Sherlock - Phantom Check
Which WMI class did the attacker use to retrieve model and manufacturer information for virtualization detection?
First, let’s check at the Get-WMI cmdlet:
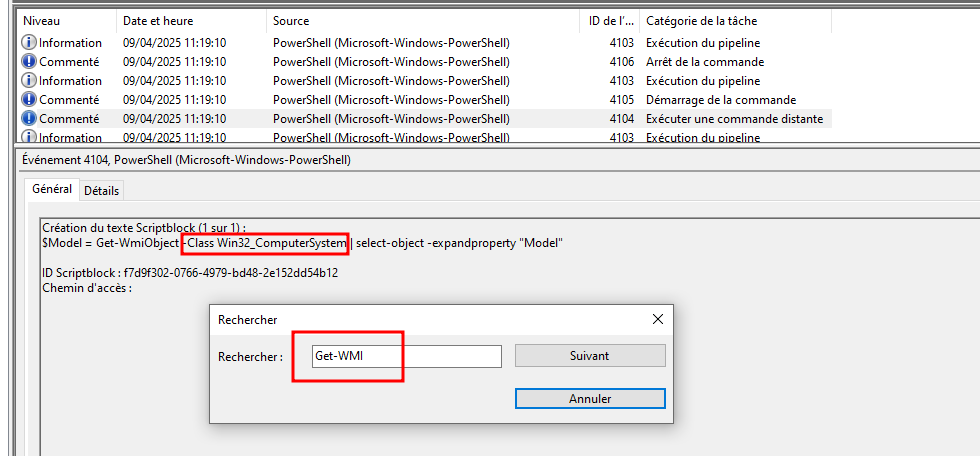
We find the query pretty fast.
Win32_ComputerSystem
Which WMI query did the attacker execute to retrieve the current temperature value of the machine?
Let’s search for further Get-WMIObject commands:
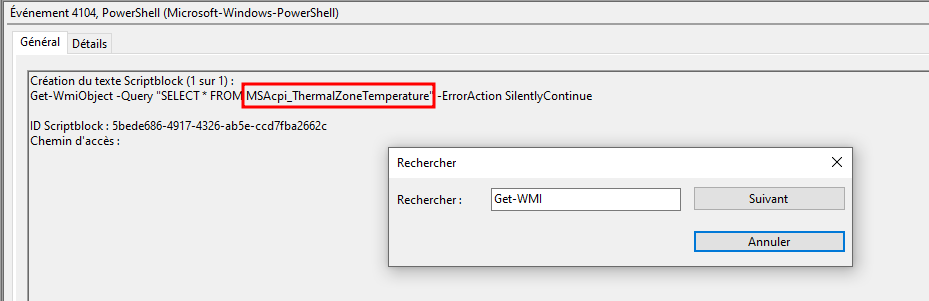
SELECT * FROM MSAcpi_ThermalZoneTemperature
The attacker loaded a PowerShell script to detect virtualization. What is the function name of the script?
We can leverage the event ID 4104 in order to see the PowerShell scripts that have been executed. Inside one of the events, we can see the whole script that checks if the system is virtualized.
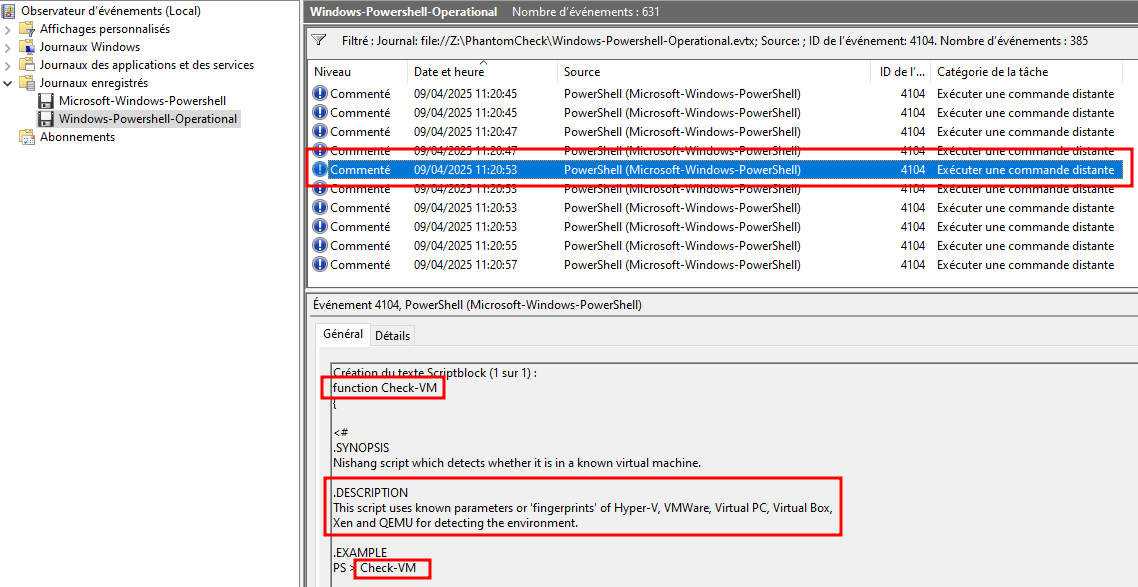
Check-VM
Which registry key did the above script query to retrieve service details for virtualization detection?
Inside the same event, we can scroll down and see that it checks the HKLM:\SYSTEM\ControlSet001\Services registry key to check if the system is virtualized:
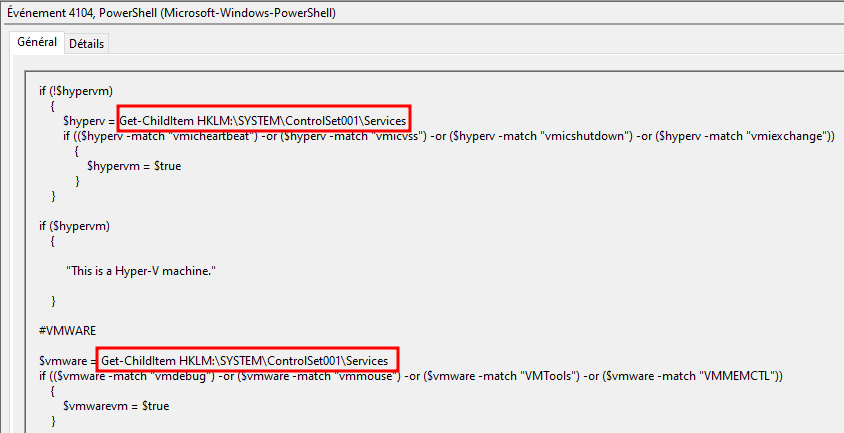
HKLM:\SYSTEM\ControlSet001\Services
The VM detection script can also identify VirtualBox. Which processes is it comparing to determine if the system is running VirtualBox?
Inside the same script, we can see it checks if the vboxservice.exe and vboxtray.exe processes are up and running with the Get-Process cmdlet:
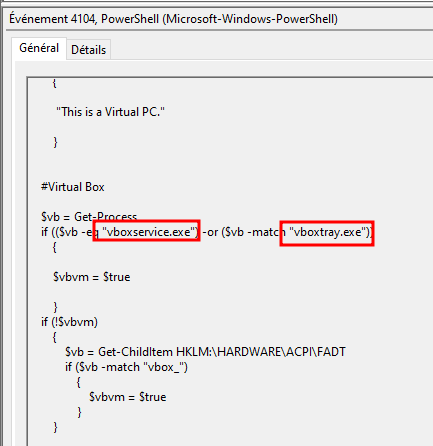
vboxservice.exe, vboxtray.exe
The VM detection script prints any detection with the prefix ‘This is a’. Which two virtualization platforms did the script detect?
Let’s do a basic ctrl+f and search for This is a that have been printed:
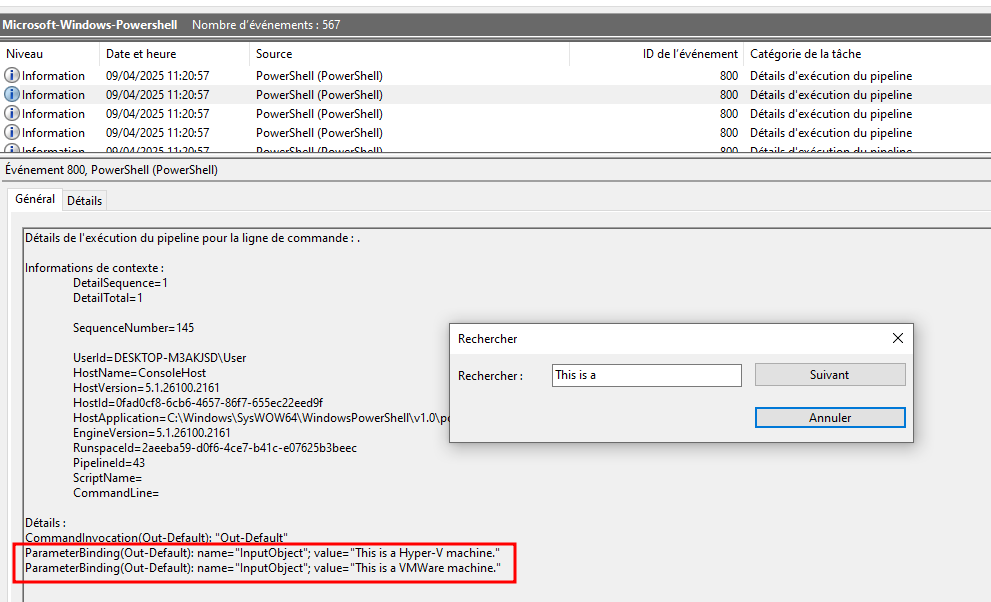
Hyper-V, VMWare