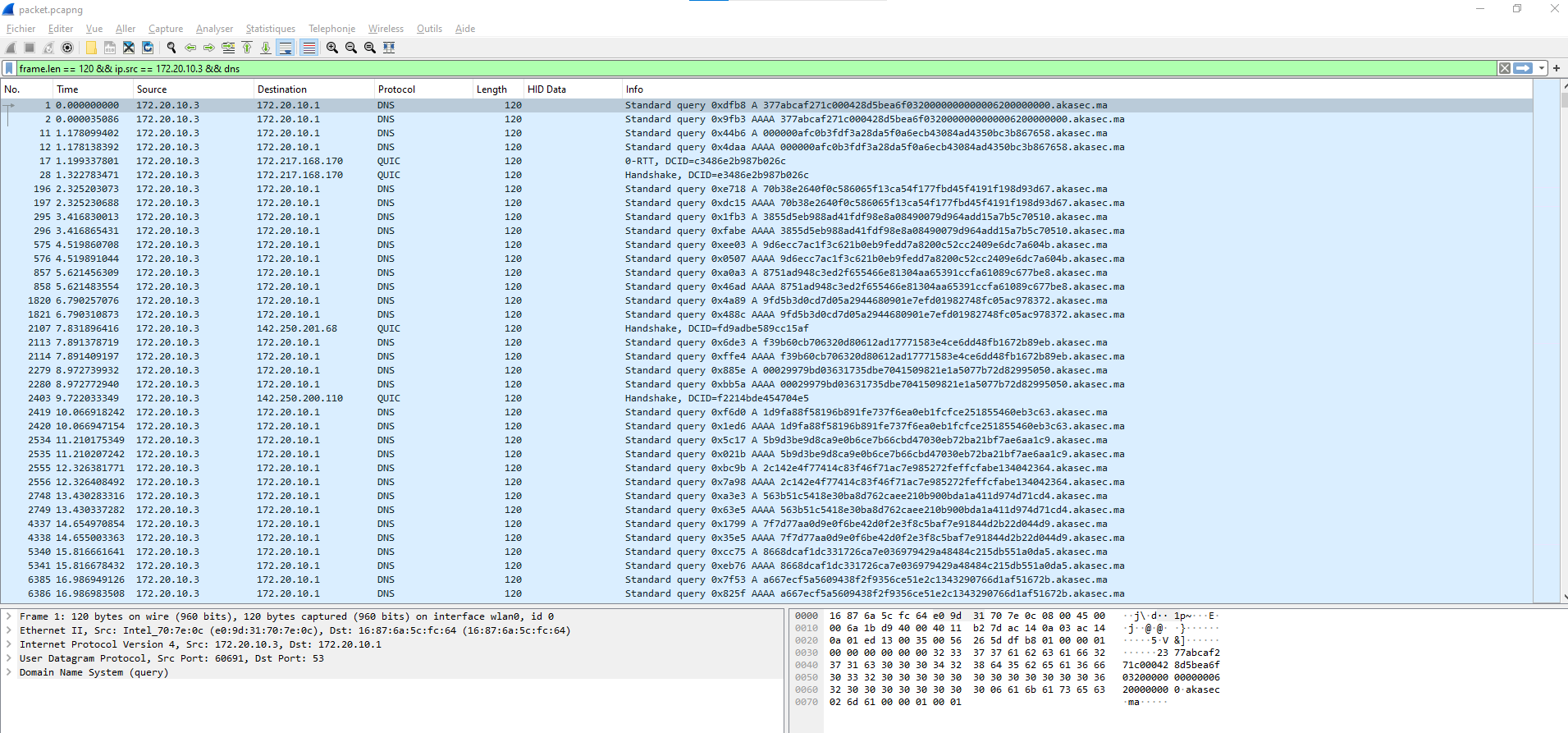
Fine, there’s definitly something suspicious on the network. It looks like DNS exfiltration. Let’s extract all the queries.
Extraction
In this part, I’m gonna use zeek to extract the fields that I need. Zeek can be used with docker, so in case of you don’t have docker :
sudo apt install docker.ioPull the zeek image
sudo docker pull zeek/zeekLet’s run the docker with share volume, for our host it will be the current directory $(pwd) and for our docker it will be /mnt. Make sure you have your pcap file in the working directory
sudo docker run -it -v $(pwd):/mnt zeek/zeekIn the container, let’s run this command in order to extrat all the information in differents log files :
zeek -r capture.pcapAnd so, there’s dns.log that gives us all the information about DNS, so let’s cut the query field and grep on akasec, like we’ve seen in Wireshark.
cat dns.log | zeek-cut query | grep akasec > sussyNow, we can print our sussy file, but the queries are logged twice. This is becasue the queries and responses are logged. In order to cut them, we can use sed to print one line of two :
sed 'n;d' sussy > sussybetterWe need to cut the akasec.ma domain name, so with sed (again)
sed -i 's/\.akasec\.ma//g' sussybetterLet’s go to CyberChef and upload our sussybetter file, and select the From Hex recipe
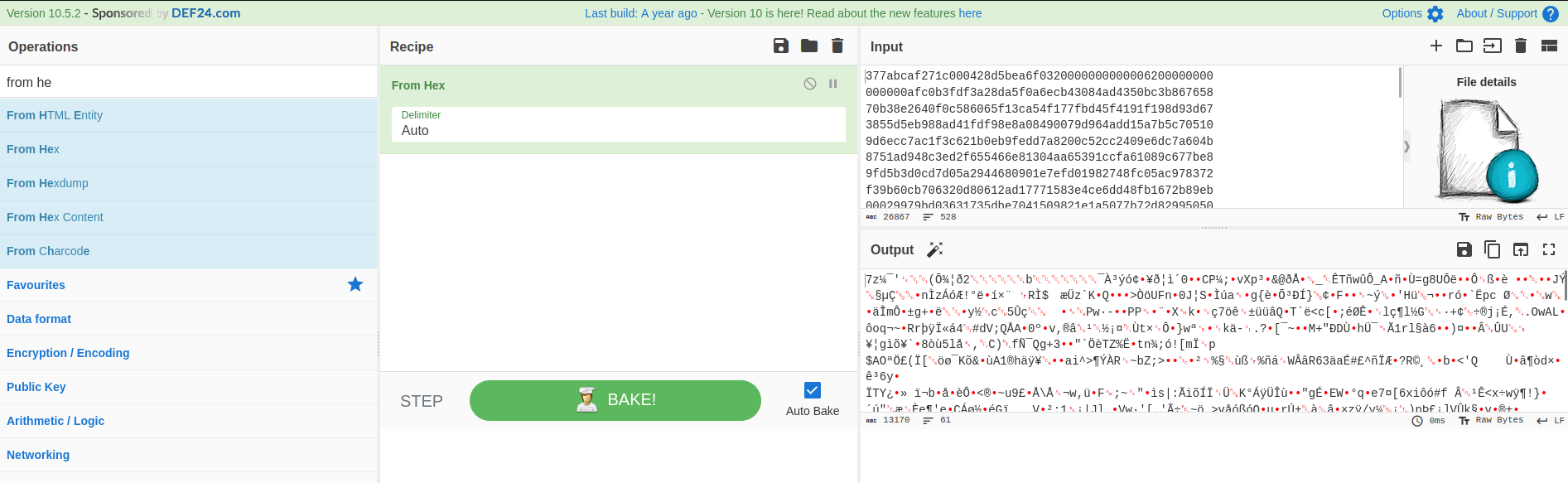
As we can see, there’s a pretty cool magic byte in the ouptut that says we have found a .7z file !! Let’s download it directly in CyberChef
Let’s try to open it
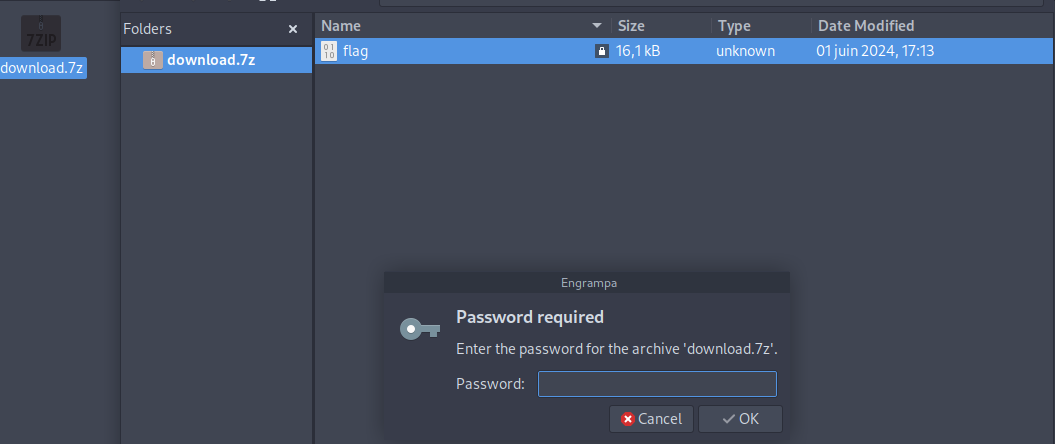
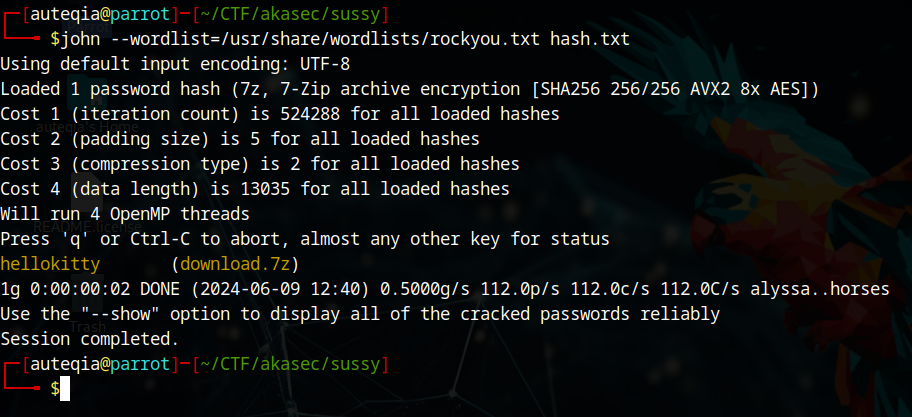
It requires a password, but we don’t have it. Let’s crack it hehehe
Take the fingerprint :
7z2john download.7z > hash.txtAnd crack it using the rockyou :
john --wordlist=/usr/share/wordlists/rockyou.txtbingo we found it : hellokitty
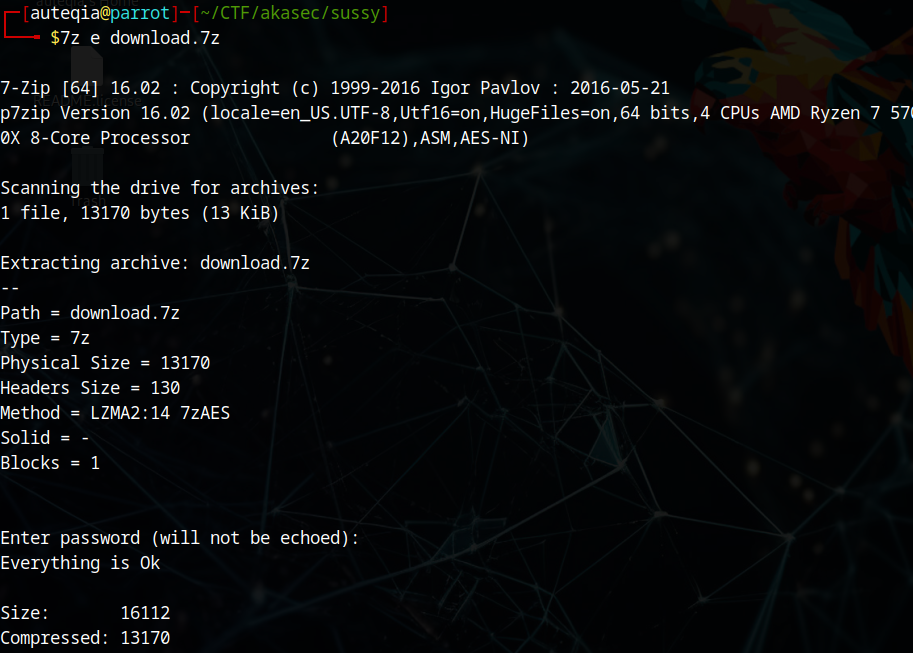
Let’s unzip it
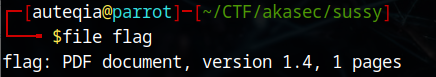
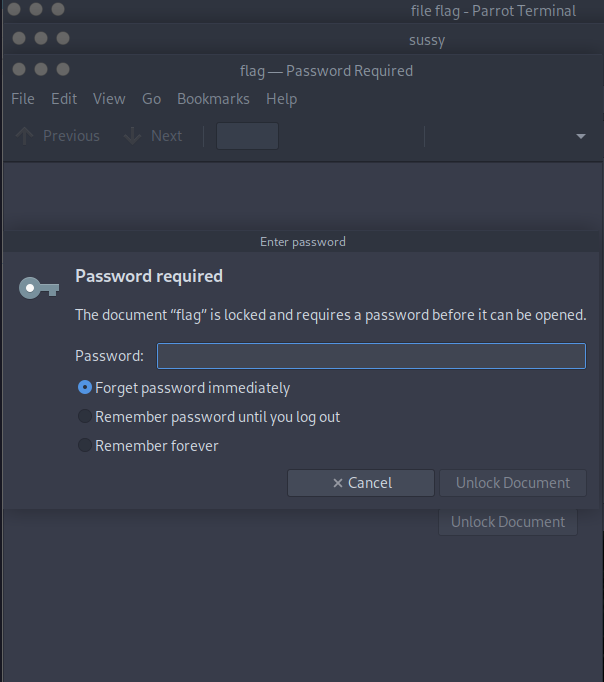
A new password is required, so let’s crack it again
pdf2john flag > pdfhash.txt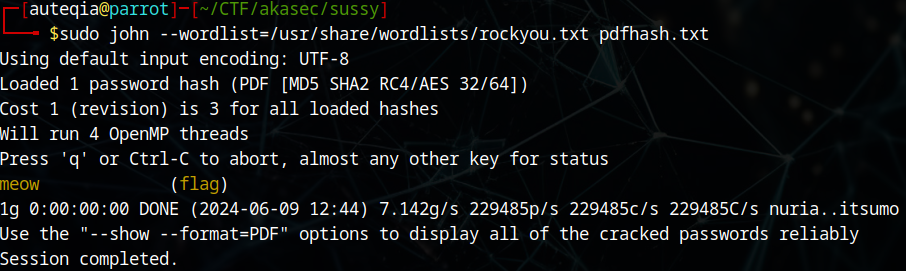
It was really fast, the password is meow :)
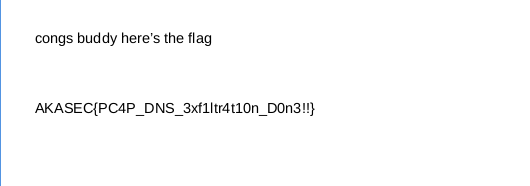
And then we got the flag !
Flag : AKASEC{PC4P_DNS_3xf1ltr4t10n_D0n3!!}