Sherlock - Operation Dream Job
You are a junior threat intelligence analyst at a Cybersecurity firm. You have been tasked with investigating a Cyber espionage campaign known as Operation Dream Job. The goal is to gather crucial information about this operation.
First, we start with a file IOCs.txt:
1. 7bb93be636b332d0a142ff11aedb5bf0ff56deabba3aa02520c85bd99258406f
2. adce894e3ce69c9822da57196707c7a15acee11319ccc963b84d83c23c3ea802
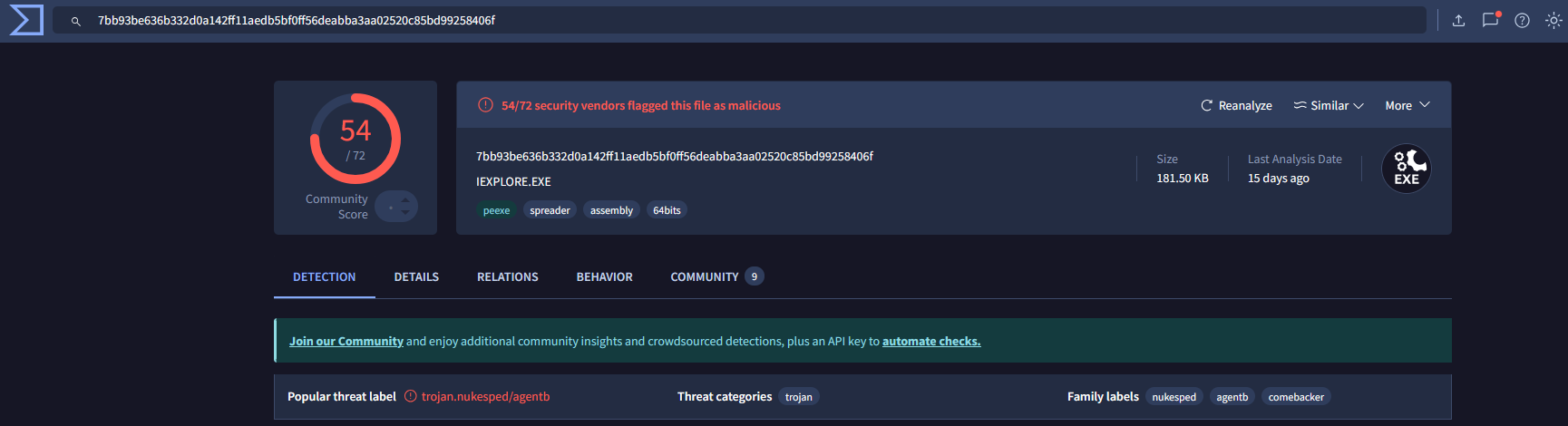
3. 0160375e19e606d06f672be6e43f70fa70093d2a30031affd2929a5c446d07c1 In VirusTotal (7bb93be636b332d0a142ff11aedb5bf0ff56deabba3aa02520c85bd99258406f):
adce894e3ce69c9822da57196707c7a15acee11319ccc963b84d83c23c3ea802:
0160375e19e606d06f672be6e43f70fa70093d2a30031affd2929a5c446d07c1:
Who conducted Operation Dream Job?
By using VirusTotal, we can see in the Community Tab that the IOCs are related to the North Korean hacker group name Lazarus.
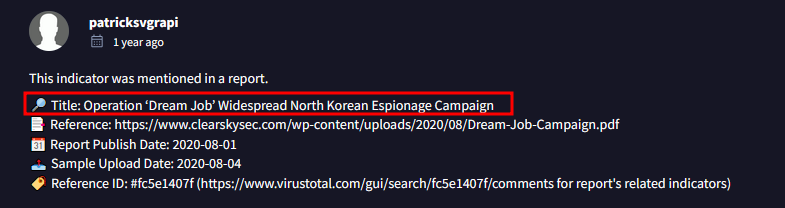
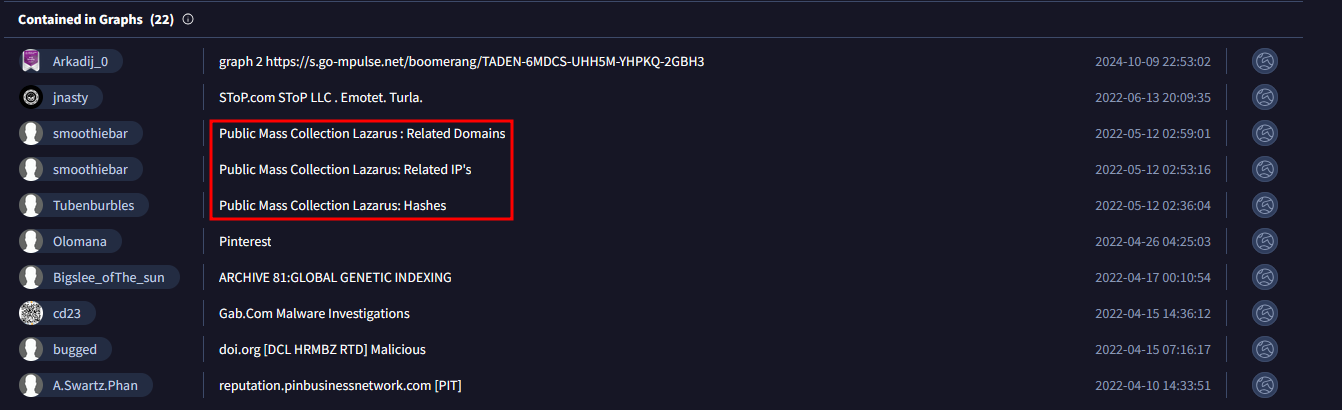
Then, on the MITRE website, we can see that the Operation Dream Job is well documented and related to Lazarus group:
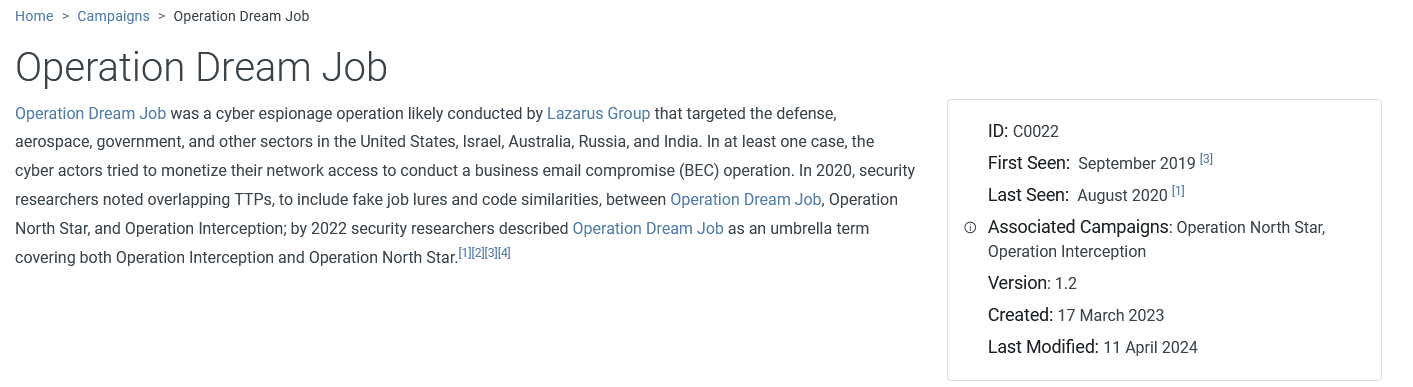
Lazarus Group
When was this operation first observed?
As previously mentioned on the MITRE website, the first appearance is in September 2019
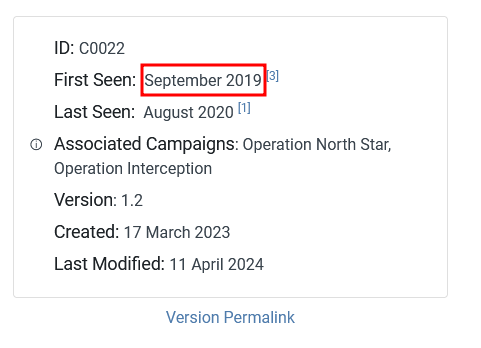
September 2019
There are 2 campaigns associated with Operation Dream Job. One is Operation North Star, what is the other?
Still on the MITRE website, we can see that the other name is Operation Interception
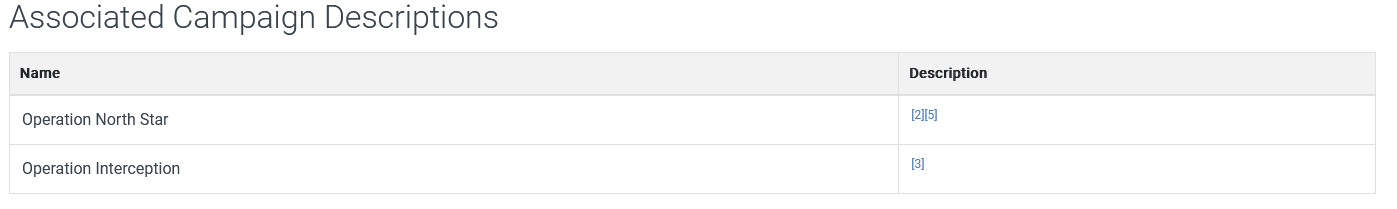
Operation Interception
During Operation Dream Job, there were the two system binaries used for proxy execution. One was Regsvr32, what was the other?
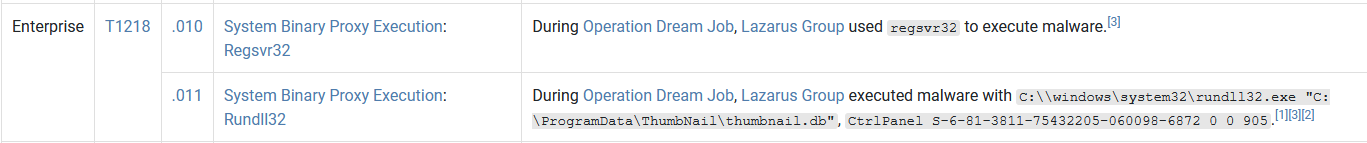
Rundll32
What lateral movement technique did the adversary use?
Inside the ATT&CK Navigator, we can see that the Lateral Movement technique used is Internal Spearphishing:
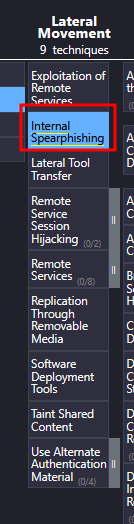
Internal Spearphishing
What is the technique ID for the previous answer?
For this one, we just have to hover the Internal Spearphishing on the MITRE ATT&CK Navigator:
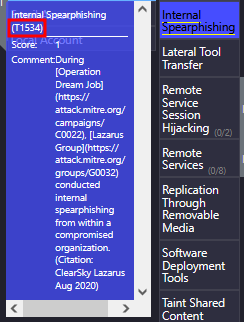
T1534
What Remote Access Trojan did the Lazarus Group use in Operation Dream Job?
Still on the MITRE website:
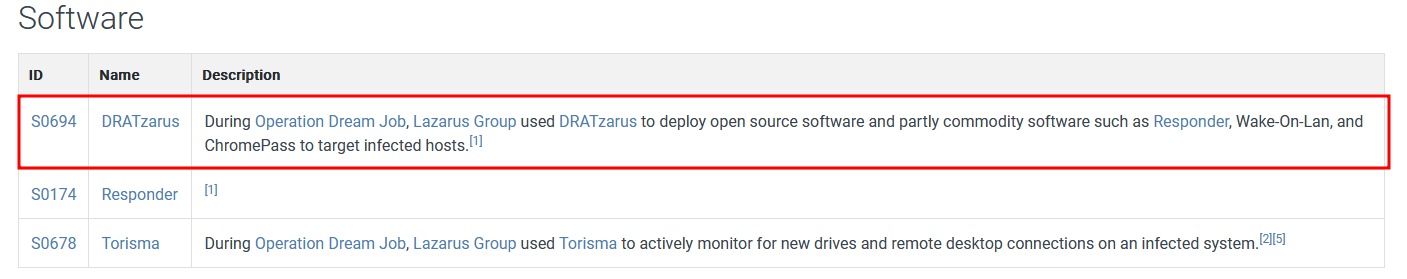
DRATzarus
What technique did the malware use for execution?
Under the Execution, we can see the techniques highlighted in blue and the one that we seek: Native API:
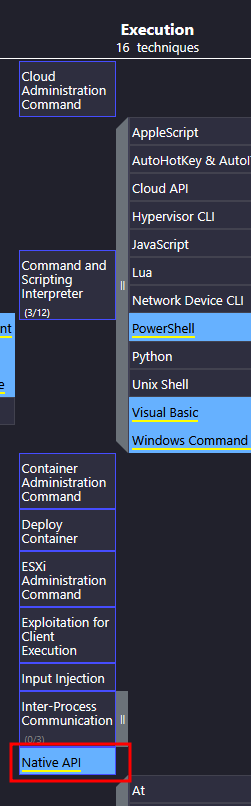
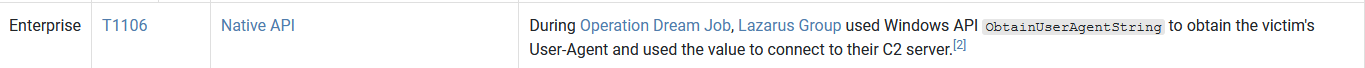
Native API
What technique did the malware use to avoid detection in a sandbox?
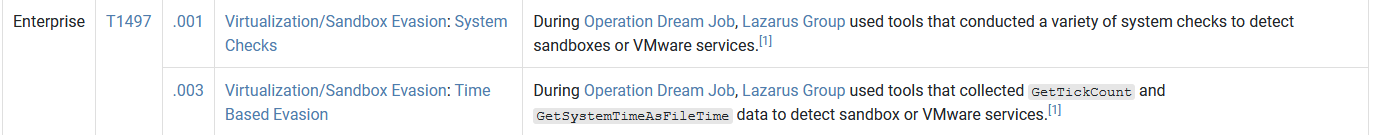
Time Based Evasion
To answer the remaining questions, utilize VirusTotal and refer to the IOCs.txt file. What is the name associated with the first hash provided in the IOC file?
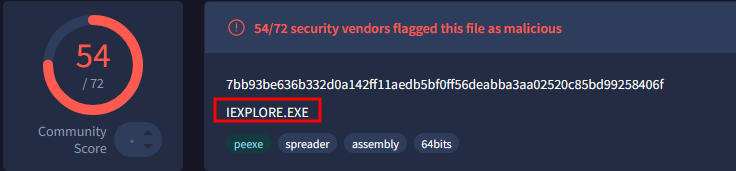
IEXPLORE.EXE
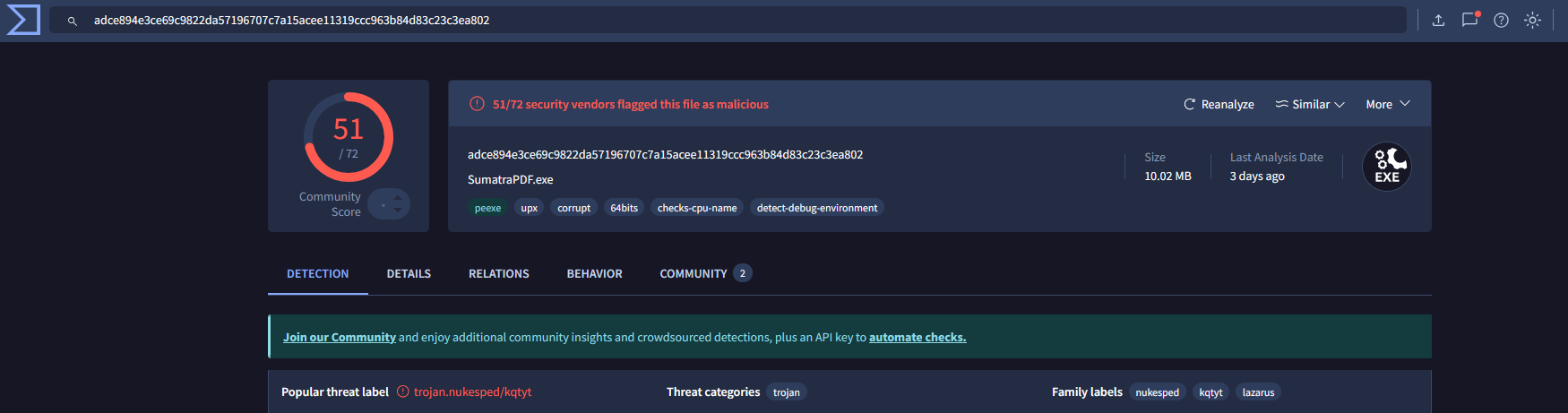
When was the file associated with the second hash in the IOC first created?
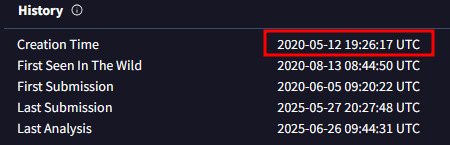
2020-05-12 19:26:17 UTC
What is the name of the parent execution file associated with the second hash in the IOC?
Under the Relation tab:
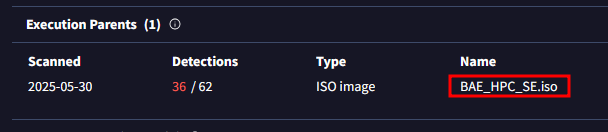
BAE_HPC_SE.iso
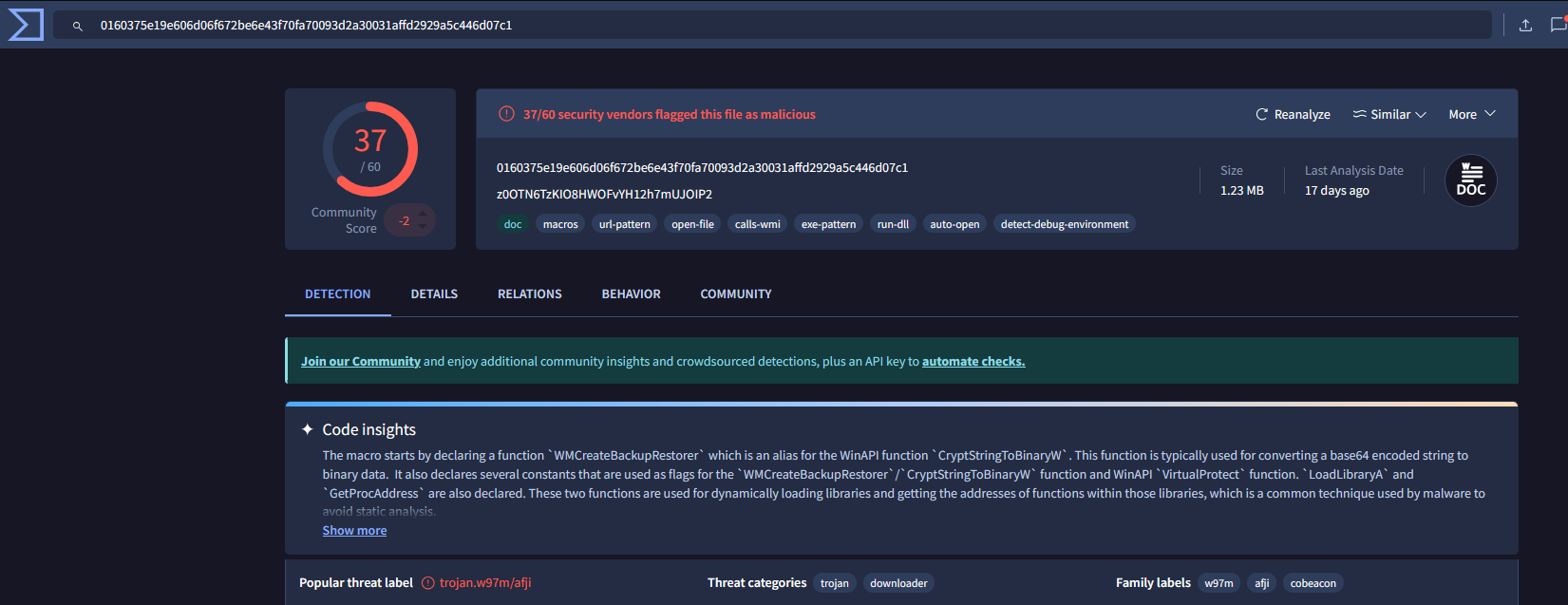
Examine the third hash provided. What is the file name likely used in the campaign that aligns with the adversary’s known tactics?
Under the Details tab:
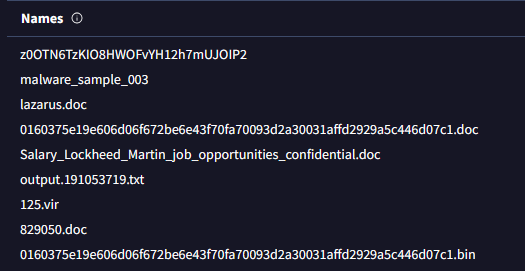
As we can see, every names are suspicious but the Salary_Lockheed_Martin_job_opportunities_confidential.doc took my attention.
A quick Google research leads us to this:
Why this might be our filename? Because as we have seen before, the Operation Dream Job targeted mainly the Aerospace field.
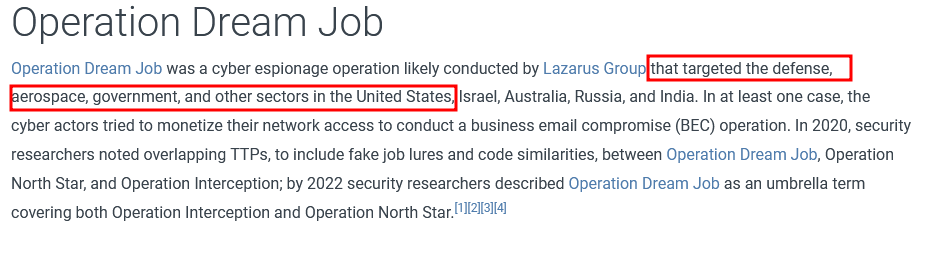
This could have been a filename used in a campaign phishing that targeted the Defense employee.
Salary_Lockheed_Martin_job_opportunities_confidential.doc
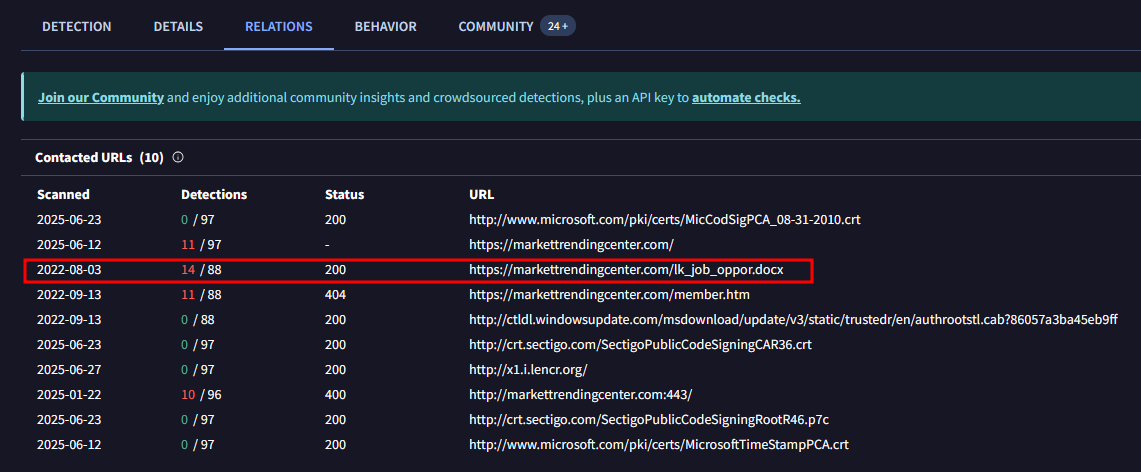
Which URL was contacted on 2022-08-03 by the file associated with the third hash in the IOC file?
Under the Relations tab: