Sherlock - RomCom
Challenge description: Susan works at the Research Lab in Forela International Hospital. A Microsoft Defender alert was received from her computer, and she also mentioned that while extracting a document from the received file, she received tons of errors, but the document opened just fine. According to the latest threat intel feeds, WinRAR is being exploited in the wild to gain initial access into networks, and WinRAR is one of the Software programs the staff uses. You are a threat intelligence analyst with some background in DFIR. You have been provided a lightweight triage image to kick off the investigation while the SOC team sweeps the environment to find other attack indicators..
Difficulty: Very Easy
1. What is the CVE assigned to the WinRAR vulnerability exploited by the RomCom threat group in 2025?
With a simple Google search we can find this:
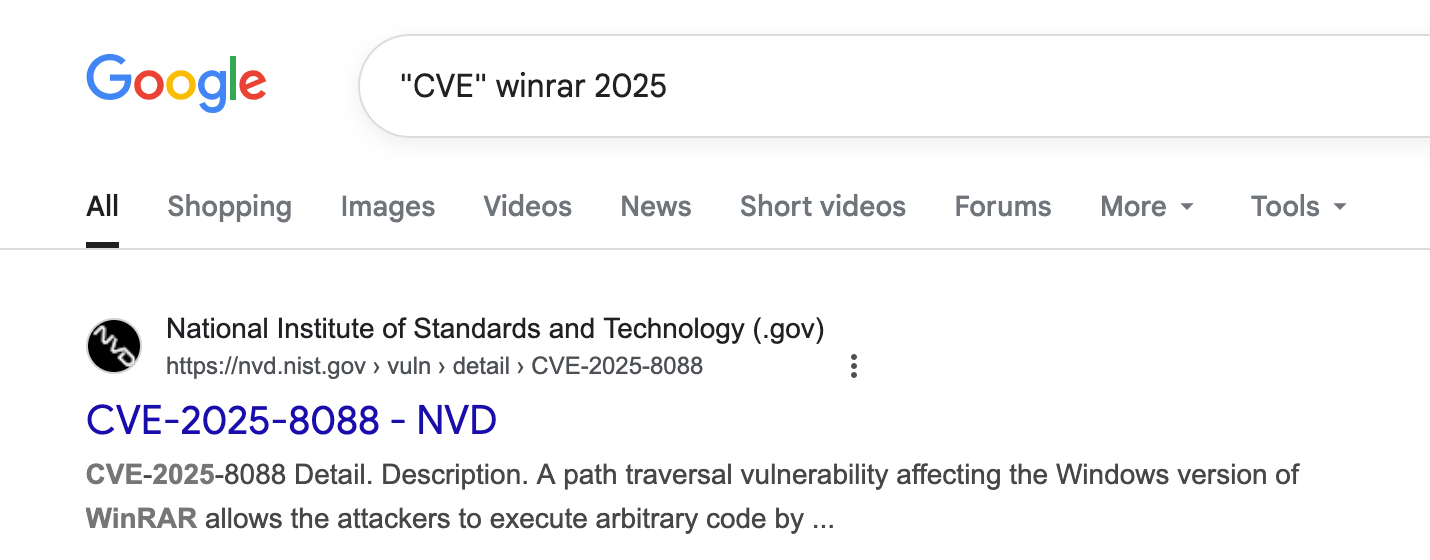
CVE-2025-8088
2. What is the nature of this vulnerability?
Inside the NIST article we can see the Vulnerability Name: Path Traversal.
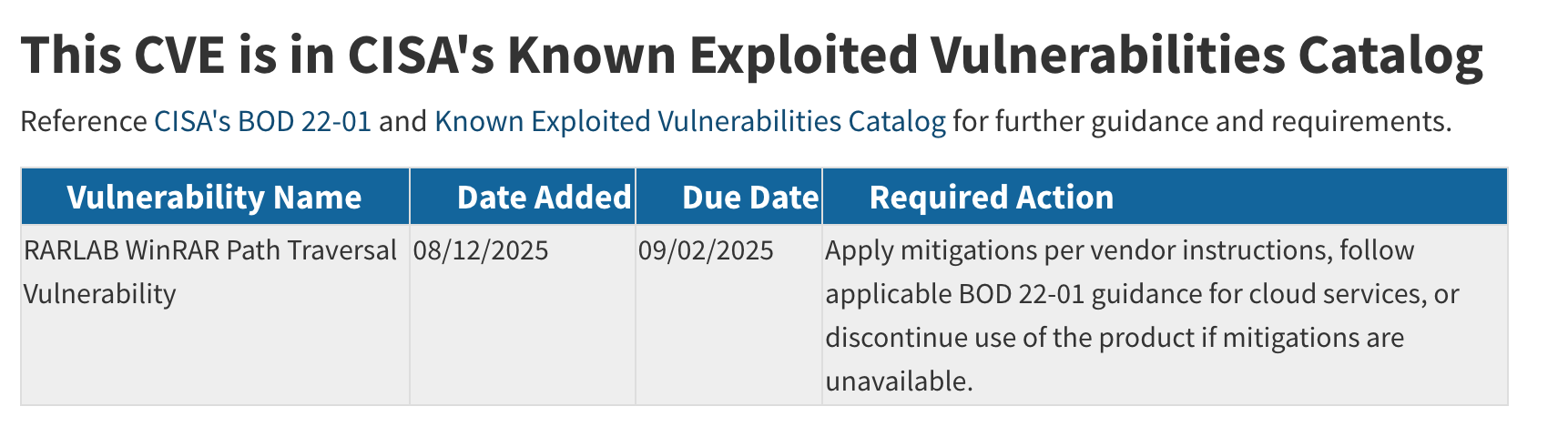
Path Traversal
3. What is the name of the archive file under Susan’s documents folder that exploits the vulnerability upon opening the archive file?
To find the answer, we have to mount the disk image in ArsenalImageMounter (or FTK Imager) and explore the content:
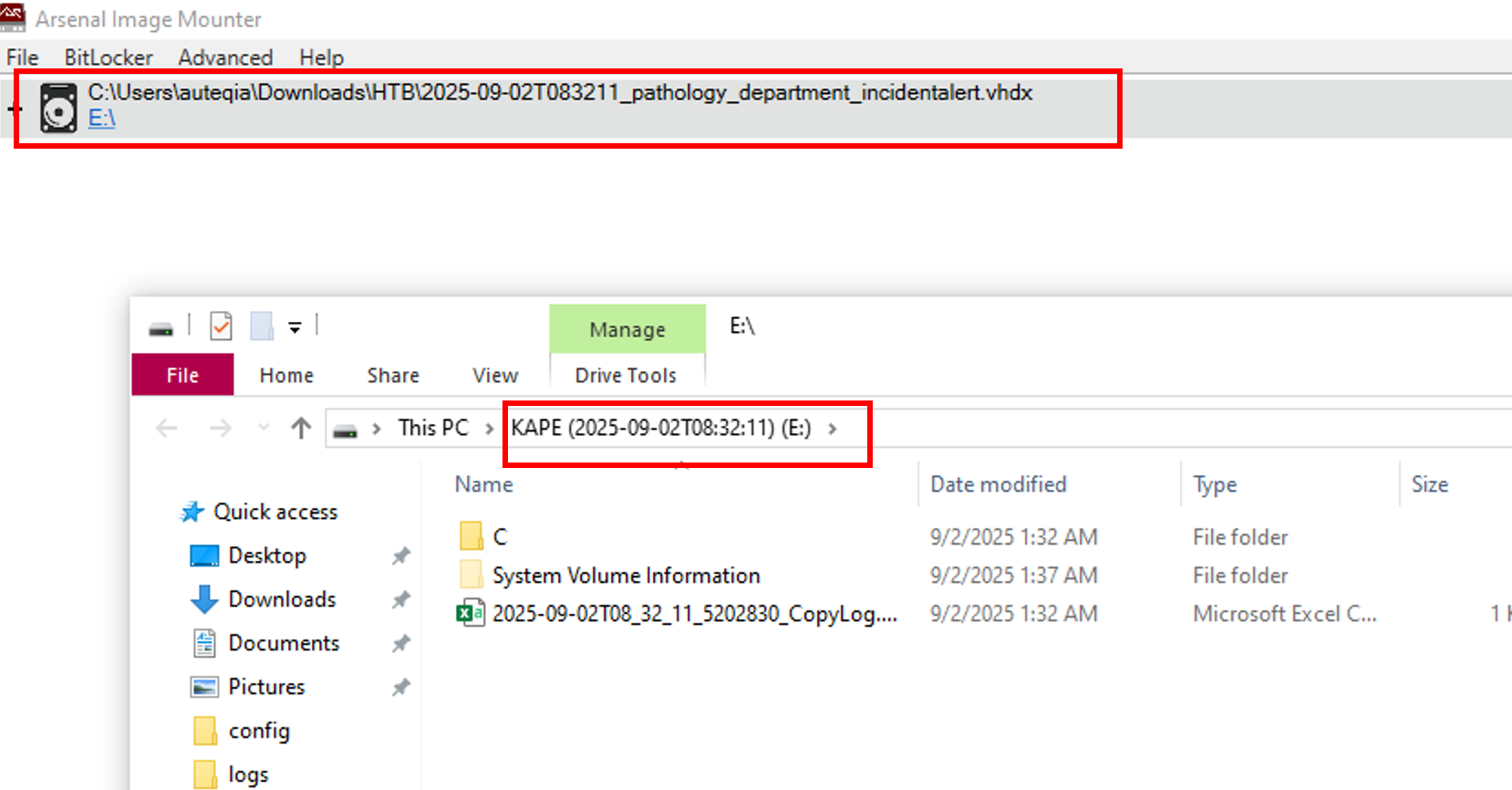
As we can see, this is a KAPE dump. Inside the C folder, we have the $MFTthat will be very useful for our investigation.
Let’s run `MFTecmd:
C:\Tools\MFTECmd\MFTECmd.exe -f 'E:\C\$MFT' --csv .\Downloads\HTB\ --csvf romcom.csvAnd then open it in Timeline Explorer:
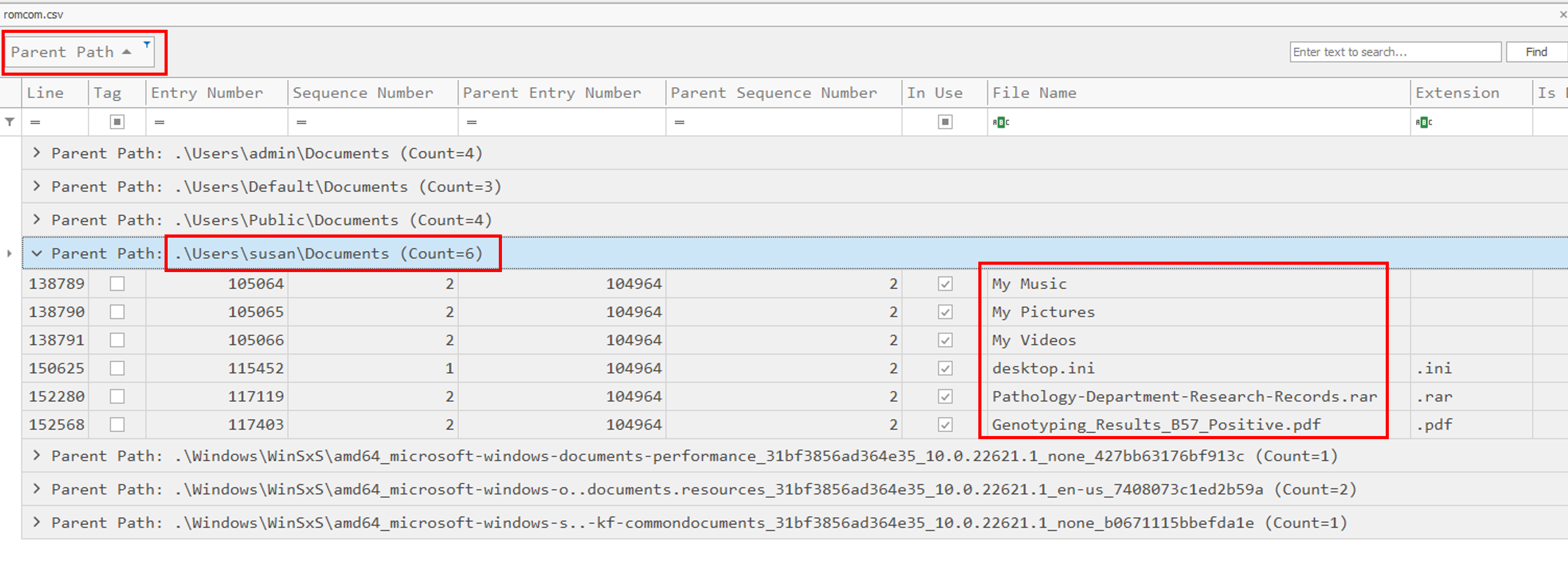
Inside the challenge description, there’s a reference to WinRAR, a well known zip/archive utility. The common extension for a WinRAR file is .rar. We can assume that the Pathology-Department-Research-Records.rar is our file.
Pathology-Department-Research-Records.rar
4. When was the archive file created on the disk?
Still on Timeline Explorer, we can see the Creation Dateof the WinRAR file:
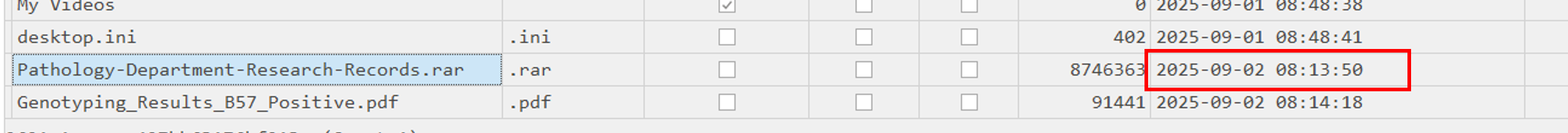
2025-09-02 08:13:50
5. When was the archive file opened?
In order to find out the file opened time, we can seek for the Last Record Change0x10attribute :
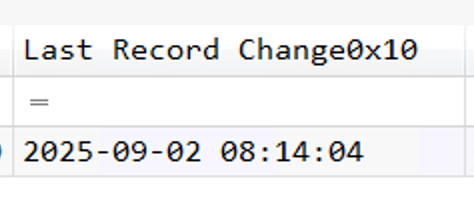
2025-09-02 08:14:04
6. What is the name of the decoy document extracted from the archive file, meant to appear legitimate and distract the user?
Normally the document would be extract under same file path, so we can seek for the files under the .\Users\susan\Documents:
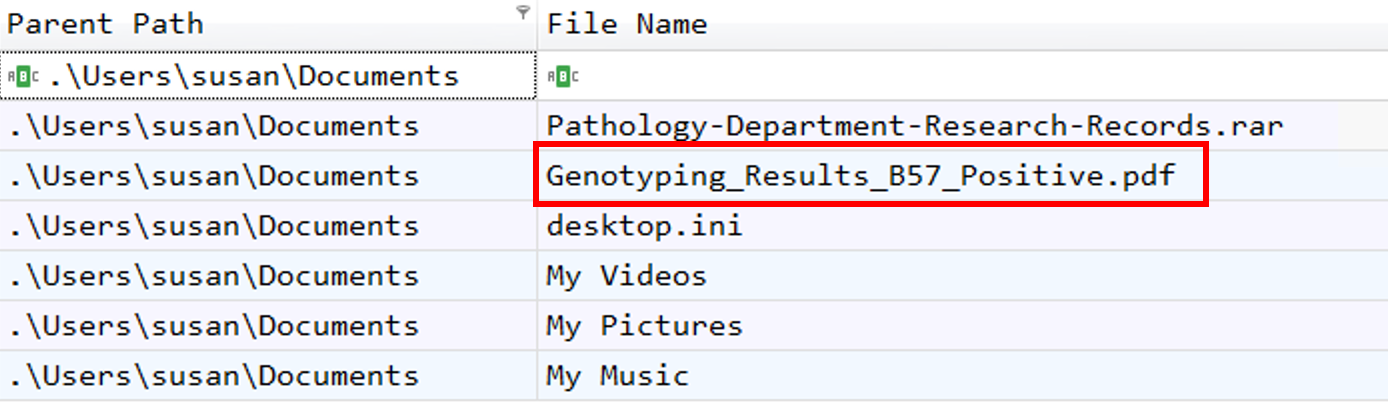
Genotyping_Results_B57_Positive.pdf
7. What is the name and path of the actual backdoor executable dropped by the archive file?
As the backdoor won’t tell out loud “yay I’m here!!” we have to investigate the files that have been created around the archive extract time. We already know the Genotyping_Results_B57_Positive.pdf, we just have to filter on the Created0x10field:
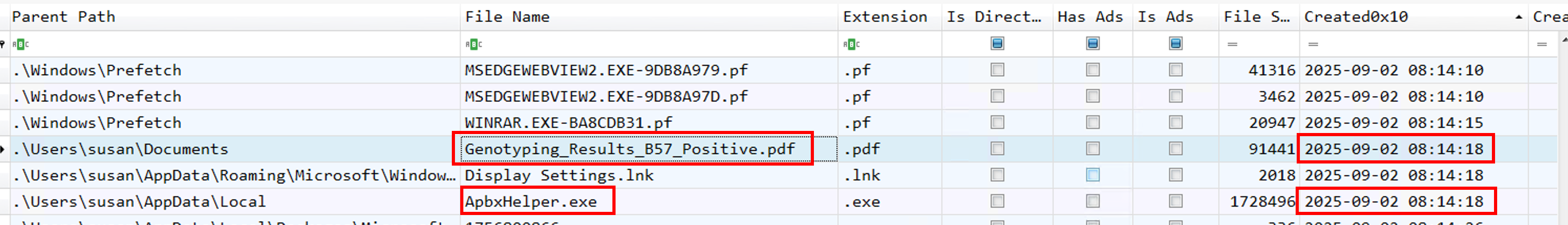
We can assume that the ApbxHelper.exeis suspicious by it’s parent folder and the time it was created.
C:\Users\susan\AppData\Local\ApbxHelper.exe
8. The exploit also drops a file to facilitate the persistence and execution of the backdoor. What is the path and name of this file?
We can do the basic check for persistence. With this filter, we can see all the files inside the .\Users\susan\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup. Yes, I know I am a lazy cheek for this filter don’t blame me.
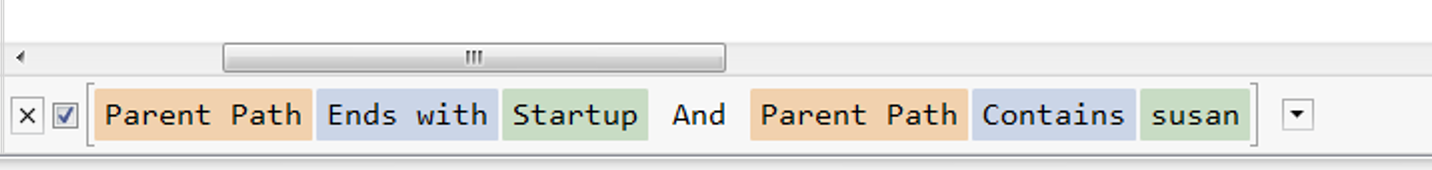
With this beautiful filter, we can admire the Display Settings.lnk that has been created during the extract of the archive (2025-09-02 08:14:18)
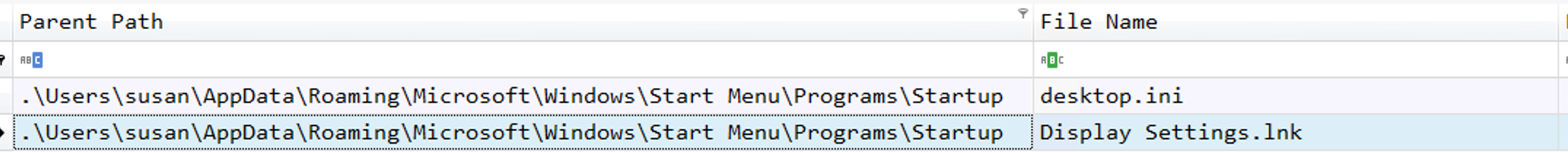
Moreover, in Timeline Explorer we can see that the Display Settings.lnk is just between the Genotyping_Results_B57_Positive.pdf and the ApbxHelper.exe which can leads us to think that the .lnk file is a shortcut for ApbxHelper.exe.
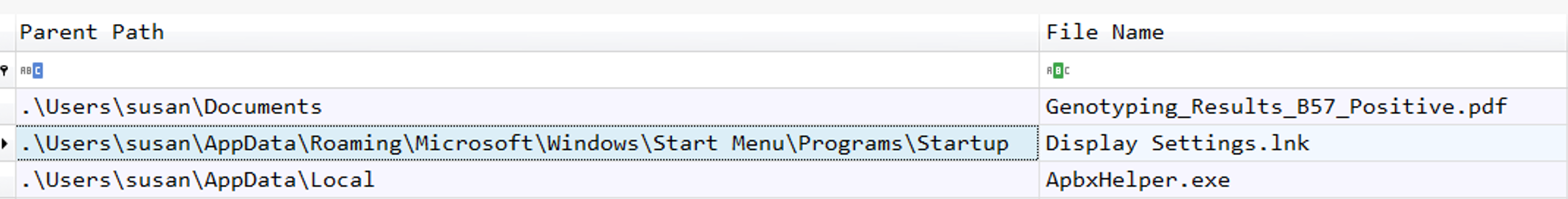
C:\Users\susan\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Display Settings.lnk
9. What is the associated MITRE Technique ID discussed in the previous question?
With a simple Google search we can find that the parent MITRE ATT&CK technique is T1547 (Boot or Logon Autostart Execution) and the final MITRE Technique is # Boot or Logon Autostart Execution: Shortcut Modification (T1547.009)
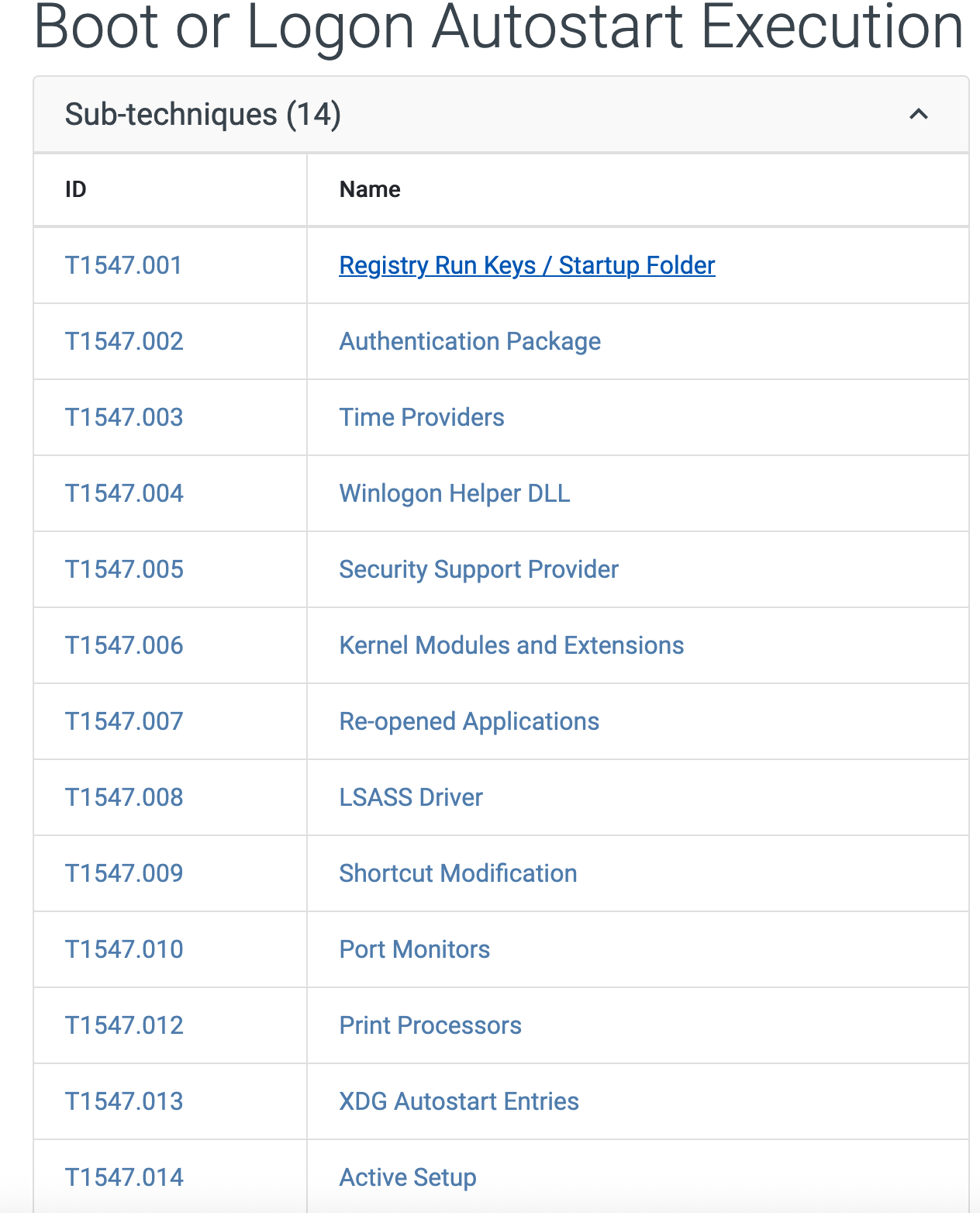
T1547.009
10. When was the decoy document opened by the end user, thinking it to be a legitimate document?
As we know, the decoydocument seems to be Genotyping_Results_B57_Positive.pdf. We now just have to check the Last Accessfield:
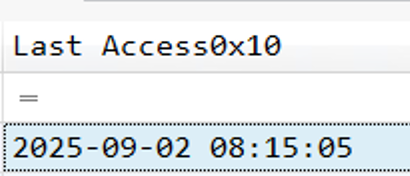
2025-09-02 08:15:05