DEADSEC2024 - Forgotten Password
I was going to create this extremely easy forensics challenge for you, but accidentally used the flag as the password when I encrypted the archive. This flag is now deleted, and since it is not possible to brute-force it, I guess that means this challenge can no longer be solved, or can it?
The script that have been used to generate the zip and the ISO is included
content of the archive
7z l challenge.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,4 CPUs AMD Ryzen 7 5700X 8-Core Processor (A20F12),ASM,AES-NI)
Scanning the drive for archives:
1 file, 574 bytes (1 KiB)
Listing archive: challenge.zip
--
Path = challenge.zip
Type = zip
Physical Size = 574
Date Time Attr Size Compressed Name
------------------- ----- ------------ ------------ ------------------------
2024-07-25 21:46:32 ..... 53248 382 challenge.iso
------------------- ----- ------------ ------------ ------------------------
2024-07-25 21:46:32 53248 382 1 filesgenerate.py
from io import BytesIO
import os
import subprocess
import pycdlib # pip install pycdlib
try:
FLAG = open("flag.txt","r").read()
except FileNotFoundError:
FLAG = "fake_flag_for_testing"
iso = pycdlib.PyCdlib()
iso.new(interchange_level=4)
iso.add_fp(BytesIO(FLAG.encode()), len(FLAG), '/flag.txt;1')
iso.write('challenge.iso')
iso.close()
subprocess.check_output(["zip", "challenge.zip", "challenge.iso", "-P", FLAG])Encryption method
We lost the password! But if we manage to do a Plain-text attack, we may end up recovering the zip password
7z l -slt challenge.zip | grep -i method
Method = ZipCrypto DeflateIt’s indeed ZipCrypto, which is vulnerable to this kind of attack :)
Playground
Test time ! Let’s use the python script in order to create an unencrypted ISO to see if there is pattern in ISO file.
fake flag
Create a fake flag file
echo "DEAD{feur}" > flag.txtremove the zip encryption
Change the last line of the program to remove the -P option
subprocess.check_output(["zip", "challenge.zip", "challenge.iso"])This creates challenge.zip with unencrypted challenge.iso file inside
run the program
Install the lib
pip install pycdlib
#or
sudo apt install python3-pycdlibpython3 generate.pyls -l
[...]
-rw-r--r-- 1 auteqia auteqia 52K 27 juil. 16:50 challenge.isostrings
strings challenge.iso
[...]
2024072816503400
[...]
0000000000000000
2024072816503400
[...]
[...]
CD001
flag.txt;1
DEAD{feur}As we can see, there’s mainly null bytes in this ISO, let’s hexedit
xxd

As we can see, there’s a few null bytes, starting from offset 0x80 to 0xa0. In the plain text attack tool bkcrack, we can specify an offset and the data from this offset.
Every time I used the generate.py, the 0x90 offet was full of null bytes
bkcrack bkcrack bkcrack everywhere
Let’s download the executable of bkcrack on Github
find the keys
wget https://github.com/kimci86/bkcrack/releases/download/v1.7.0/bkcrack-1.7.0-Linux.tar.gz
gzip -d bkcrack-1.7.0-Linux.tar.gz
tar -xvf bkcrack-1.7.0-Linux.tar
cd bkcrack-1.7.0-Linux/beware of taking the original encrypted file and not our test files !
/bkcrack -C challenge.zip -c challenge.iso -x 90 000000000000000000000000
bkcrack 1.7.0 - 2024-05-26
[17:05:48] Z reduction using 4 bytes of known plaintext
100.0 % (4 / 4)
[17:05:48] Attack on 1400873 Z values at index 87
Keys: 6b13ebc5 cc0be8ac 709e18f9
25.2 % (353442 / 1400873)
Found a solution. Stopping.
You may resume the attack with the option: --continue-attack 353442
[17:13:25] Keys
6b13ebc5 cc0be8ac 709e18f9Yes we got something !!!
bkcrack help section :
-x, --extra <offset> <data> Additional plaintext in hexadecimal starting
at the given offset (may be negative)0x90(hex notation) because before there’s a risk that the ISO has some none null-bytes.
use the keys
./bkcrack -C challenge.zip -k 6b13ebc5 cc0be8ac 709e18f9 --change-password decrypted.zip brandnewpassword
[17:16:23] Writing unlocked archive decrypted.zip with password "brandnewpassword"
100.0 % (1 / 1)
Wrote unlocked archive.looks like we got something !
Let’s enter brandnewpassword as we set it before
And here’s the flag !
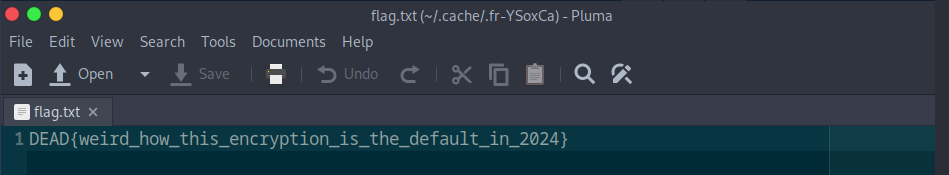
The flag !!
DEAD{weird_how_this_encryption_is_the_default_in_2024}really good challenge !